TRUSTED BY INDUSTRY LEADERS
Expect More From Your Automation
Turn millions of security data points into insights, backed by our patented Graph Neural Net engine
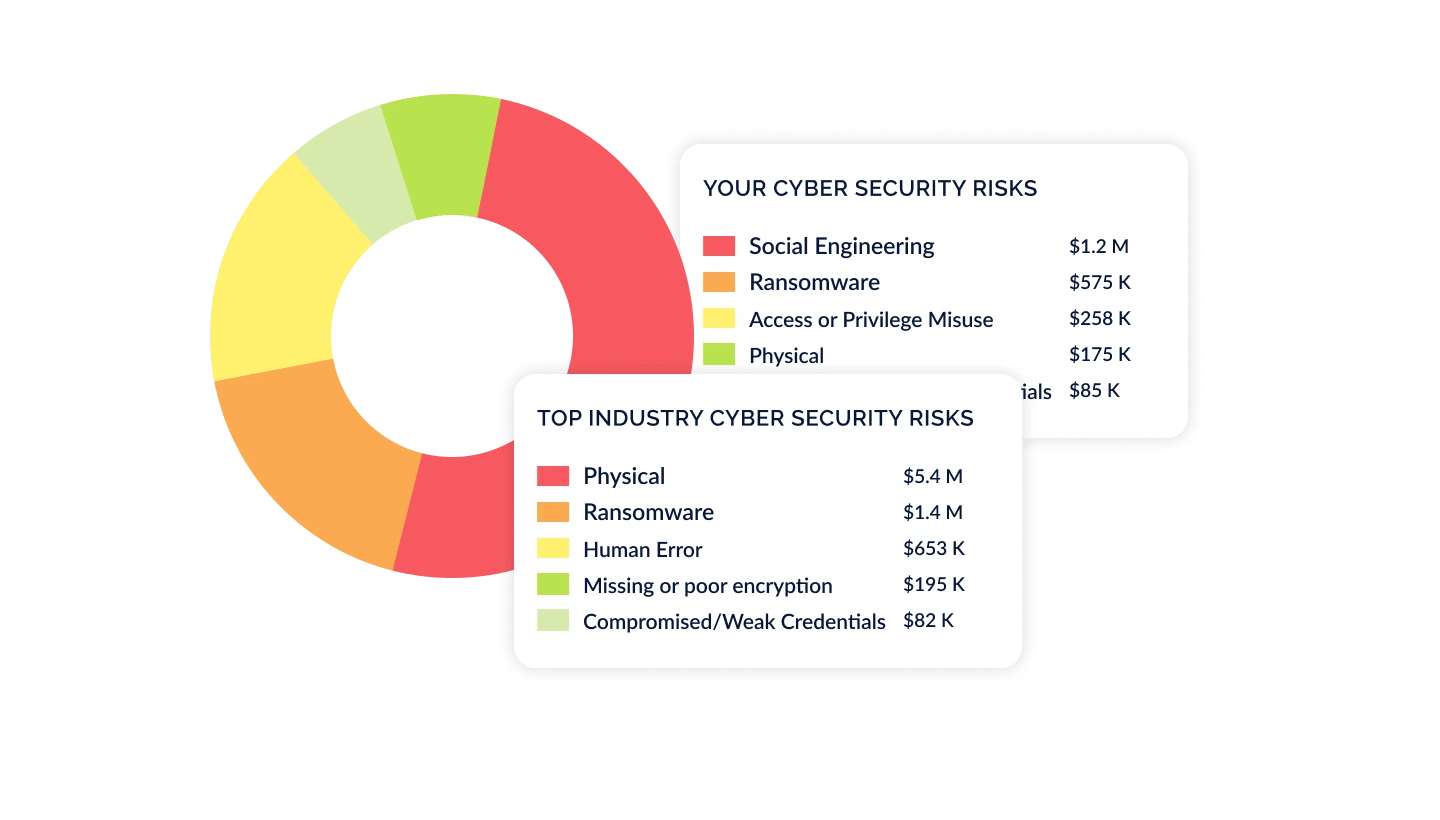
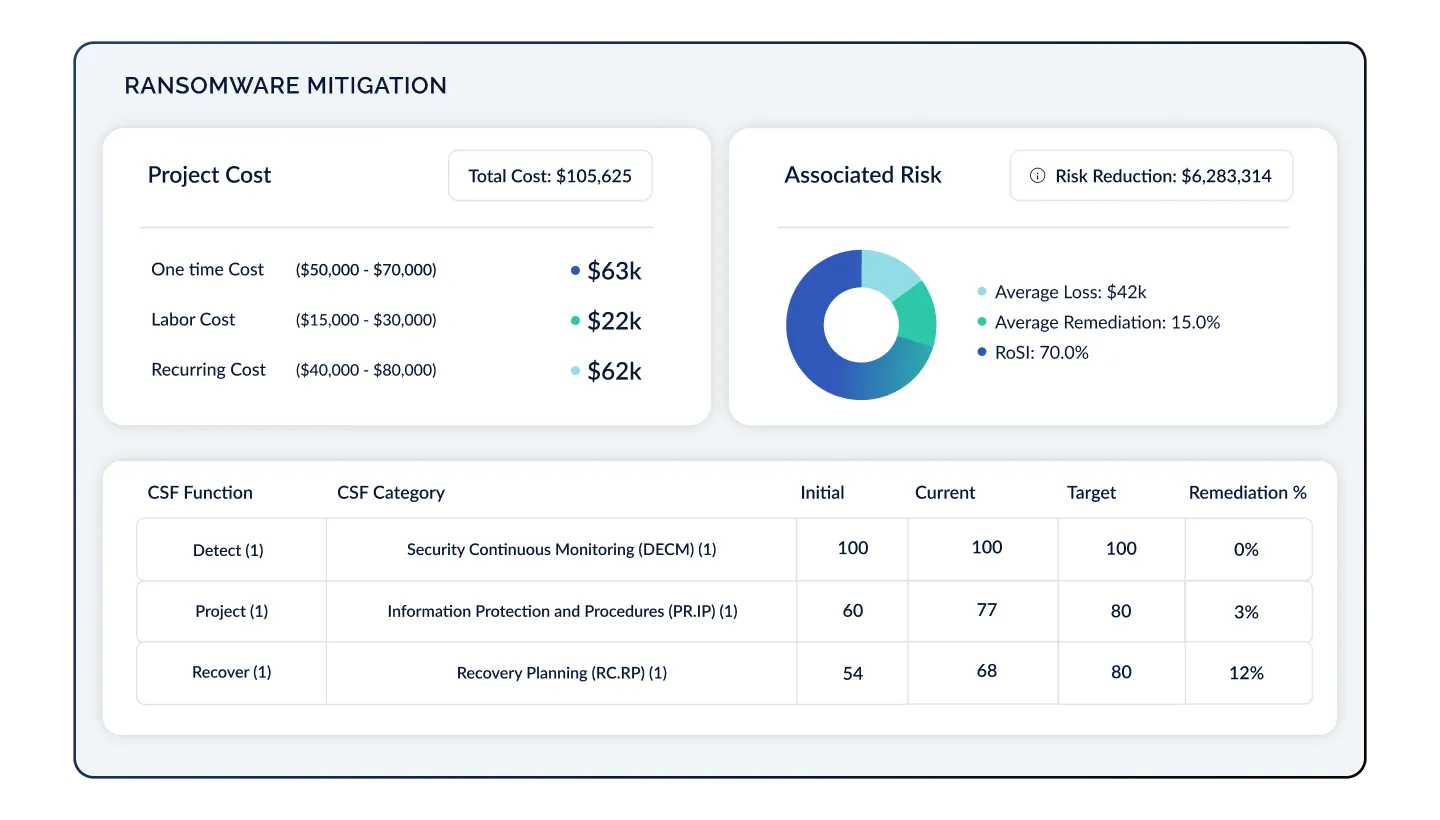
Quantify Cyber Risk in Financial Terms
Leveraging your risk and compliance posture, present cyber risk initiatives in a way that's transparent and understandable to executives, boards, and regulators. Showcase how security contributes to the bottom line by translating cyber risk into dollars and cents backed by defensible, transparent models like FAIR, NIST 800-30 and others.
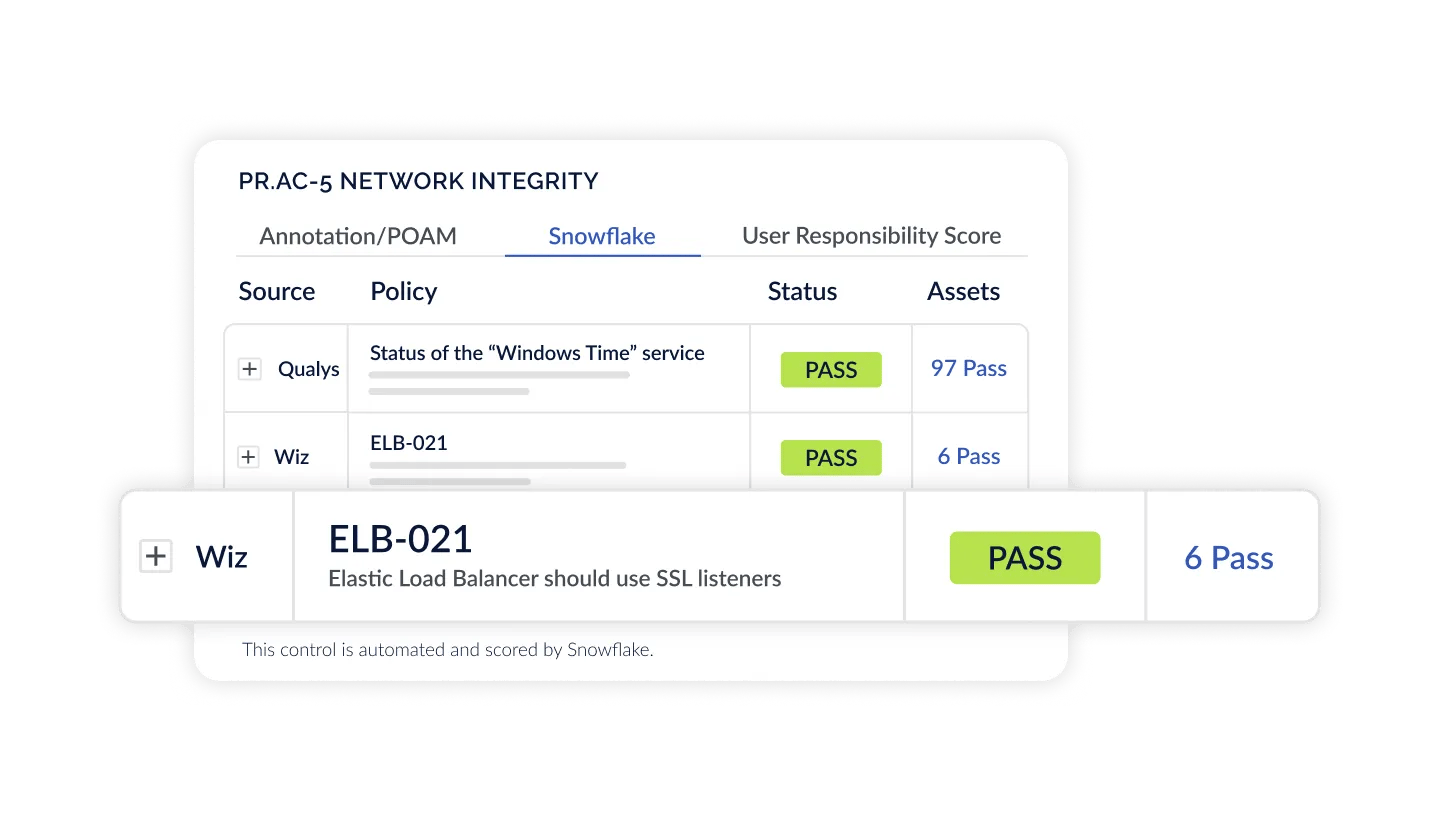
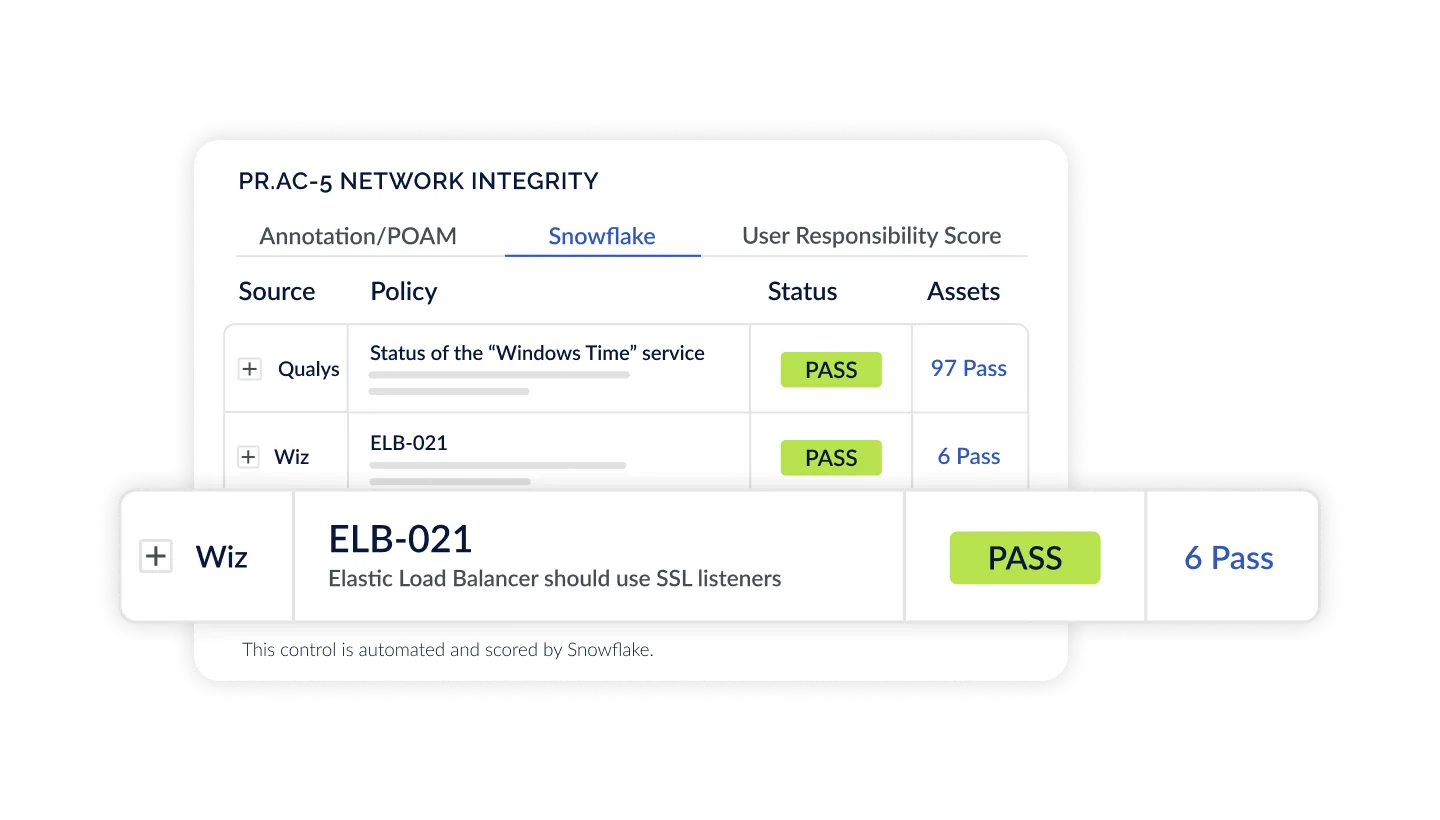
Automate Assessments at Enterprise Scale
Combine Continuous Control Monitoring and Agentic Evidence Collection to automate assessments like never before. Gain dynamic insight into your compliance posture and monitor controls across NIST, CIS, ISO, and any other standard. CyberStrong harmonizes frameworks to crosswalk control data across any regulation to give you complete visibility into your compliance posture, no matter the requirement.
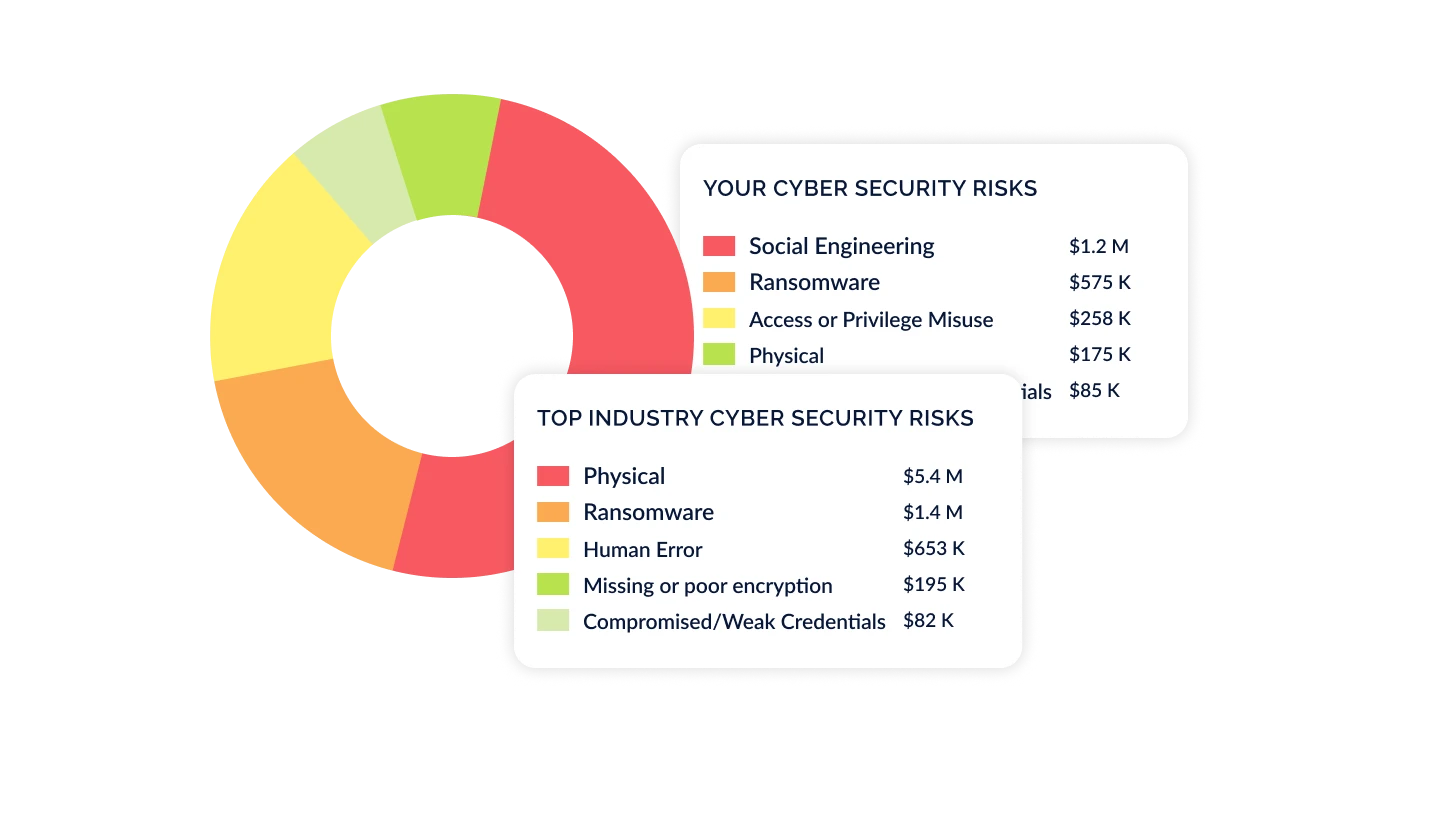
Identify & Prioritize Findings Based on the Complete Picture
Using CyberSaint’s AI-native approach, prioritize findings, risks, and remediation projects based on millions of internal and external signals. Allocate resources effectively to mitigate the risks that matter most to your organization without getting lost in the noise.
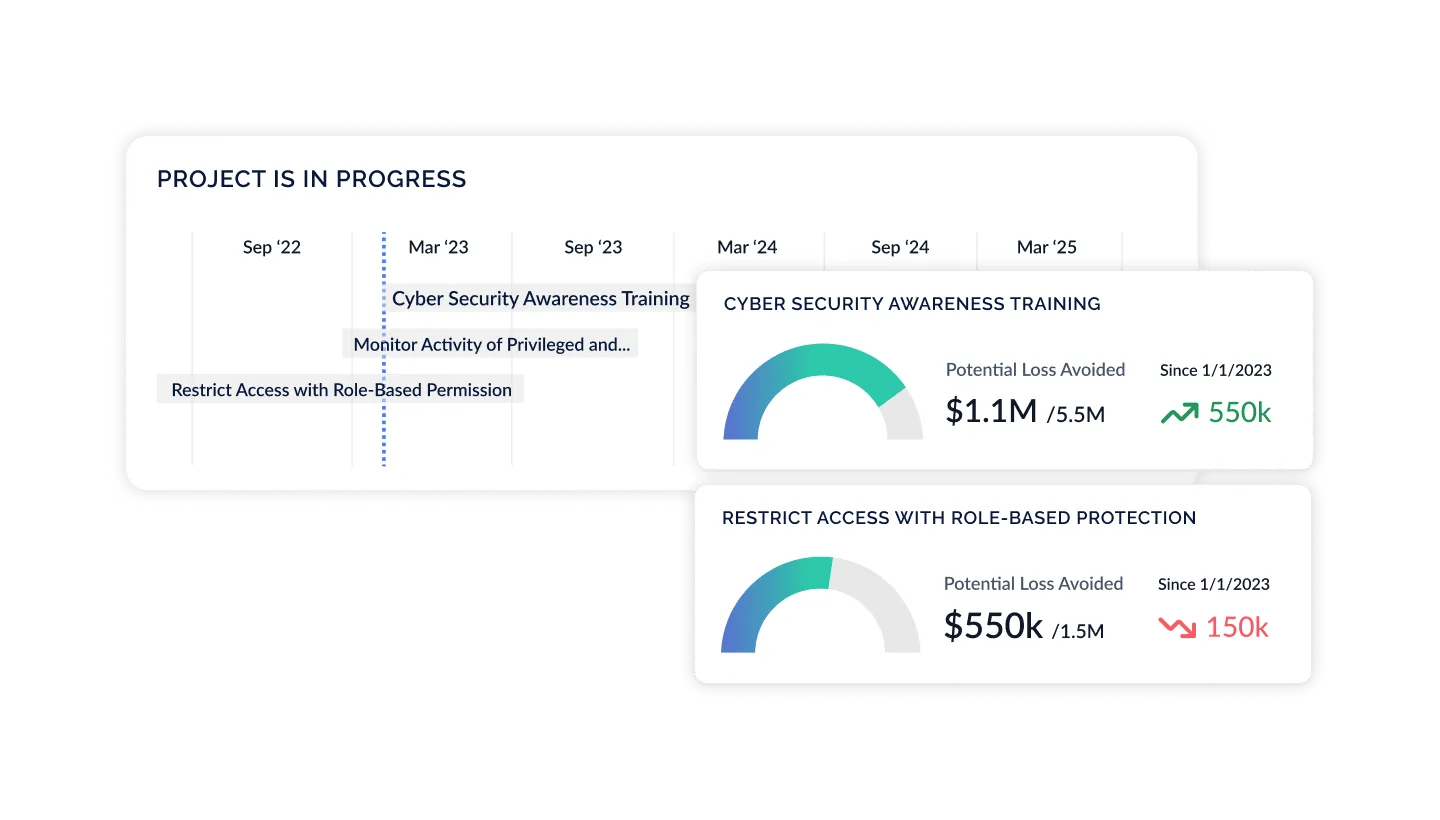
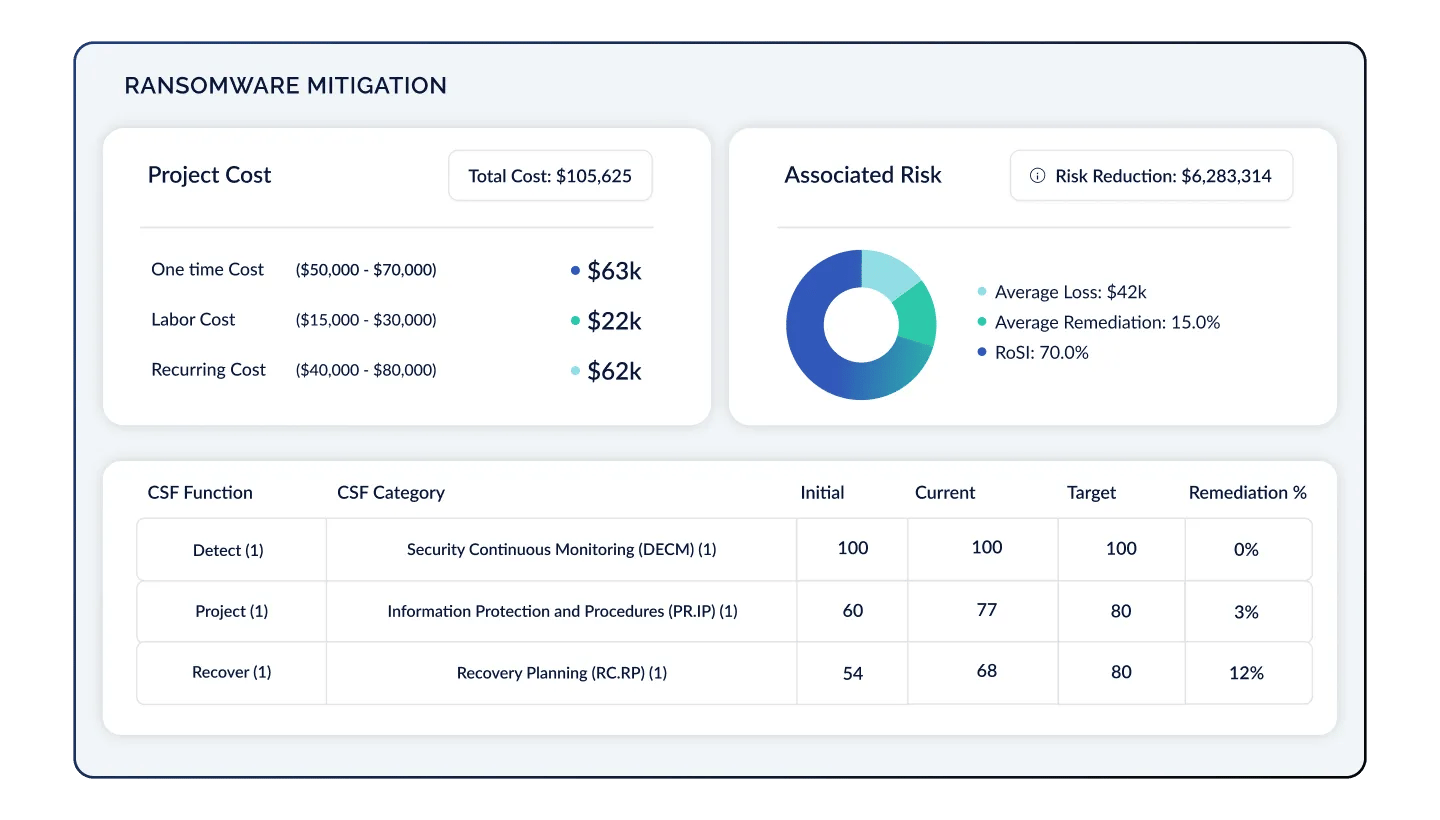
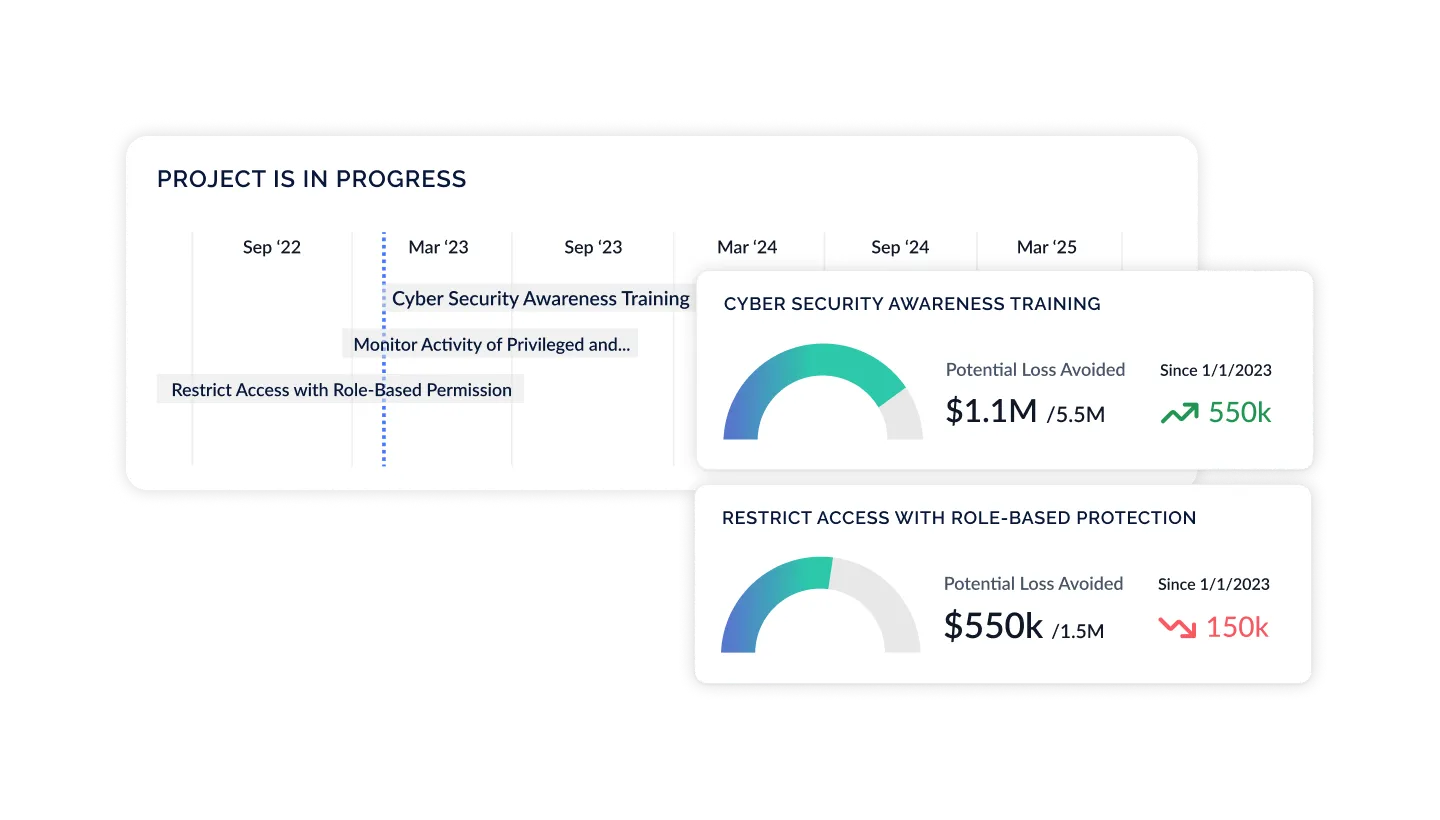
Present ROSI & Buy Down Risk
With a real-time, holistic view of your organization's cyber risk posture, update and refine your strategy over time based on dynamic data coming from your security environment, additional control frameworks, newly uncovered risks, and unlocked resources. Prioritize actions by assessing risk likelihood and impact, ROSI, and identify new opportunities to drive business value.
Prove Business Value with Effortless Transparency and Credible Insights
$ 0 T+
0 M+
$ 0 M+
Unlock Increased Value as Your Program Matures
CyberStrong is designed to grow with you. Get instant results by starting with the software package that aligns with your immediate needs and unlock functionality as your strategy evolves.
Compliance Hub
Risk Hub
Executive Hub
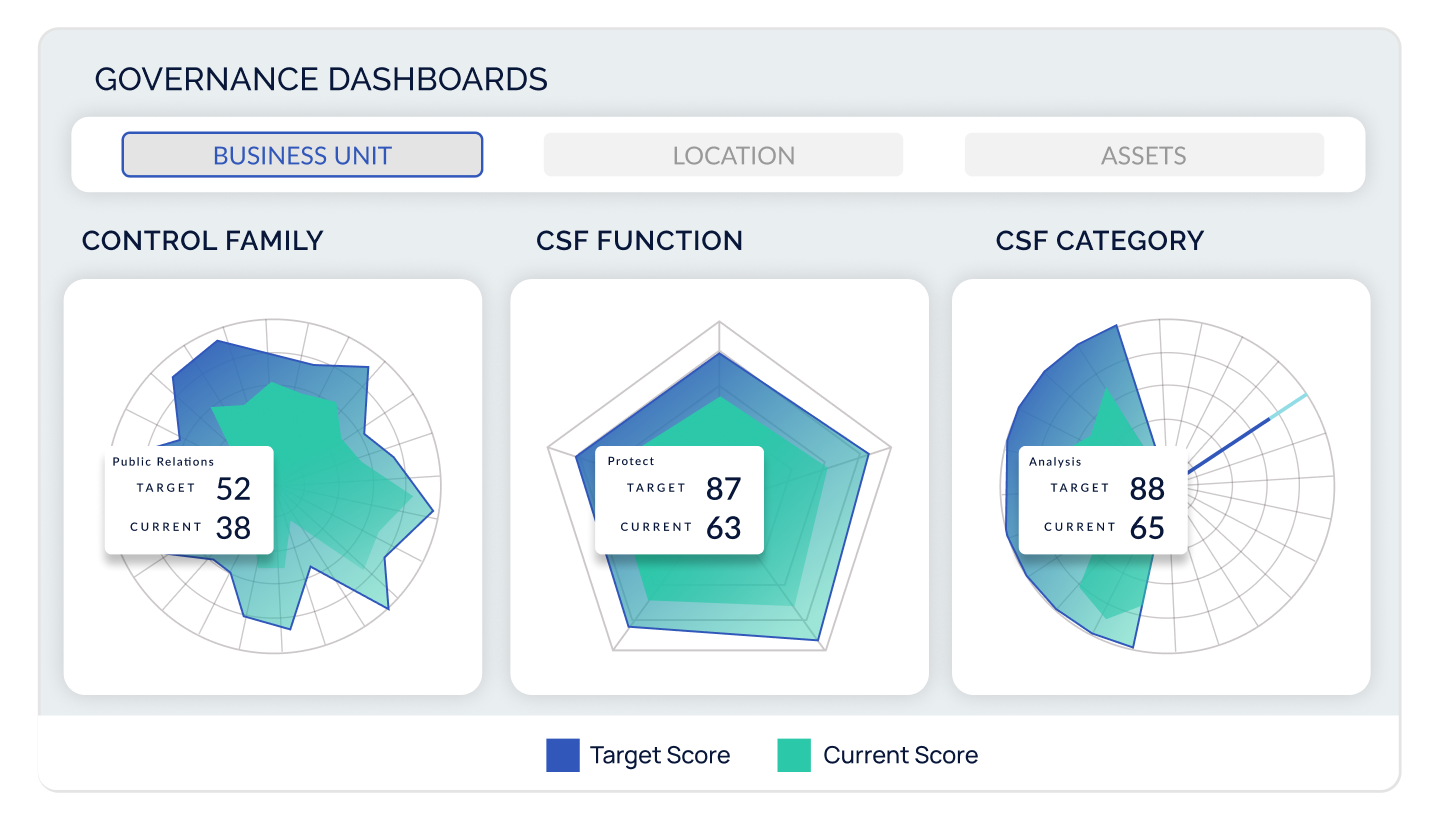
Compliance Hub
The most basic CyberStrong package, built to address risk-based compliance management.
- Uncover what top cyber risks impact your business, and use these insights to inform your control assessment strategy
- Access a flexible controls library, hundreds of frameworks, and perform assessments
- Harmonize frameworks with AI-powered automated crosswalking to "assess once, use many"
- Leverage flexible dashboards and reports to track trends over time, gap-to-goal analysis, and view compliance by geography, business unit, assets, and more
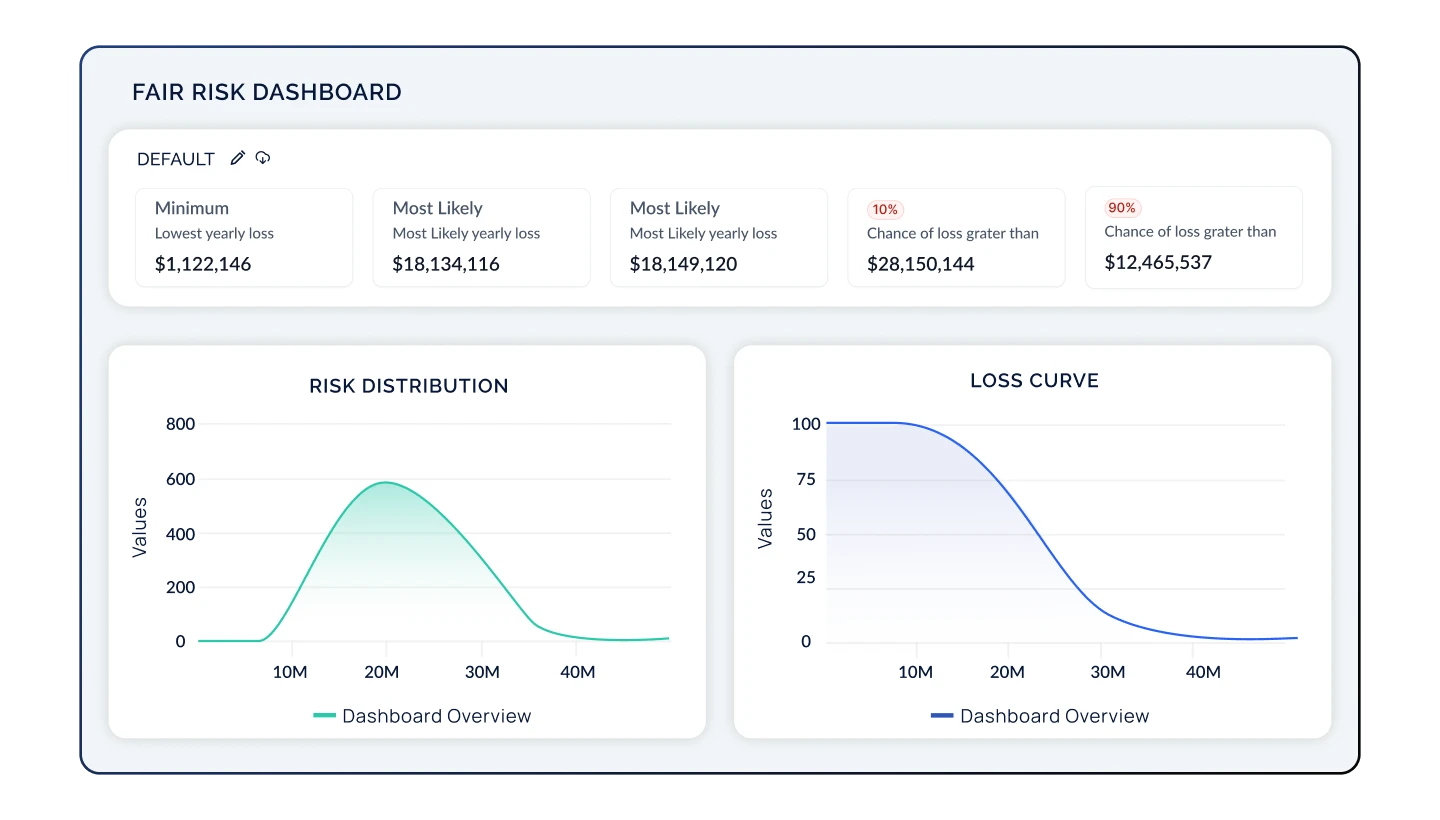
Risk Hub
Designed to connect the dots between controls, risks, and finance, the Risk Hub includes everything in the Compliance Hub plus the ability to:
- Tie control groups from assessments and frameworks you are already tracking to risks in an intuitive risk register
- Benchmark your top risks versus those of your peers based on industry, company size, and revenue
- Quantify risk into financial metrics with transparent models such as FAIR and NIST 800-30, designed for rapid implementation and scalability
- Customize heat maps, risk dashboards, and reports to view risk from any angle
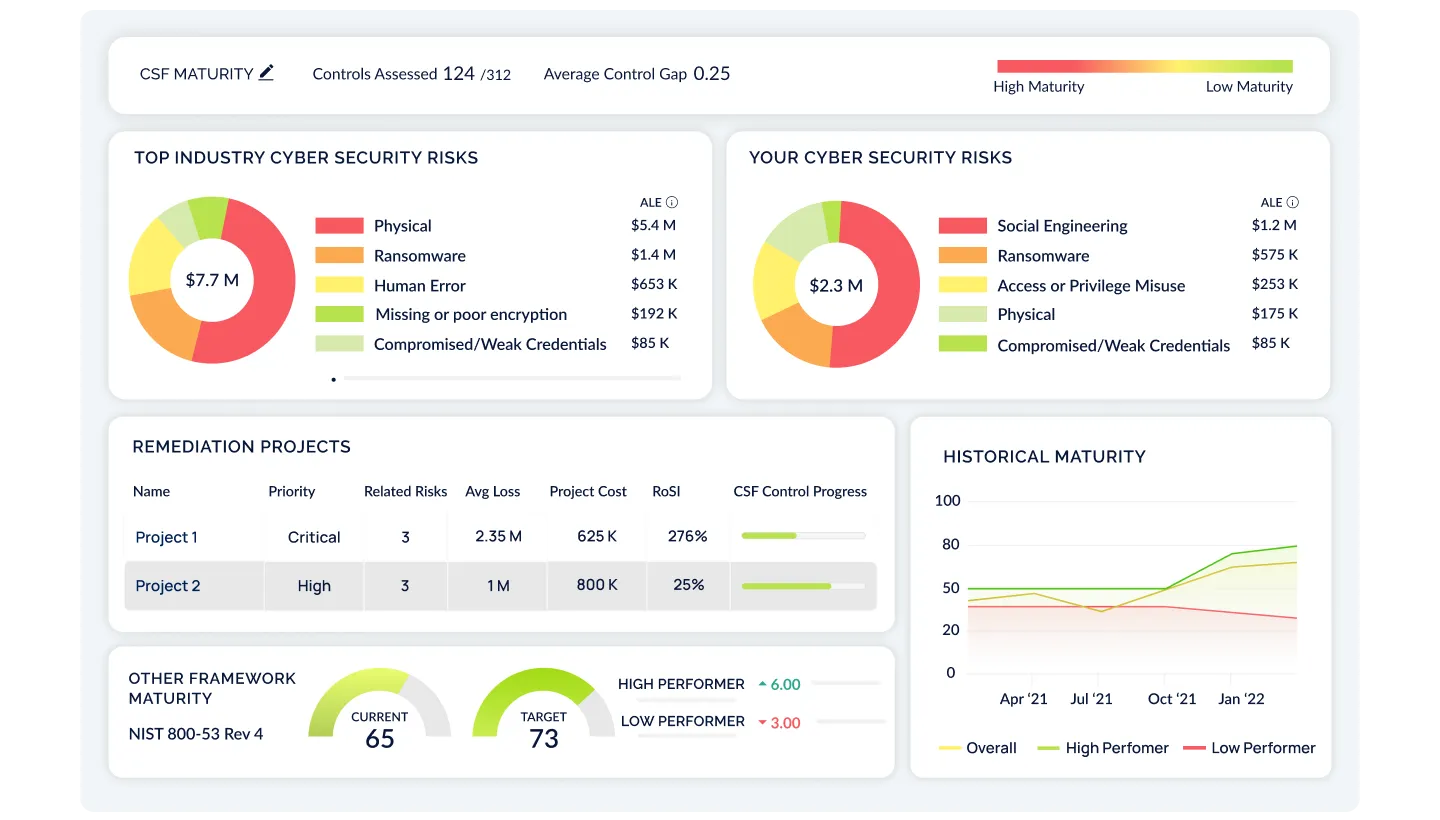
Executive Hub
Our most robust package, the Enterprise Hub elevates the cyber risk conversation. Leverage everything offered in the Risk Hub, plus the ability to:
- Present cyber risk initiatives in a business context, making complex cyber risk data accessible and understandable to non-technical stakeholders, regulators, and cross-functional teams, especially the C-Suite and Board
- Influence budgeting decisions by modeling out security investments with clear remediation project timelines, tracking, and ROI analysis
- Refine and optimize your cyber risk strategy as new controls or risks are added, uncovering new opportunities for risk remediation, budget unlock, and value creation on an ongoing basis
Becoming CyberStrong
The SEC requirements have elevated the conversation around cyber risk to the Boardroom. CyberSaint’s platform not only hits on the need for increased automation at the foundational compliance level, but also the need to link controls to risks to make cyber risk management real-time. Companies now can have a clear understanding of their cyber risk posture and optimize accordingly based on their most likely cyber losses, risk mitigated, and ROSI. Translating cyber risk into financial terms is a game-changer for C-suites and Boards, and CyberSaint has cracked the code on rapid time to value and scalability for enterprise cyber risk quantification. The CyberStrong platform is a powerful solution for every enterprise CISO looking to master their cyber risk posture.
We needed to get going quickly, manage our cybersecurity posture continuously, and measure where we are today against where we as a leadership team determined we wanted to go. Automating our assessment process was a key driver for us. When we looked into Continuous Control Monitoring tools, CyberSaint stood out because we could land on one use case and expand over time without buying multiple tools.
The CyberStrong platform was built for CISOs (by CISOs) to assess and manage cyber-risk to assist them in developing, implementing, and managing a robust cybersecurity program. Not only does CyberStrong provide CISOs with an in-depth view of their cyber-posture and risk, it provides them with the ability to show, on demand, an executive, dashboard view of their cyber-risk profile. Such a capability is key for Board Directors, C-Suites, and senior executives, as it will allow them to effectively perform their governance (oversight) and management responsibilities in compliance with the varying regulatory requirements faced by organizations today, including the new SEC Cybersecurity regulations.
Shifting to CyberStrong allowed us to quantify cyber risk in tangible terms, aligning our strategy with top industry standards effortlessly. We've broken down silos, enhanced our risk tracking and reporting and have an informed approach to budgeting moving forward.
The SEC requirements have elevated the conversation around cyber risk to the Boardroom. CyberSaint’s platform not only hits on the need for increased automation at the foundational compliance level, but also the need to link controls to risks to make cyber risk management real-time. Companies now can have a clear understanding of their cyber risk posture and optimize accordingly based on their most likely cyber losses, risk mitigated, and ROSI. Translating cyber risk into financial terms is a game-changer for C-suites and Boards, and CyberSaint has cracked the code on rapid time to value and scalability for enterprise cyber risk quantification. The CyberStrong platform is a powerful solution for every enterprise CISO looking to master their cyber risk posture.
We needed to get going quickly, manage our cybersecurity posture continuously, and measure where we are today against where we as a leadership team determined we wanted to go. Automating our assessment process was a key driver for us. When we looked into Continuous Control Monitoring tools, CyberSaint stood out because we could land on one use case and expand over time without buying multiple tools.
The CyberStrong platform was built for CISOs (by CISOs) to assess and manage cyber-risk to assist them in developing, implementing, and managing a robust cybersecurity program. Not only does CyberStrong provide CISOs with an in-depth view of their cyber-posture and risk, it provides them with the ability to show, on demand, an executive, dashboard view of their cyber-risk profile. Such a capability is key for Board Directors, C-Suites, and senior executives, as it will allow them to effectively perform their governance (oversight) and management responsibilities in compliance with the varying regulatory requirements faced by organizations today, including the new SEC Cybersecurity regulations.
Shifting to CyberStrong allowed us to quantify cyber risk in tangible terms, aligning our strategy with top industry standards effortlessly. We've broken down silos, enhanced our risk tracking and reporting and have an informed approach to budgeting moving forward.

2025 Gartner® Hype Cycle™ for Cyber-Risk Management

AI-Powered Findings Management Solution Brief








.png)


