How It Works
The CyberStrong platform optimizes organizations’ cyber risk posture by automating assessments, financializing risks, and informing decisions at the executive level
The CyberStrong Journey
CyberSaint customers benefit from a continuous, dynamic, and data-driven approach to cyber risk management, ensuring future-proof adaptability and resilience
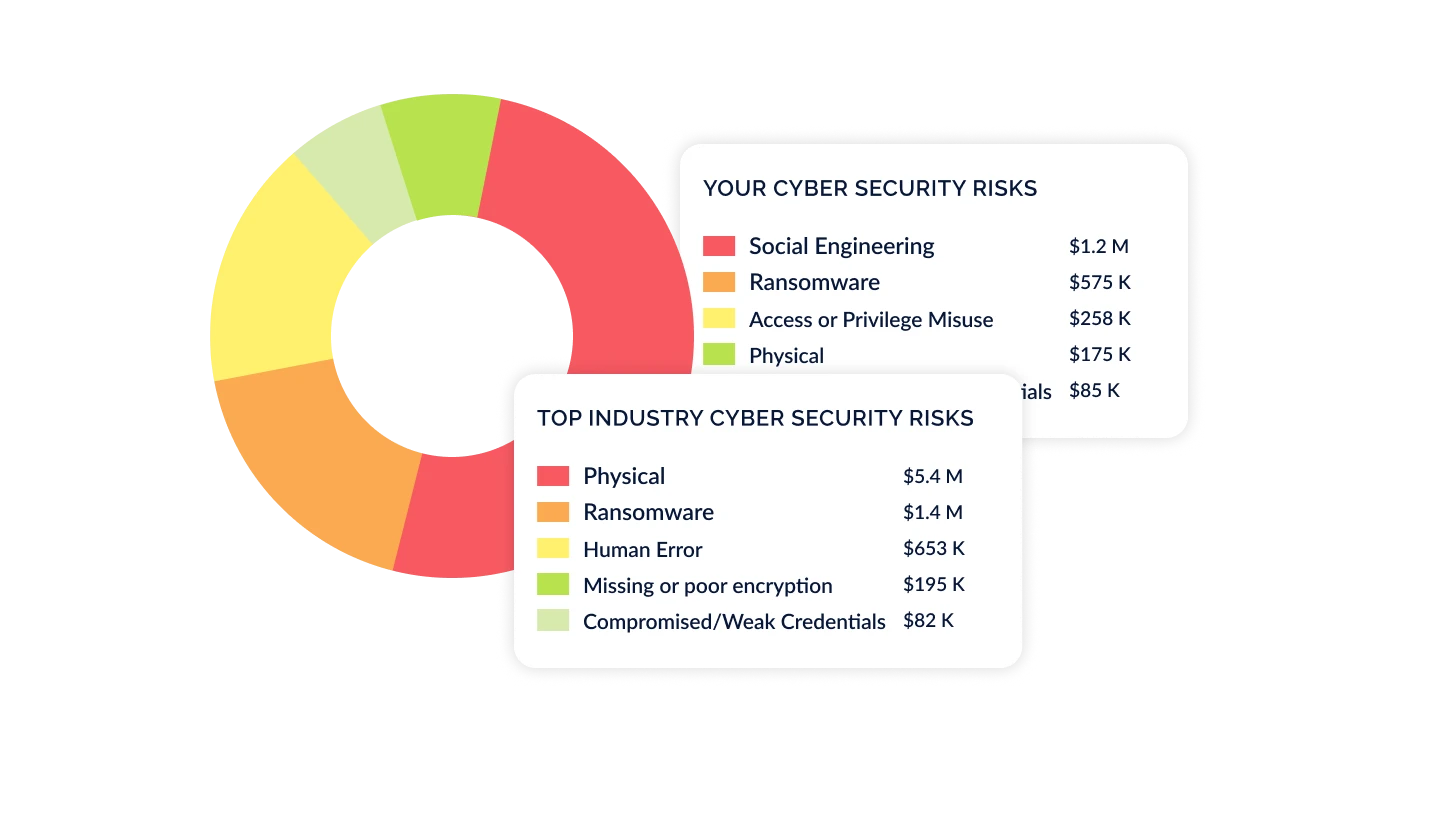
Identify & Benchmark Your Industry Risks
Based on your industry, revenue, and employee size, understand the top risks faced by your industry peers. These inherent risks help you prioritize which risks are most important to address.
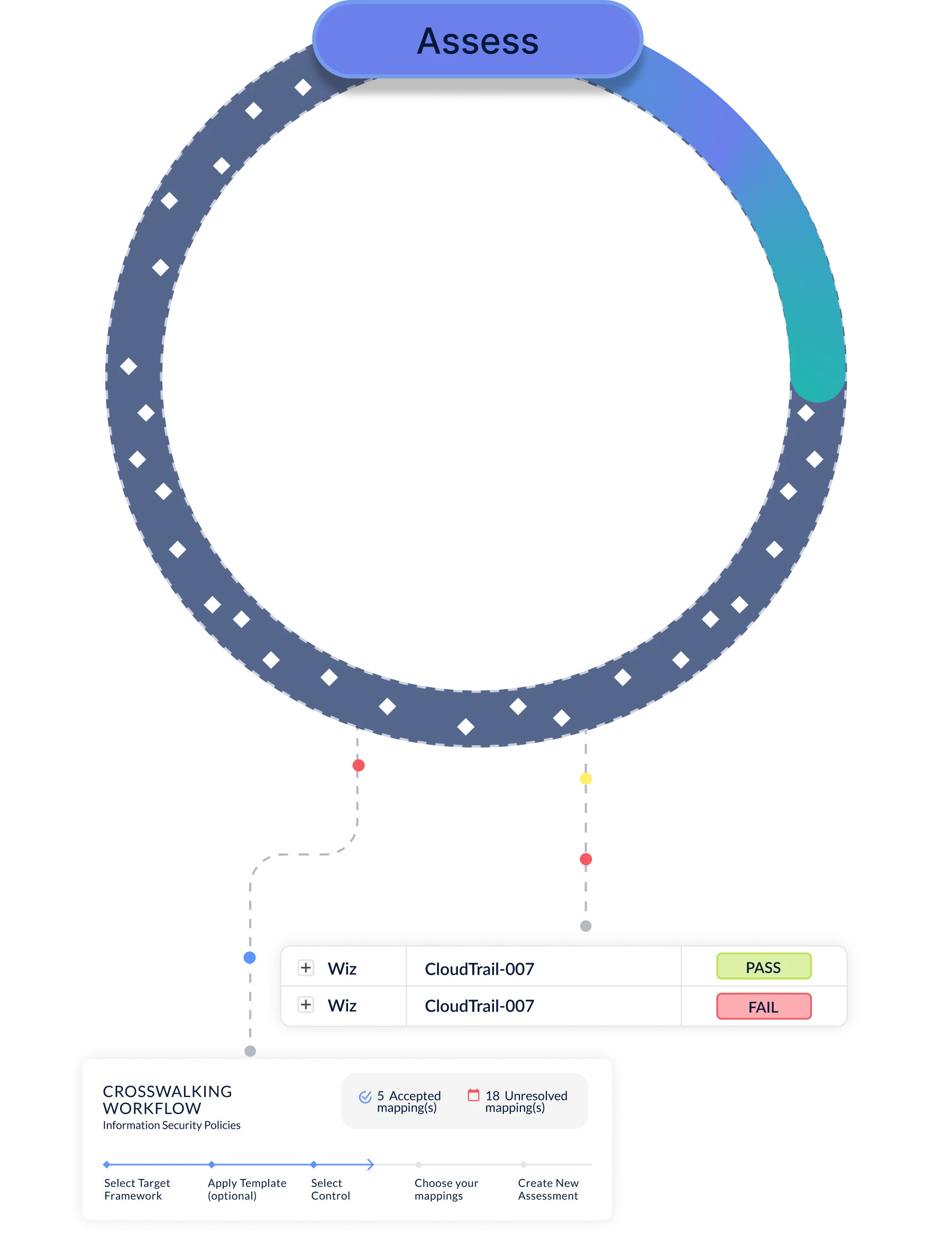
Automate Assessments from the Top-Down Based on Your Risks
Use your top Industry Risks to prioritize your control assessment. CyberStrong has already done the mapping for you, allowing you to quickly assess your top controls to measure maturity and identify gaps. Turn on Continuous Control Monitoring and Agentic Evidence Collection to make your assessment update in real-time, and use AI-powered crosswalking to map multiple frameworks, allow you to "assess once, use many".
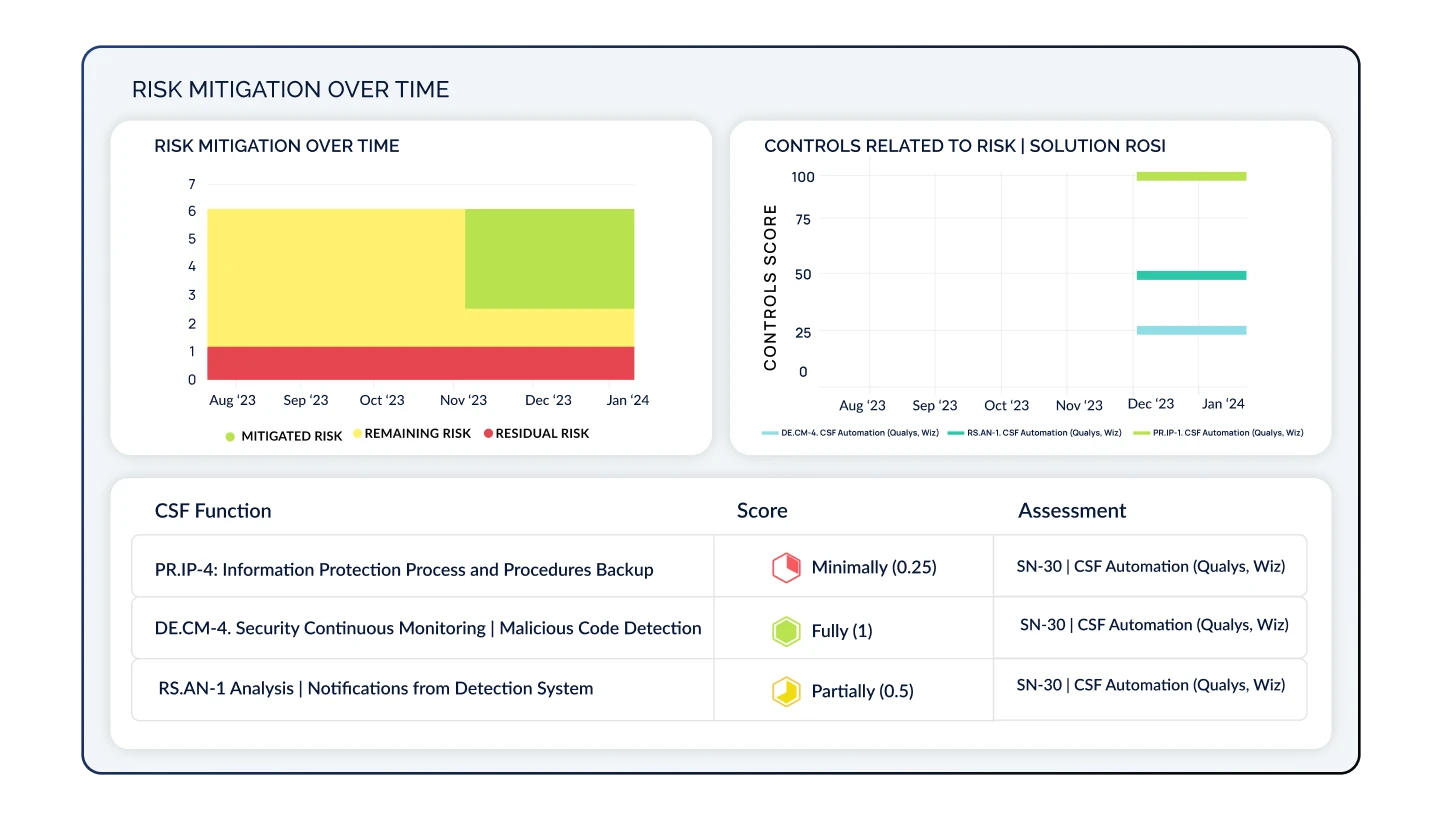
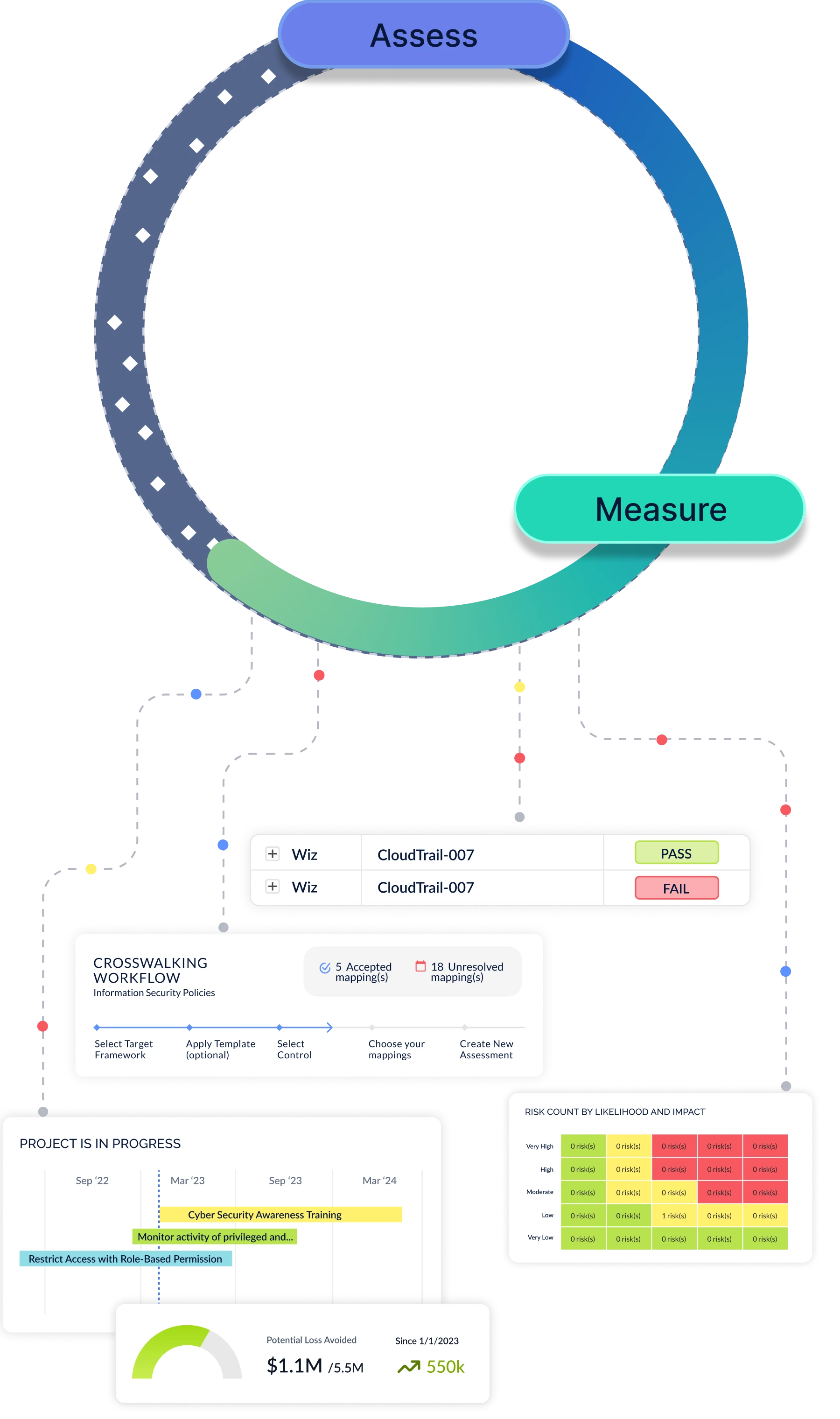
Quantify Your Risk Posture with Credible Risk Models
Continuously re-evaluate your cyber risk posture by automatically updating your residual risk score through NIST 800-30 or FAIR risk models. Compare your residual risk with the inherent risk of your industry peers to prioritize remediation activities while accounting for financial impact.
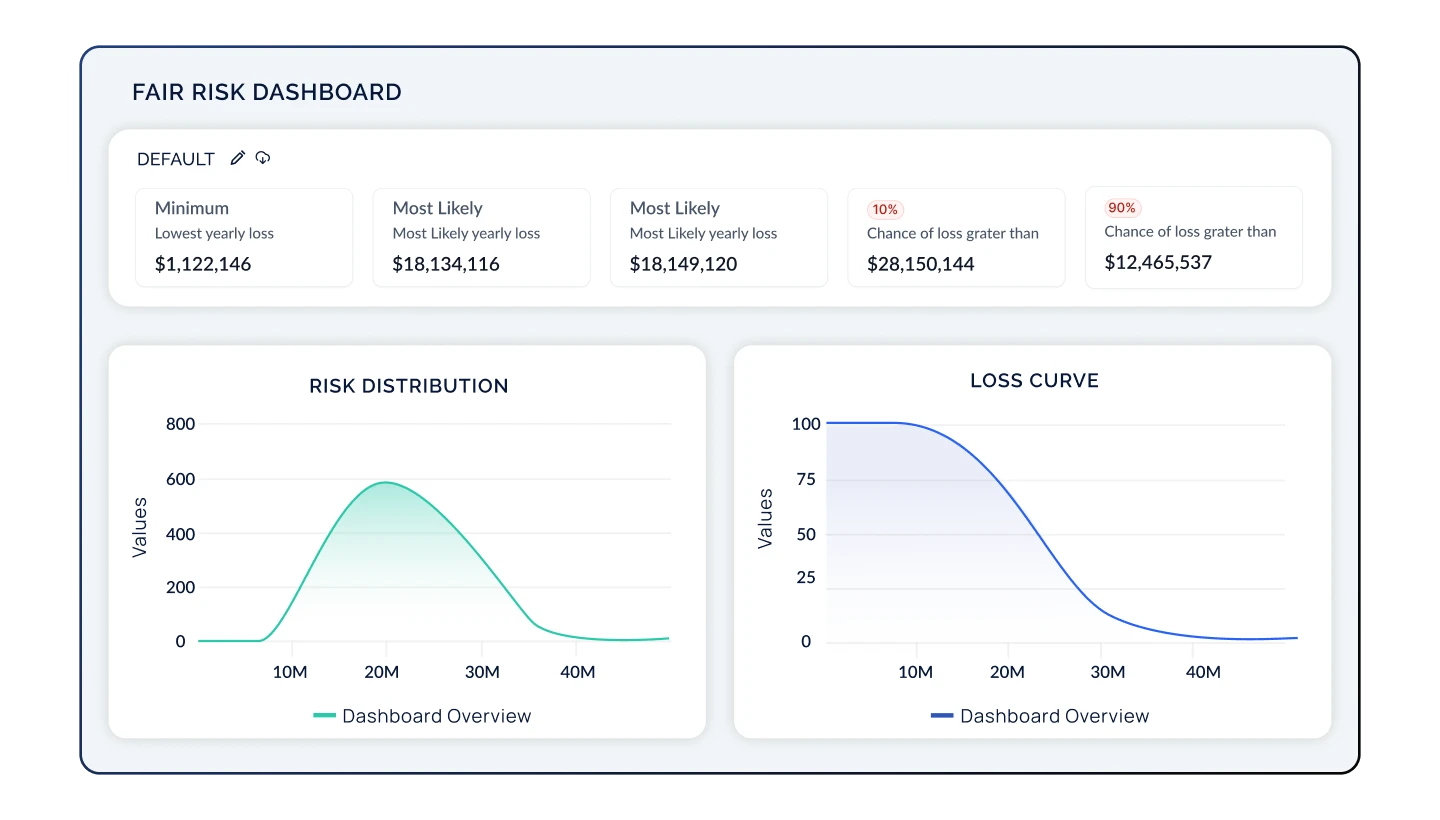
Communicate Your Risk Posture in Financial Terms
Quantify risk into terms that your board understands: dollars and cents. By displaying your cyber risk posture in financial terms, your Executive team will understand the potential losses associated with your top risks, their likelihood, and the positive impact of cyber initiatives, allowing you to secure investments to reduce your cyber risk exposure.
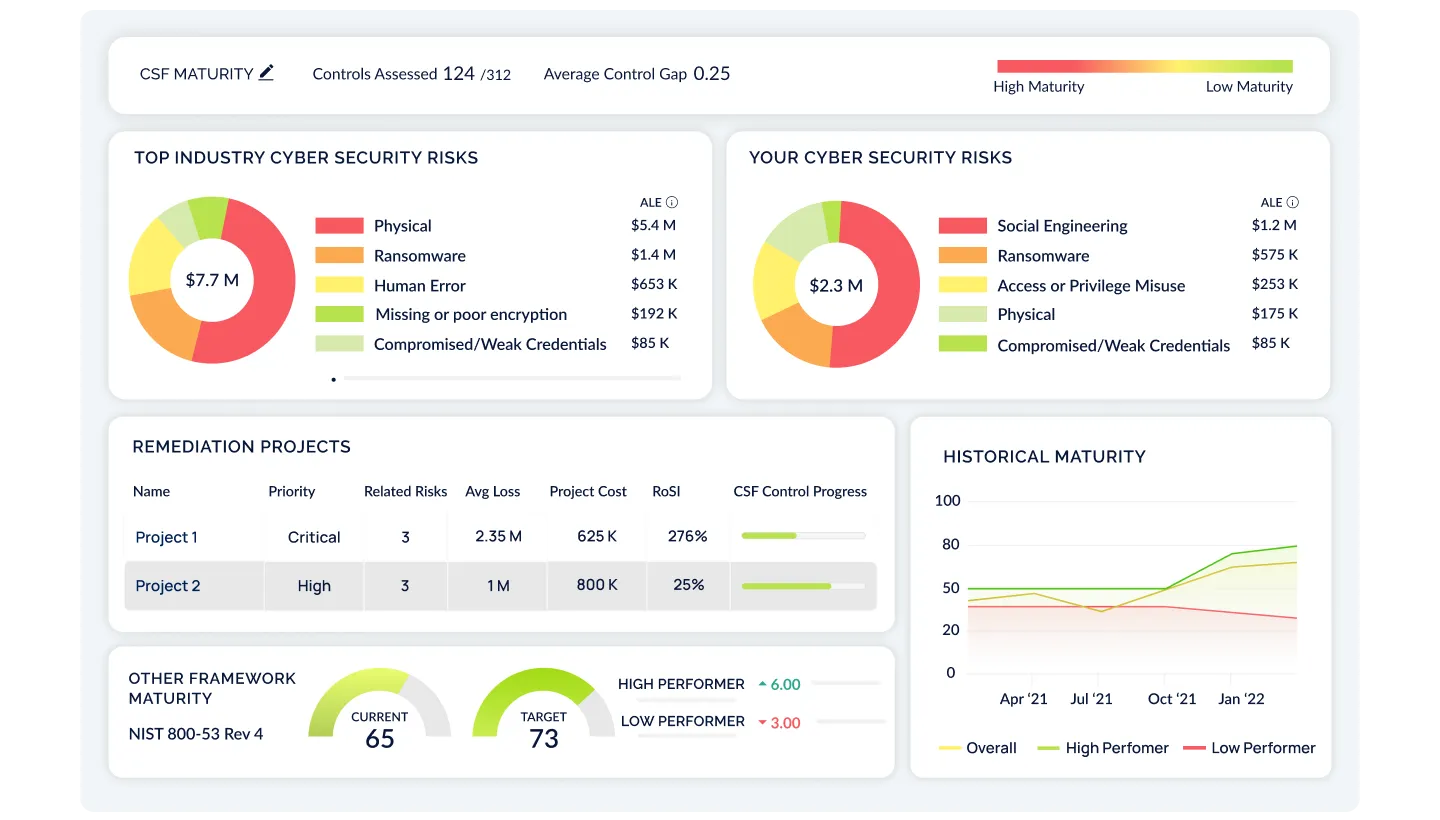
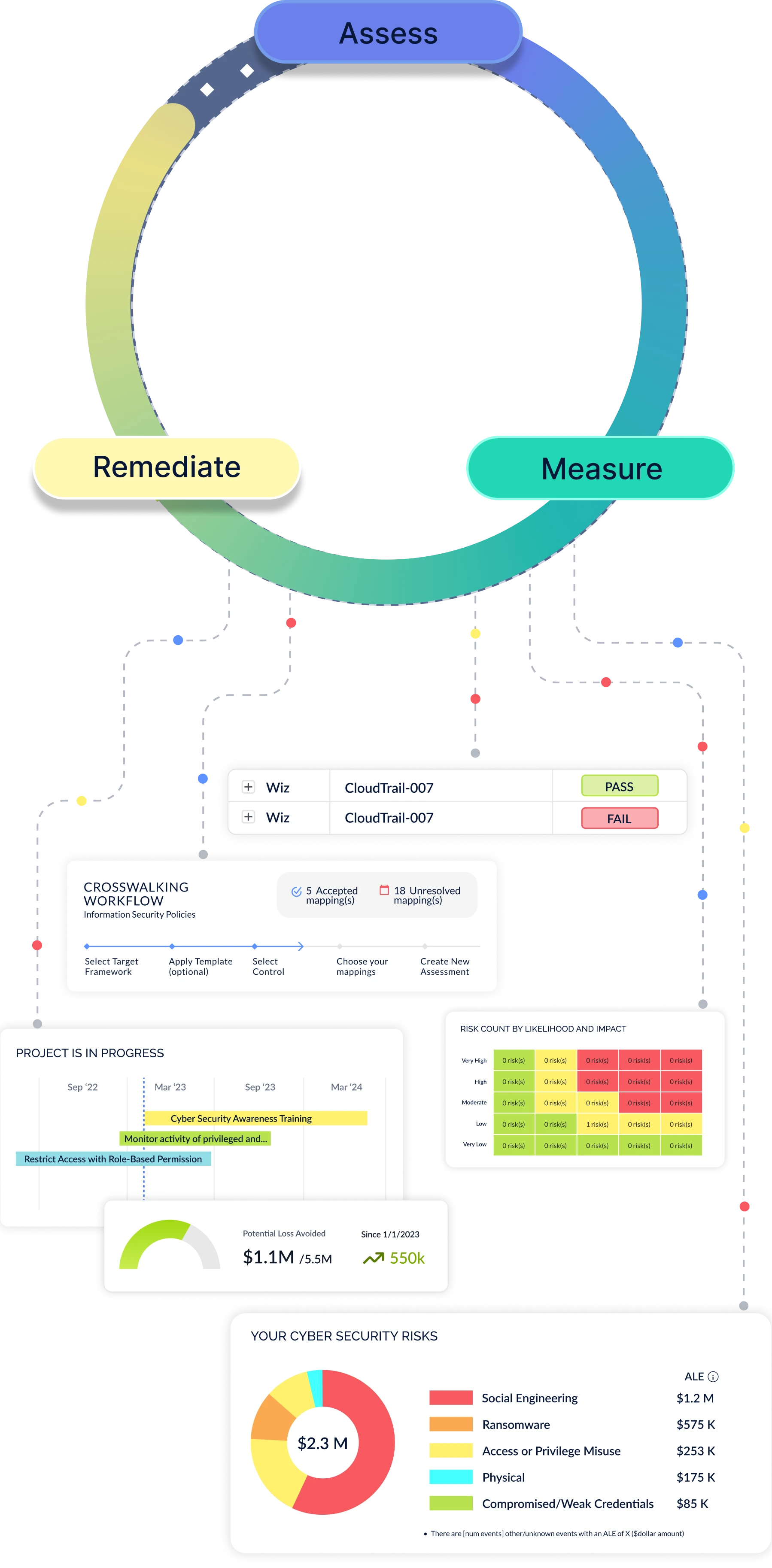
Develop, Prioritize, and Track Remediation Plans
Now that you have a list of prioritized gaps and resources, develop remediation projects and measure the Return on Security Investment (RoSI) on your initiatives. Track project costs, risk reduction, and financial impact mitigated for all your cyber risks.
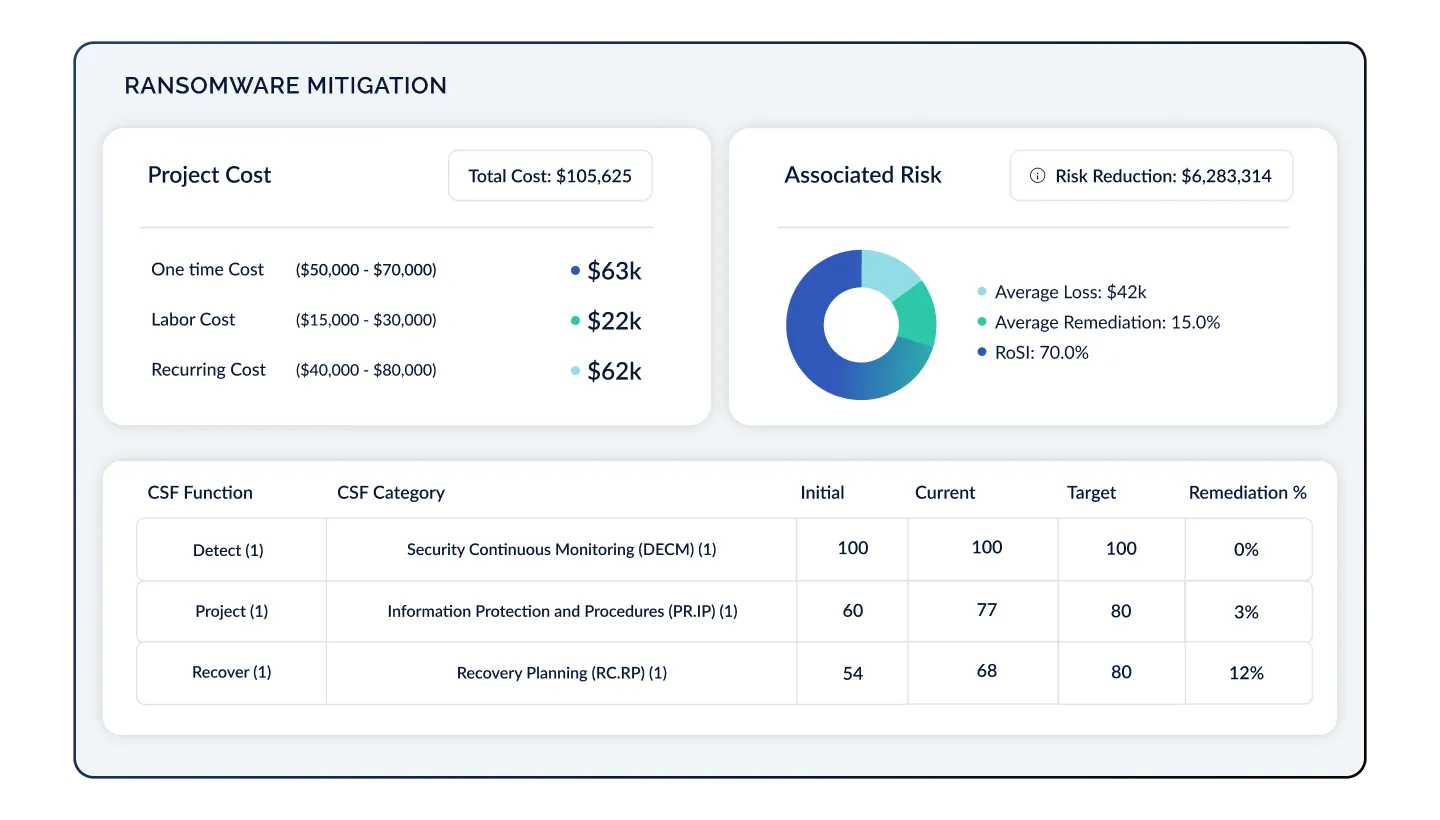
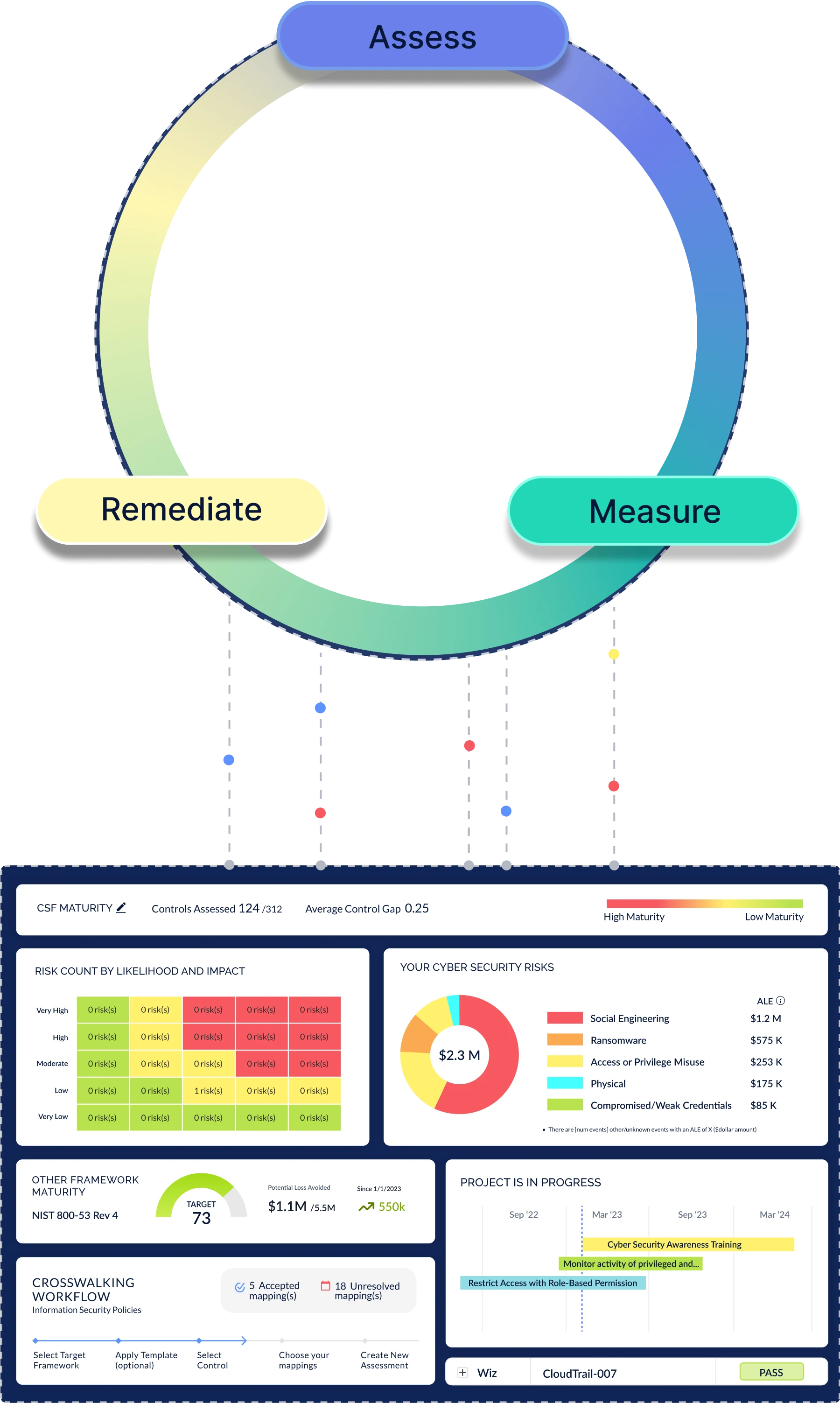
Optimize Your Cyber Risk Posture As Your Program Evolves
Continually track your risk progress through your remediation efforts. As top risks enter into acceptable levels, continually add additional risks and controls to your program. This approach creates a prioritized cyber risk management program that matures over time.
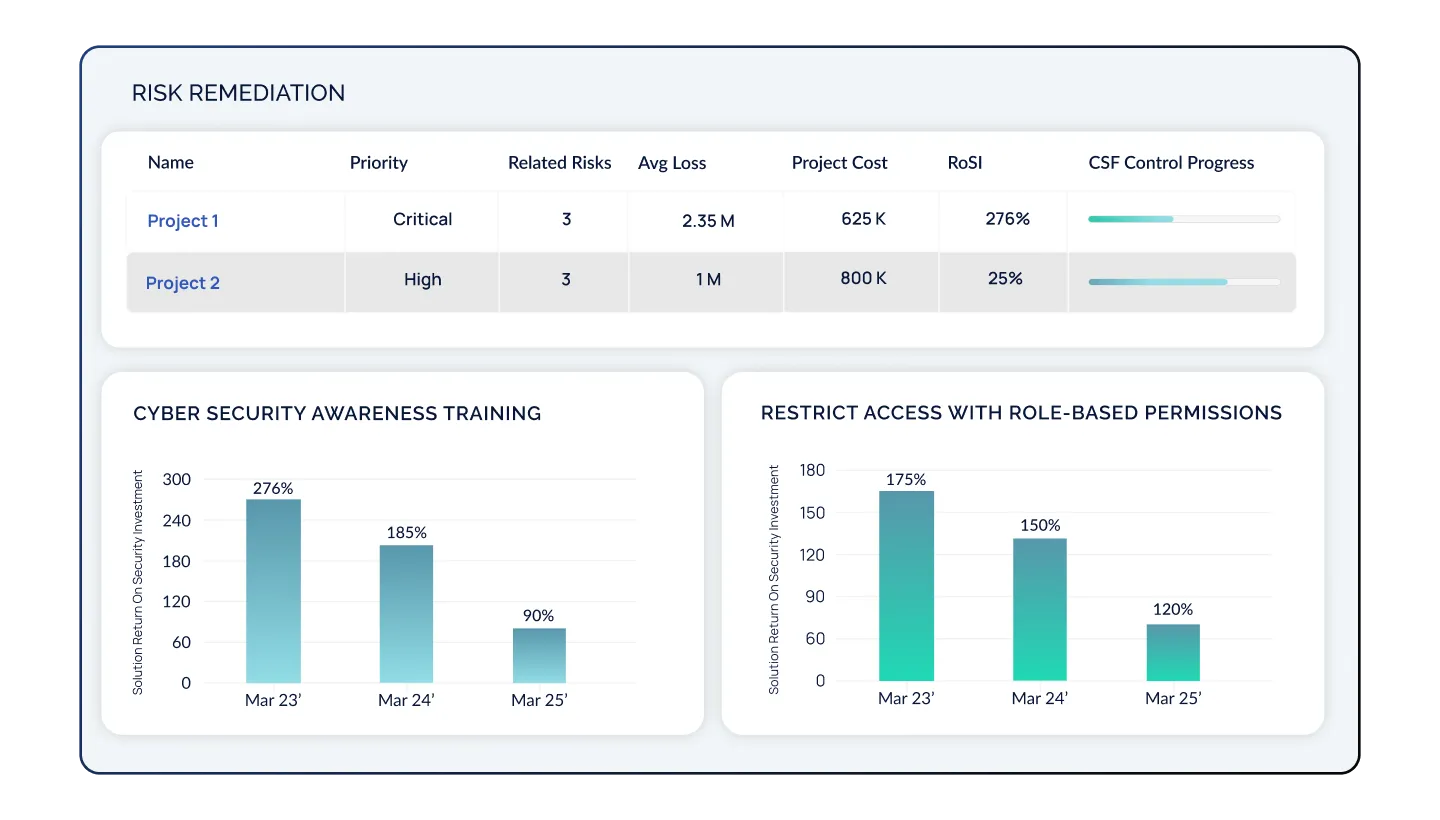
Identify & Benchmark Your Industry Risks
Based on your industry, revenue, and employee size, understand the top risks faced by your industry peers. These inherent risks help you prioritize which risks are most important to address.

Automate Assessments from the Top-Down Based on Your Risks
Use your top Industry Risks to prioritize your control assessment. CyberStrong has already done the mapping for you, allowing you to quickly assess your top controls to measure maturity and identify gaps. Turn on Continuous Control Monitoring and Agentic Evidence Collection to make your assessment update in real-time, and use AI-powered crosswalking to map multiple frameworks, allow you to "assess once, use many".

Quantify Your Risk Posture with Credible Risk Models
Continuously re-evaluate your cyber risk posture by automatically updating your residual risk score through NIST 800-30 or FAIR risk models. Compare your residual risk with the inherent risk of your industry peers to prioritize remediation activities while accounting for financial impact.

Communicate Your Risk Posture in Financial Terms
Quantify risk into terms that your board understands: dollars and cents. By displaying your cyber risk posture in financial terms, your Executive team will understand the potential losses associated with your top risks, their likelihood, and the positive impact of cyber initiatives, allowing you to secure investments to reduce your cyber risk exposure.

Develop, Prioritize, and Track Remediation Plans
Now that you have a list of prioritized gaps and resources, develop remediation projects and measure the Return on Security Investment (RoSI) on your initiatives. Track project costs, risk reduction, and financial impact mitigated for all your cyber risks.

Optimize Your Cyber Risk Posture As Your Program Evolves
Continually track your risk progress through your remediation efforts. As top risks enter into acceptable levels, continually add additional risks and controls to your program. This approach creates a prioritized cyber risk management program that matures over time.

.png)
Powered by CyberSaint AI
Curious how we're automating cyber risk management at enterprise scale? It's not just APIs and workflow. Book a demo to see real automation at work.
The CyberStrong Platform Architecture
Designed to continuously assess, measure, remediate, and communicate cyber risk enterprise-wide, taking into account new security data, additional controls, and newly identified risks as your program matures
You're Sitting on a Goldmine — Let's Use It
Frameworks, Assessments & Controls
Cyber Risk Quantification & Risk Tracking
Findings, Risk, & Control Remediation
Executive Insights for the C-Suite & Board
CyberStrong Differentiators
Transition from manual processes to automation, replace black-box scoring with transparent and credible models, and consolidate point solutions into a single, unified platform
AI-Powered
We've been innovating in Artificial Intelligence and Machine Learning since inception, and built our platform on patents that were approved starting in 2019.
Immediate Value
CyberStrong delivers immediate insights into customers' cyber risk posture, and most customers are active in system within one week or less.
Credible CRQ
We've humanized cyber risk quantification and mapped cyber risk to metrics that CFOs, CEOs, and Boards are already asking for and can understand.
Powerful Automation
Use Continuous Control Monitoring and Agentic Evidence Collection to automate control scoring and evidence validation, moving from point-in-time assessment to real-time. Plus, automate crosswalking as new frameworks come into play use data in one assessment to meet controls in another.
Holistic Approach
Move beyond reporting on framework compliance, risks, cyber events, and remediations in silos. CyberStrong connects controls directly to risk register entries and links risks to investments, providing a precise snapshot of your cyber risk posture.
Intuitive Platform
Cyber risk is complex, but the solution is simple. Tailored for scalability and efficiency, the platform ensures seamless navigation and quick access to every feature. We've minimized the learning curve, training up users within days of onboarding.
FORTUNE 500 CASE STUDY
Quantify Risk. Prioritize Gaps. Reduce Cyber Risk Exposure.
After a 2022 ransomware attack, the CISO needed a solution to serve as the foundation of their new cyber risk management program. The team wanted to track the potential financial loss and impact of cyber risks, prioritize actions, and unlock budget. CyberStrong allowed them to:
- Build the foundation of their program off of NIST SP 800-171, CMMC, and the NIST CSF with the ability to add other frameworks
- Transition from a spreadsheet-based risk register to a centralized, quantifiable NIST 800-30 risk register for credible cyber risk quantification
- Use cyber risk presets to map threats to MITRE TTPs, enhancing risk prioritization by linking TTPs directly to controls
- Empower the CISO with a scalable, data-driven solution to spur action and influence decisions





