With an increasing interest in cyber as a business function, it is vital that non-technical leaders are tuned into the cyber posture of their organization. Data visualizations that can depict the impact of cyber on business are in demand for technical and non-technical leaders to understand what’s happening in cyber. Cybersecurity dashboards aggregate and consolidate data into functional, presentable, easy-to-understand images that visualize cybersecurity posture in real-time.
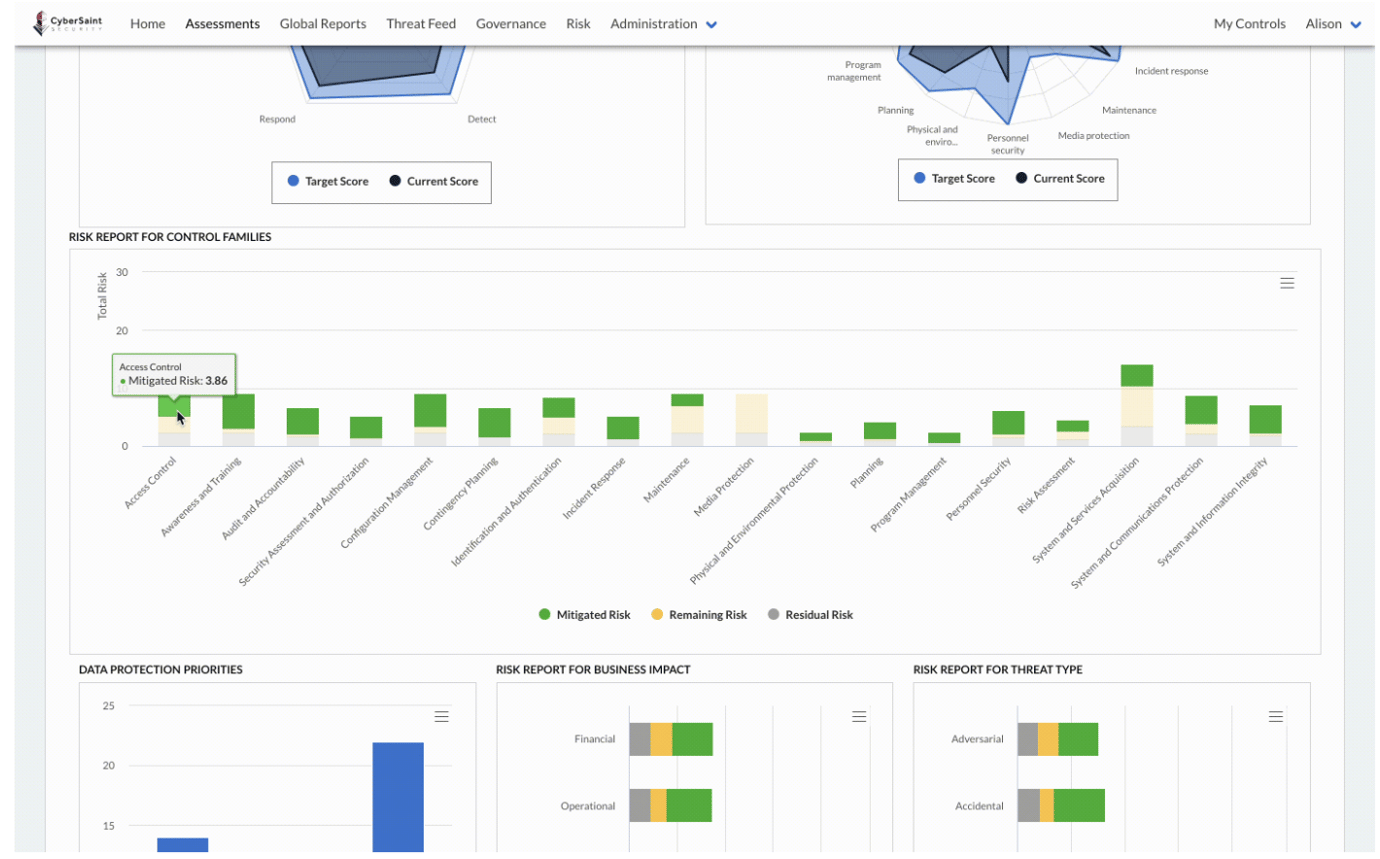
The CyberStrong Assessment Dashboard illustrates assessment data against a gold-standard framework like the NIST Cybersecurity Framework. The Cyberstrong Assessment Dashboard enables mapping between any framework or standard, such as CMMC, NERC CIP, and NIST CSF. Thus, you can instantly map frameworks and simultaneously see where you are on the NIST CSF.
With advanced dashboarding capabilities, security teams can leverage the real-time information delivered to identify gaps in the security structure and proactively manage risk. CyberStrong maps data on people, processes, technology, risk, and cost against your current gaps to provide a Pareto Efficient frontier optimization that identifies “low-hanging fruit” opportunities to mitigate cyber risk for “always-on” continuous improvement. Furthermore, CyberStrong is the only solution that uses AI to augment manual effort in this way, and CyberStrong’s AI rank-orders the top results out of billions of possible combinations, finding the optimal path to success and eliminating lesser results.
In short, the Assessment Dashboard is excellent for visualizing distinct strengths and weaknesses in security posture. Security leaders gain actionable insights for remediation, benchmarking against any gold-standard framework used for the assessment. With dashboards that can clearly depict this critical information, leaders can confidently present to the board, illustrate the connection between business and security, and gain granular insight into risk as broken down by control family.
Contact us to learn more about CyberStrong’s cybersecurity dashboarding and reporting capabilities. Read about other dashboard functions, like executive dashboards, here.





.png)
.png)
.png)
%201.png)
.png)