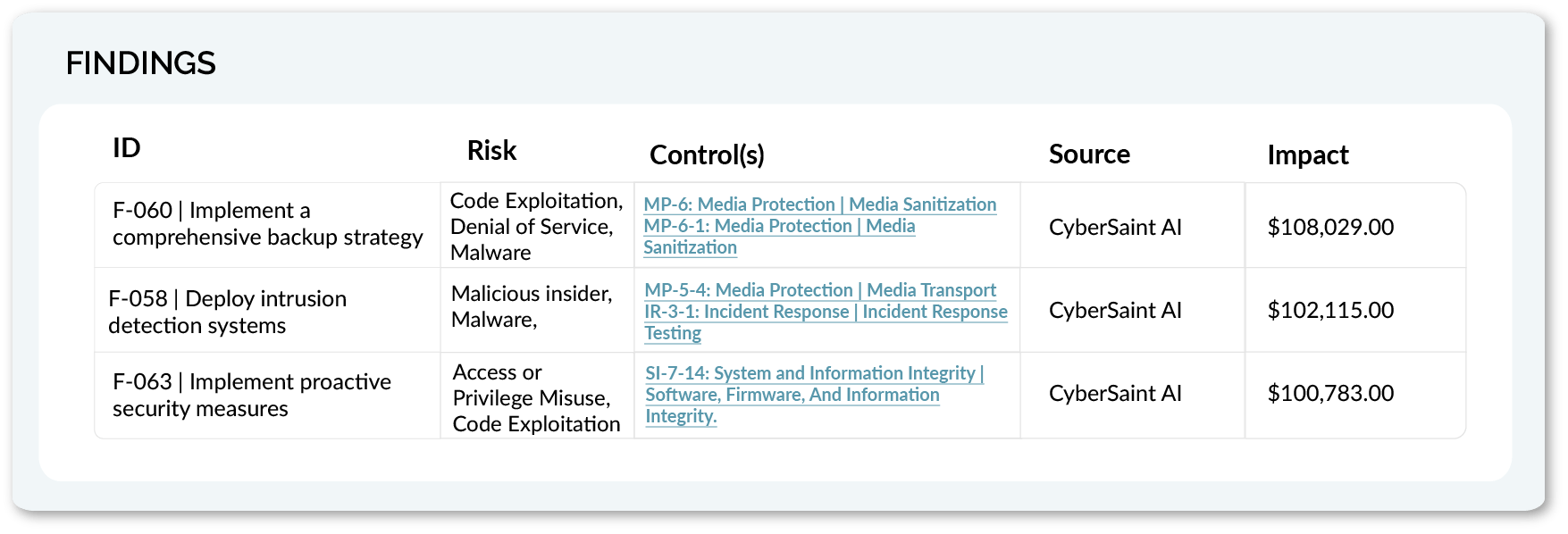
What is Cybersecurity Findings Management?
Cybersecurity findings management is the process of identifying, prioritizing, tracking, and remediating security issues uncovered through vulnerability scans, audits, or assessments.
A “finding” can represent anything from a failed control to a critical vulnerability, any deviation from the desired security posture.
Findings management connects these issues to their root causes, associated controls, and potential business impacts. When done well, it turns fragmented security data into clear, risk-informed action, strengthening your organization’s cyber resilience.
Why is Findings Management Important?
Without a unified system for managing cybersecurity findings, organizations face duplication, delays, and inconsistent remediation.
Effective findings management enables teams to:
- Prioritize findings by risk and impact instead of volume
- Improve visibility across frameworks and business units
- Streamline audit readiness and evidence collection
- Track remediation ownership and timelines
- Support continuous compliance and risk reduction
In short, findings management is where tactical remediation meets strategic risk management.
How Does Findings Management Impact Cybersecurity?
Effective findings management plays a critical role in an organization’s ability to:
- Minimize risk: Connect findings to threat intelligence and assess asset criticality.
- Boost efficiency: Streamline remediation efforts by removing redundancies across frameworks.
- Improve reporting: Deliver clear, data-driven updates tailored for leadership.
- Strengthen resilience: Ensure continuous visibility into both open and resolved findings.
Cyber Risk Quantification (CRQ) helps teams tie findings to measurable risk impact. It enables organizations to prioritize and allocate resources based on the potential effect of a finding, rather than solely on its severity or priority level. This allows more efficient risk reduction efforts and helps organizations maintain continuous compliance with industry regulations.
They can minimize risk by connecting findings to threat intelligence and assessing the criticality of assets, allowing them to prioritize remediation efforts accordingly. This not only boosts efficiency by streamlining the process but also strengthens resilience by continuously monitoring both open and resolved findings.
5 Common Challenges with Cybersecurity Findings Management
| Cybersecurity Findings Challenge | Description |
| Overwhelming Volume | Security tools produce thousands of findings with limited prioritization. |
| Siloed Systems | Vulnerabilities, audit findings, and compliance gaps exist in separate tools. |
| Limited Context | Findings aren’t connected to relevant controls or business processes. |
| Manual Tracking | Spreadsheets and ticketing systems slow remediation. |
| Reactive Cycles | Without feedback loops, organizations repeat the same errors. |
The Alert Fatigue Conundrum: How to Combat Fatigue with Streamlined Findings
Security analysts often experience alert fatigue due to a constant influx of repetitive, low-priority alerts that demand valuable attention. Streamlined findings management offers a solution by correlating numerous alerts into single, actionable findings. This process is further enhanced by filtering based on asset importance and business risk, and by linking findings to established control frameworks, which significantly speeds up remediation efforts.
Automating risk-based prioritization with AI is crucial in combating alert fatigue. This comprehensive approach enables security teams to focus on the most critical findings, ultimately reducing fatigue and significantly improving operational efficiency.
CyberStrong AI filters noise by automatically correlating alerts, control gaps, and threat intelligence, ensuring teams act only on what materially impacts the organization’s risk posture.
5 Best Practices for Intelligent Findings Management
- Centralize Findings: Consolidate findings from vulnerability scanners, compliance audits, and assessments to streamline analysis and reporting.
- Automate Prioritization: Use AI and real-time data to identify high-impact risks.
- Map Findings to Frameworks: Ensure traceability across NIST 800-53, ISO 27001, DORA, and others.
- Quantify Risk Impact: Convert findings into financial or operational risk metrics that accurately reflect the impact.
- Enable Continuous Validation: Implement Continuous Control Monitoring (CCM) to verify the effectiveness of remediation.
Explore how CyberStrong’s Continuous Control Automation (CCA) reduces manual validation and audit prep.
How to Evaluate a Findings Management Solution
What to Look for in a Findings Management Solution
When evaluating solutions, prioritize tools that offer:
- Automated data ingestion from multiple sources
- AI-driven prioritization and contextual risk scoring
- Cross-framework mapping to unify compliance and security findings
- Continuous control validation for sustained accuracy
- Integrated dashboards and reporting for technical and executive stakeholders
How Does CyberStrong Perform Findings Management?
CyberStrong automates every step of findings management—from detection to resolution.
The platform continuously ingests vulnerability data, audit results, and assessment findings, then correlates each finding with controls, risks, and frameworks.
Its AI-powered Findings Engine prioritizes findings in real time using threat intelligence, control gaps, and financial risk data, ensuring teams focus on issues with the highest impact.
Closed findings are automatically revalidated through Continuous Control Monitoring (CCM); no manual reassessment is required.
What is Different About CyberSaint’s Approach to Findings?
CyberSaint’s approach embeds findings management into a unified cyber risk management ecosystem. Rather than isolating findings in separate modules, CyberStrong contextualizes them within the organization’s risk register, illustrating how each finding impacts quantified cyber risk and posture.
This integration enables CISOs to track remediation progress, measure ROI, and communicate results in business-relevant terms. AI-powered Findings Management is designed not only for efficiency but also for executive alignment and measurable risk reduction.
See how CyberStrong’s Risk Register connects findings to enterprise risk.
How Do Cybersecurity Findings Impact Cyber Resilience?
Findings are signals of system weakness, and how organizations manage them defines their cyber resilience. Continuous, prioritized findings management enables:
- Faster response to evolving threats
- Data-driven insight into risk posture
- Measurable improvement in security maturity
Over time, this process transforms findings from operational noise into strategic intelligence, fueling a proactive and adaptive defense model.
How Does Findings Management Support Cyber Risk Management?
Findings management and cyber risk management are tightly connected. Each finding represents a data point that shapes the organization’s risk register, informs quantification models (like FAIR or NIST 800-30), and guides remediation investment decisions.
CyberStrong bridges these domains by quantifying findings and correlating them with control gaps, threats, and financial exposure, turning technical data into actionable business insights. CyberStrong helps CISOs translate findings into financial terms, enabling data-driven discussions with leadership on where to prioritize investment and demonstrating return on security investment (RoSI).
When findings are managed intelligently, they don’t just close risks; they advance cyber resilience and strategic confidence. With CyberStrong, findings management isn’t a standalone task; it’s a fully integrated component of a connected, continuous, and quantified cyber risk management strategy. This alignment drives not only faster remediation, but also measurable resilience and strategic clarity.





.png)
.png)
.png)
%201.png)
.png)