SOLUTION SHEET
CyberStrong Risk Hub Overview
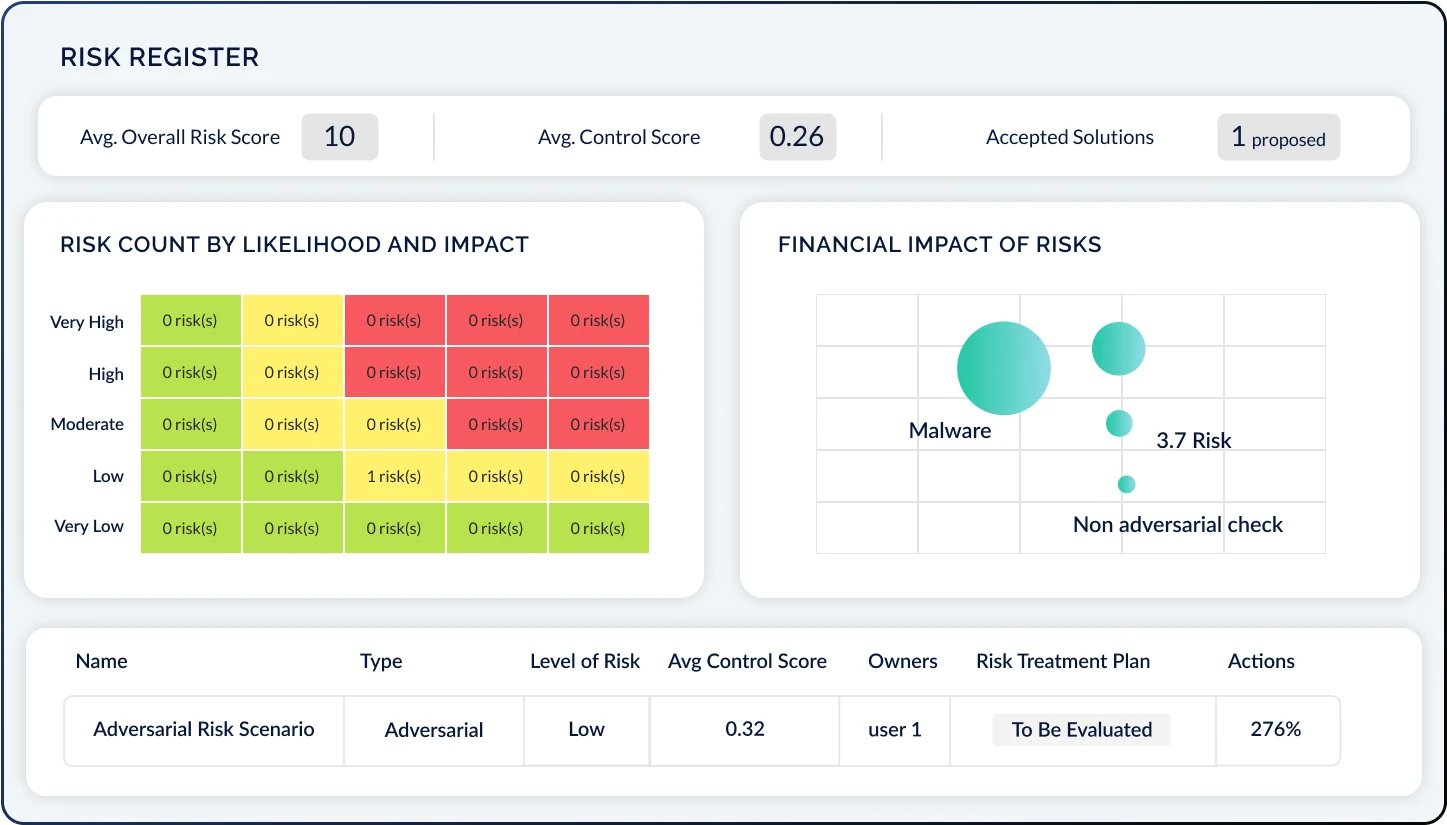
The CyberStrong Risk Hub empowers organizations to master their dynamic cyber risk posture through a data-driven approach. It enables comprehensive cyber risk management by allowing you to:
- Identify Cyber Risks: Benchmark against peers to understand and improve your cyber risk posture.
- Implement Cyber Risk Quantification: Use models like FAIR and NIST 800-30 for strategic risk management discussions.
- Translate Risks into Financial Metrics: Convert cyber risk data into financial terms for clearer decision-making across teams.
Please fill out all form fields.
Related Resources
Discover the essentials of cyber risk management and enhance your expertise

Cybersecurity GRC Tools RFI Template

Key Takeaways from Forrester’s Cyber Risk Quantification Solutions Landscape





