CyberSaint AI
Identify, Prioritize, and Act on What Matters Most
Uncover real-time clarity from real-world complexity. CyberSaint AI correlates millions of internal and external data points to surface what matters—empowering you to reduce millions in risk exposure by addressing findings with speed and precision.
You Have the Data, Now Answer "So What?"
Security teams are overloaded with findings but lack the context to act on those that truly matter. CyberStrong continuously maps relationships between your internal gaps and external threat intelligence to prioritize what poses the greatest risk.
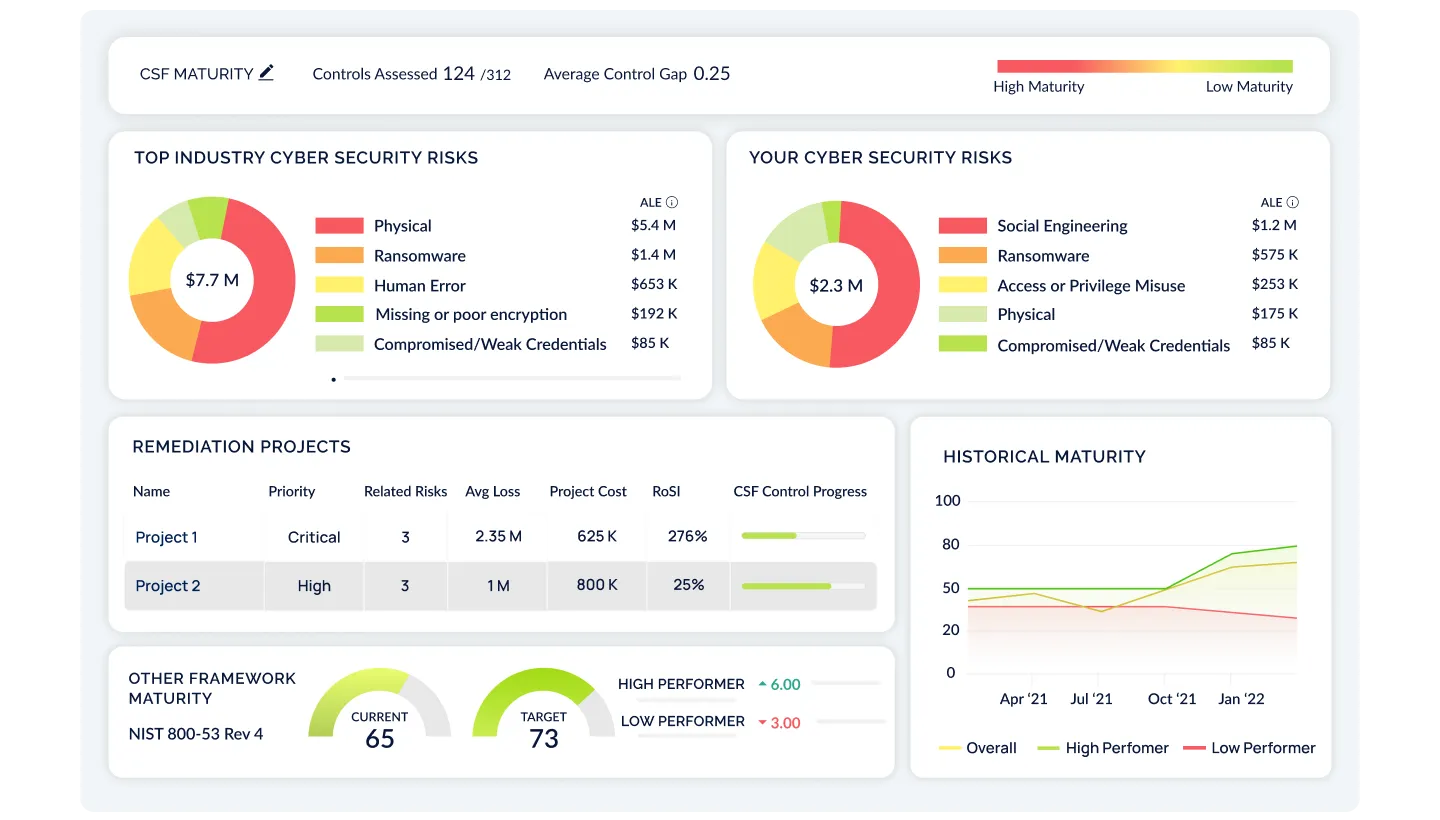
Go Beyond Static Risk Registers
CyberStrong continuously ingests real-time data from your environment and leading threat intelligence sources. Instead of waiting for assessments to catch up, you’ll always know where your biggest risks are—and why.
.png)
Focus on Impact, Not Volume
Prioritized findings are ranked by what they could cost your business. CyberStrong blends control posture, threat activity, and financial exposure into a single view, so you can direct attention to the issues that matter most.
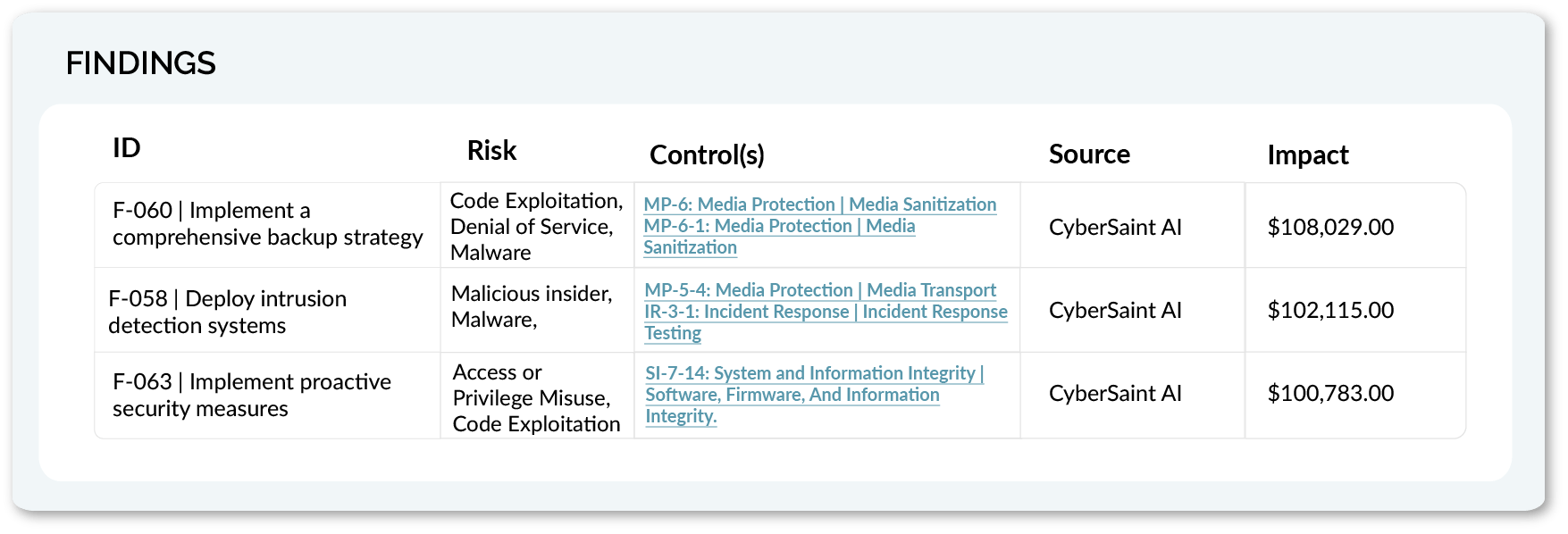
From Insight to AI-Powered Action
Every prioritized finding includes recommended remediation steps, mapped to relevant frameworks and controls. Teams can move from identification to resolution without wasting time or energy.
Stay Ahead of What’s Next
Whether there’s a surge in ransomware or a newly disclosed vulnerability, CyberStrong’s prioritized findings update automatically to reflect the current threat landscape. Your risk posture is refreshed and ready every day.
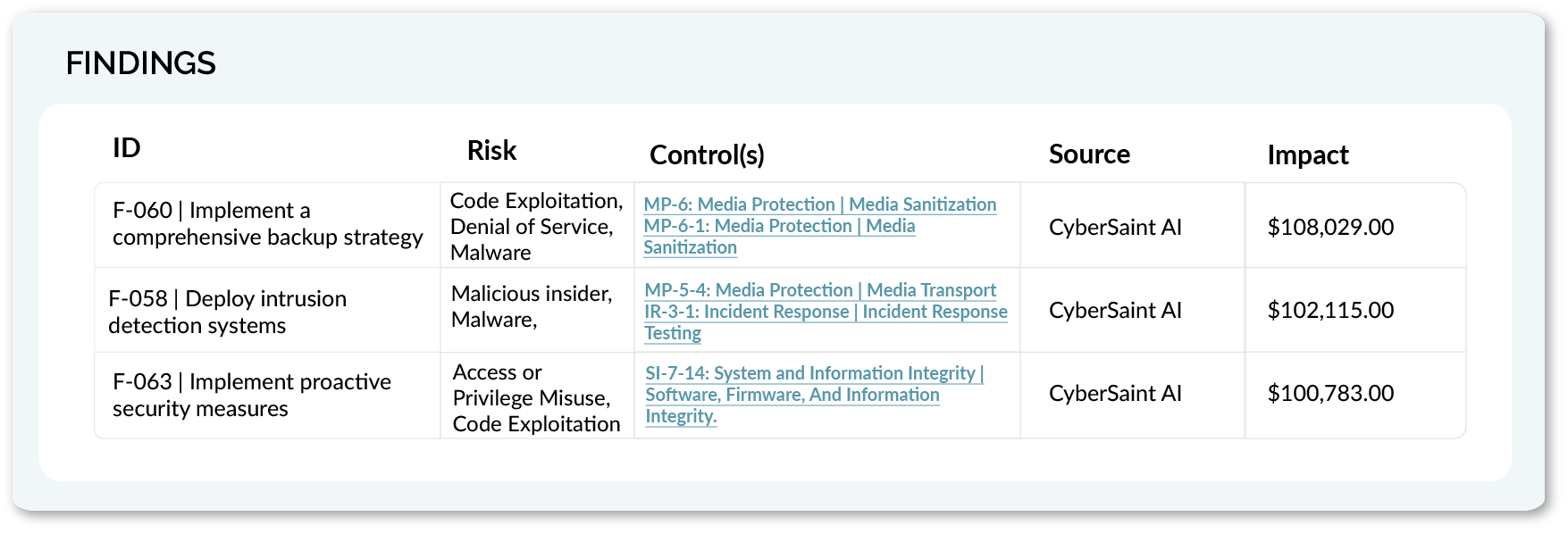
Go Beyond Static Risk Registers
CyberStrong continuously ingests real-time data from your environment and leading threat intelligence sources. Instead of waiting for assessments to catch up, you’ll always know where your biggest risks are—and why.
.png)
Focus on Impact, Not Volume
Prioritized findings are ranked by what they could cost your business. CyberStrong blends control posture, threat activity, and financial exposure into a single view, so you can direct attention to the issues that matter most.

From Insight to AI-Powered Action
Every prioritized finding includes recommended remediation steps, mapped to relevant frameworks and controls. Teams can move from identification to resolution without wasting time or energy.
Stay Ahead of What’s Next
Whether there’s a surge in ransomware or a newly disclosed vulnerability, CyberStrong’s prioritized findings update automatically to reflect the current threat landscape. Your risk posture is refreshed and ready every day.

.png)
Powered by CyberSaint AI
Learn how NLP, graph neural net engines and agentic AI takes cyber risk management to the next level—delivering exponential efficiencies for teams.
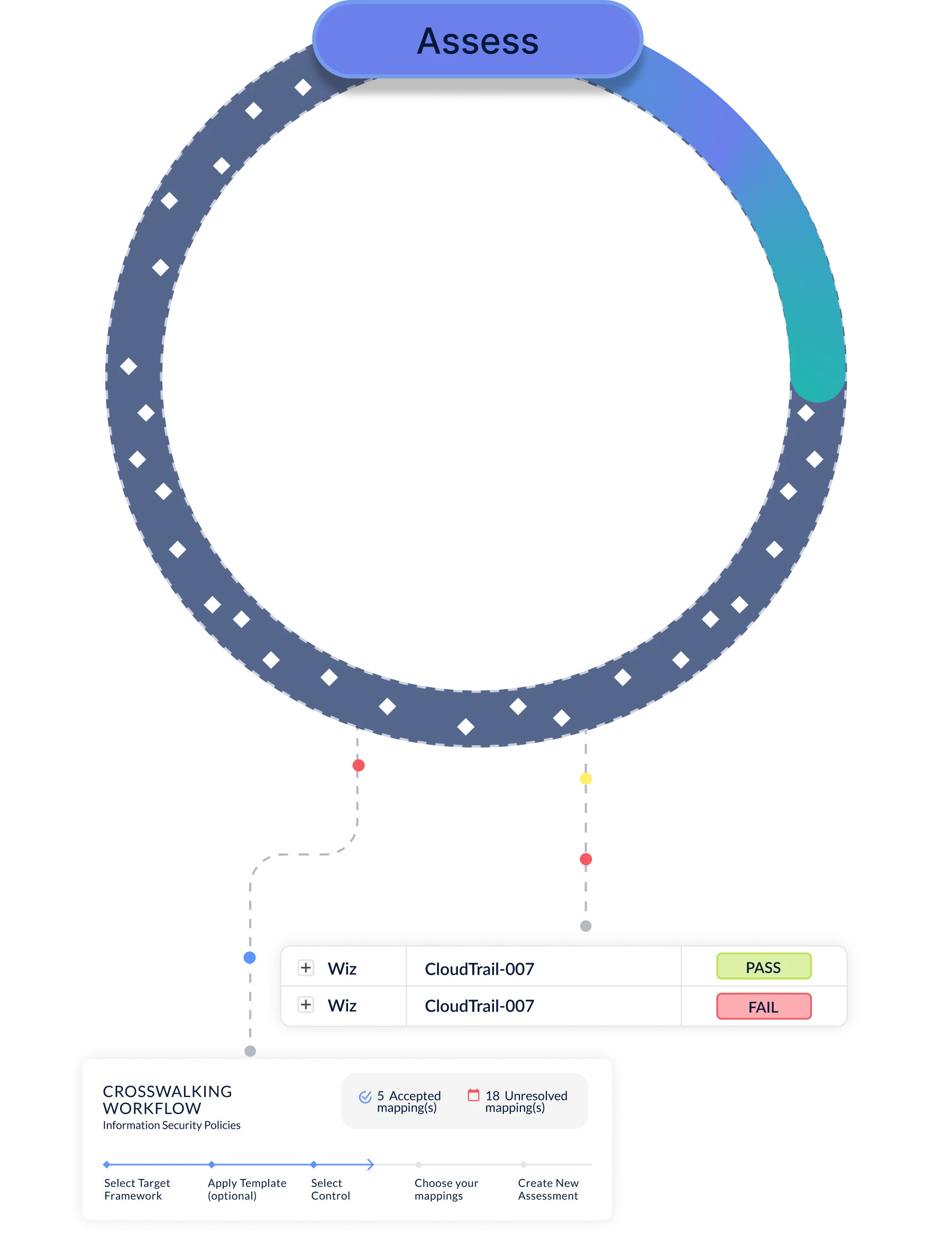
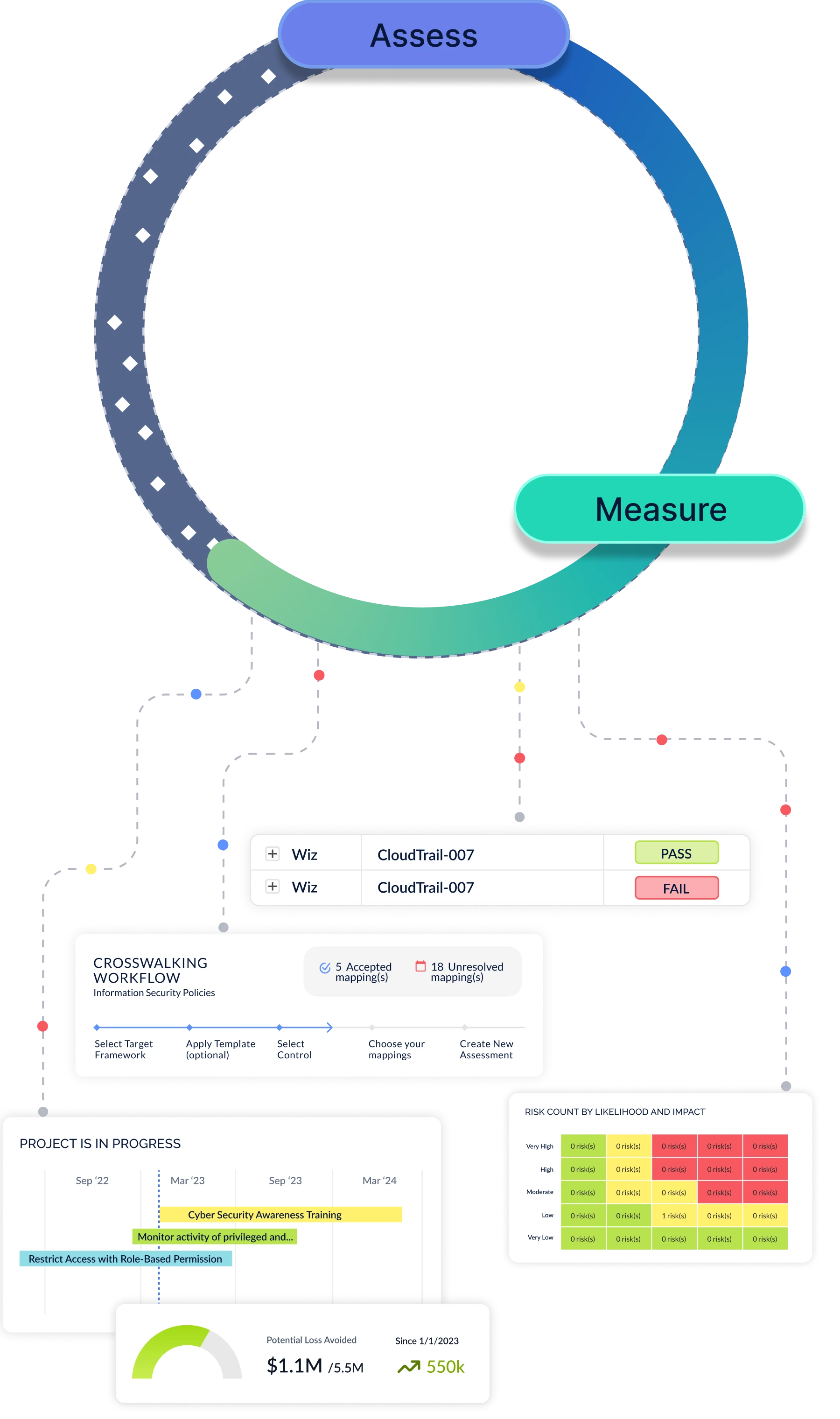
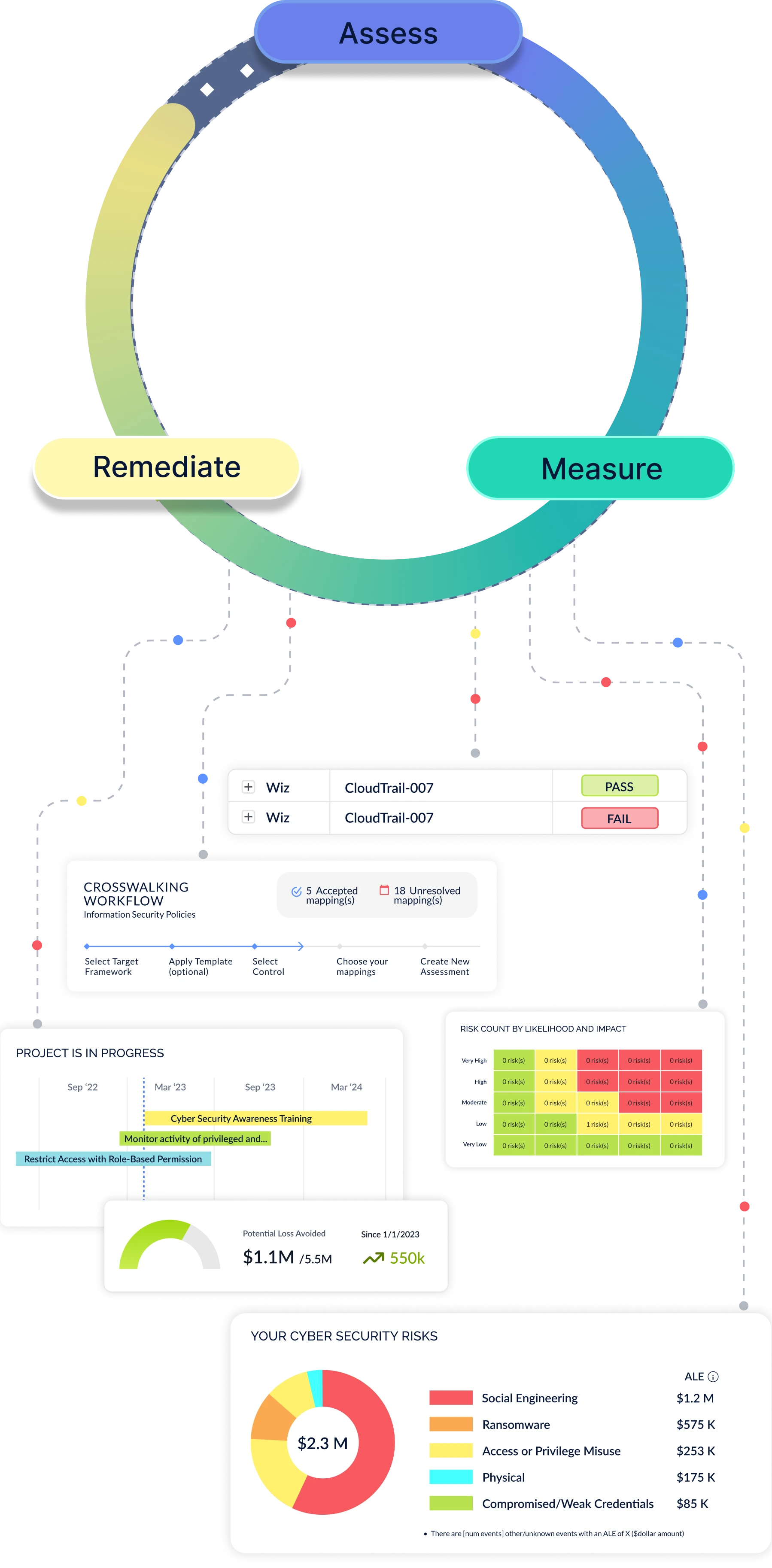
The CyberStrong Platform Architecture
Designed to continuously assess, measure, remediate, and communicate cyber risk enterprise-wide, taking into account new security data, additional controls, and newly identified risks as your program matures
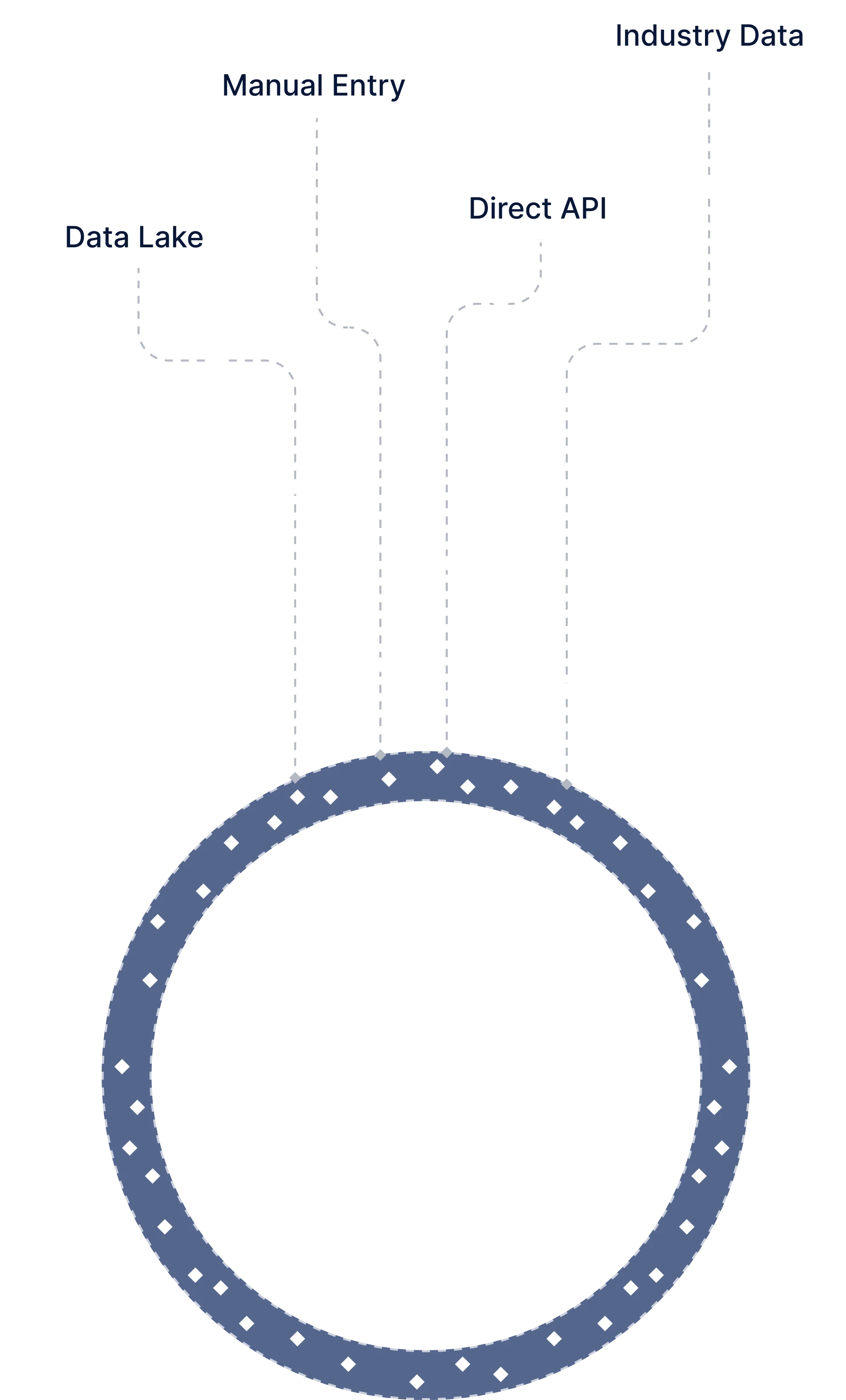
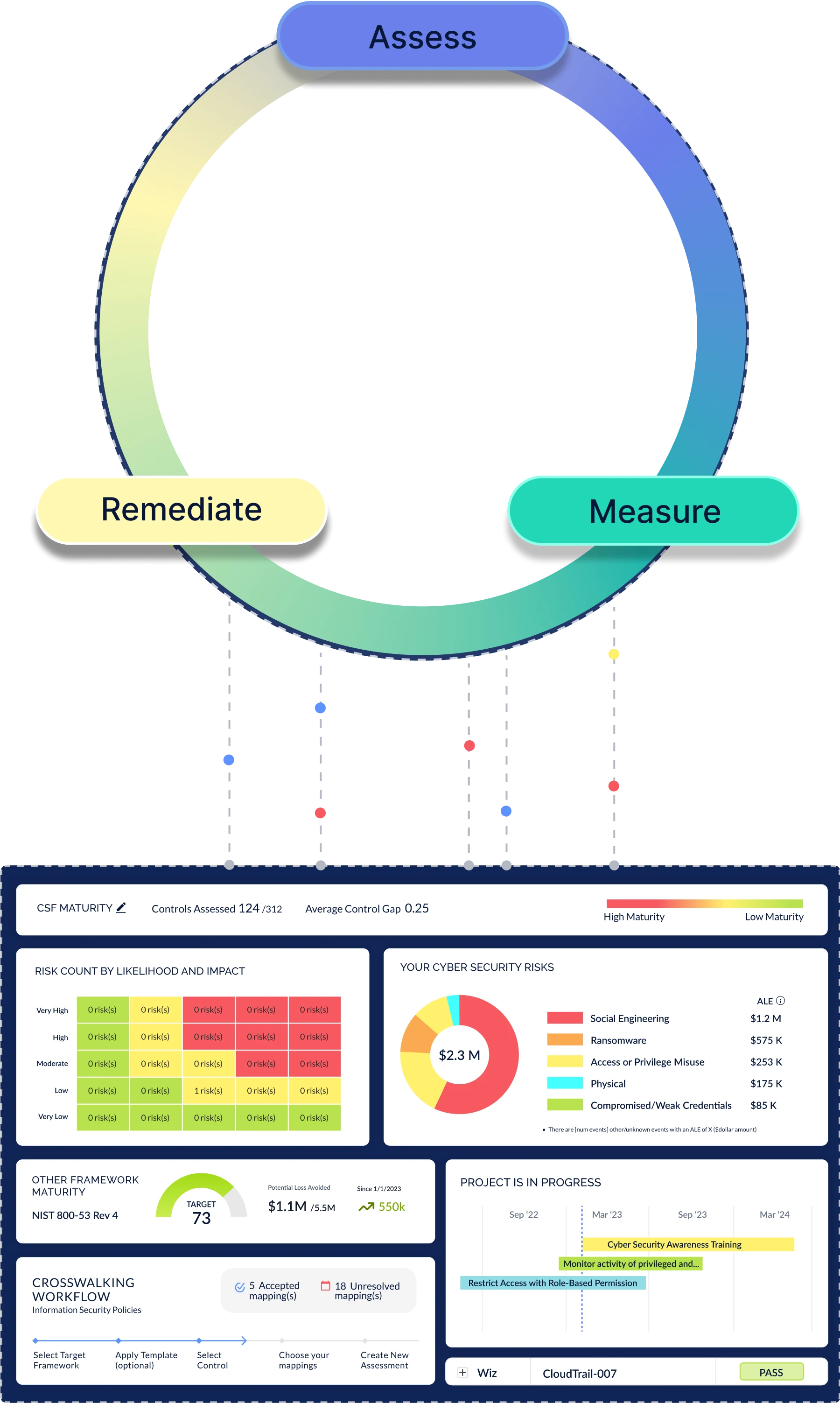
You're Sitting on a Goldmine — Let's Use It
Frameworks, Assessments & Controls
Cyber Risk Quantification & Risk Tracking
Risk & Control Remediation
Executive Insights for the C-Suite & Board
CyberStrong Differentiators
Transition from manual processes to automation, replace black-box scoring with transparent and credible models, and consolidate point solutions into a single, unified platform
AI-Powered
We've been innovating in Artificial Intelligence and Machine Learning since inception, and built our platform on patents that were approved starting in 2019.
Immediate Value
CyberStrong delivers immediate insights into customers' cyber risk posture, and most customers are active in system within one week or less.
Credible CRQ
We've humanized cyber risk quantification and mapped cyber risk to metrics that CFOs, CEOs, and Boards are already asking for and can understand.
Powerful Automation
Use Continuous Control Monitoring to automate control scoring, moving from point-in-time assessment to real-time. Plus, use Agentic Evidence Collection to validate evidence, and automate framework crosswalking to use data in one assessment to meet controls in another.
Holistic Approach
Move beyond reporting on framework compliance, risks, cyber events, and remediations in silos. CyberStrong connects controls directly to risk register entries and links risks to investments, providing a precise snapshot of your cyber risk posture.
Intuitive Platform
Cyber risk is complex, but the solution is simple. Tailored for scalability and efficiency, the platform ensures seamless navigation and quick access to every feature. We've minimized the learning curve, training up users within days of onboarding.
FORTUNE 500 CASE STUDY
Quantify Risk. Prioritize Gaps. Reduce Cyber Risk Exposure.
After a 2022 ransomware attack, the CISO needed a solution to serve as the foundation of their new cyber risk management program. The team wanted to track the potential financial loss and impact of cyber risks, prioritize actions, and unlock budget. CyberStrong allowed them to:
- Build the foundation of their program off of NIST SP 800-171, CMMC, and the NIST CSF with the ability to add other frameworks
- Transition from a spreadsheet-based risk register to a centralized, quantifiable NIST 800-30 risk register for credible cyber risk quantification
- Use cyber risk presets to map threats to MITRE TTPs, enhancing risk prioritization by linking TTPs directly to controls
- Empower the CISO with a scalable, data-driven solution to spur action and influence decisions





