CyberSaint AI
Agentic Evidence Collection
Continuously and securely collect audit-ready evidence with autonomous agents. Go beyond API integrations and leave manual effort behind.
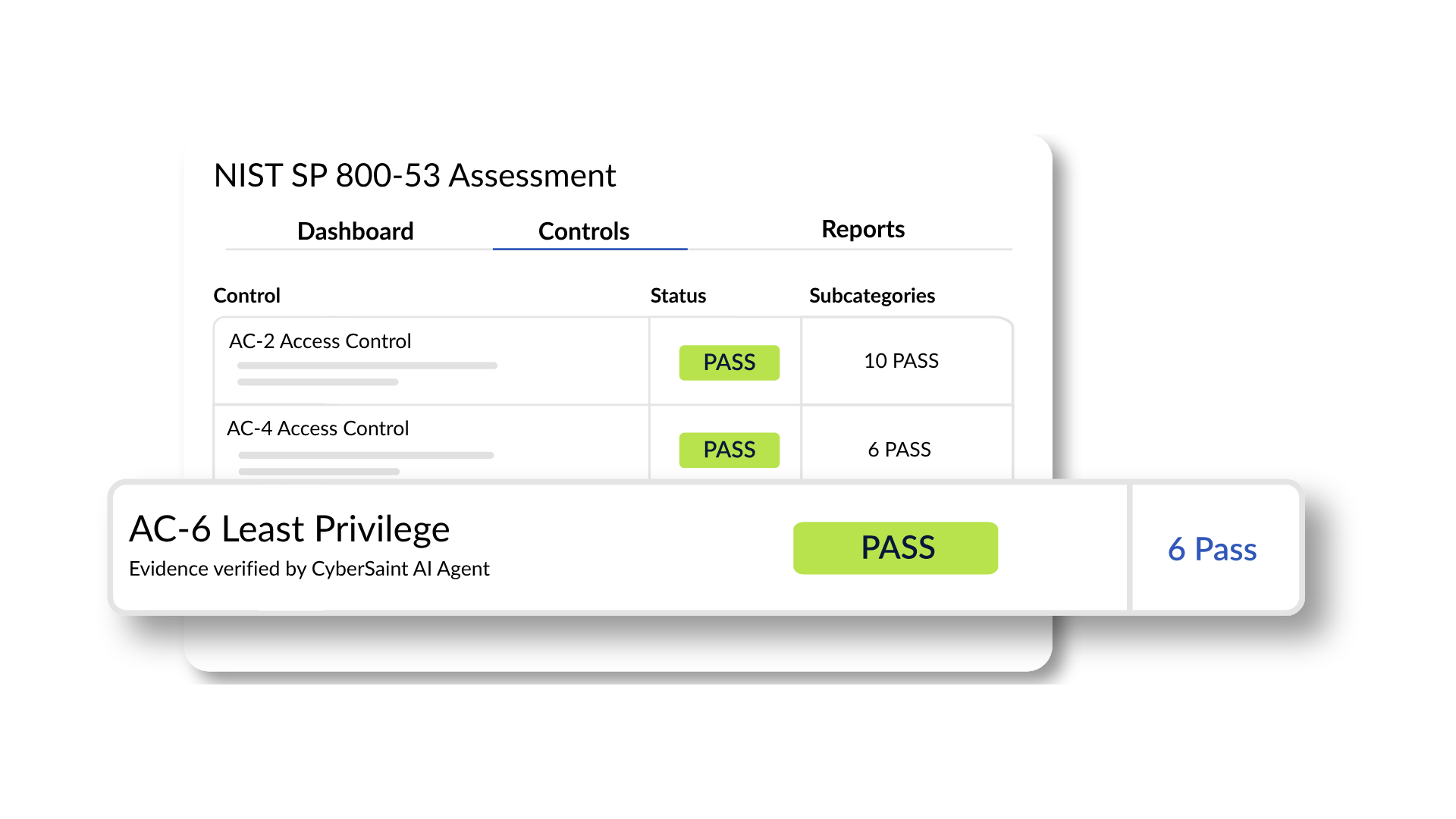
Focus on reducing risk and passing audits, not chasing screenshots.
Built for compliance and audit teams ready to move beyond manual check-box work, CyberSaint's Agentic Evidence Collection gathers structured and unstructured data across your tech stack to validate continuous compliance and demonstrate audit readiness.
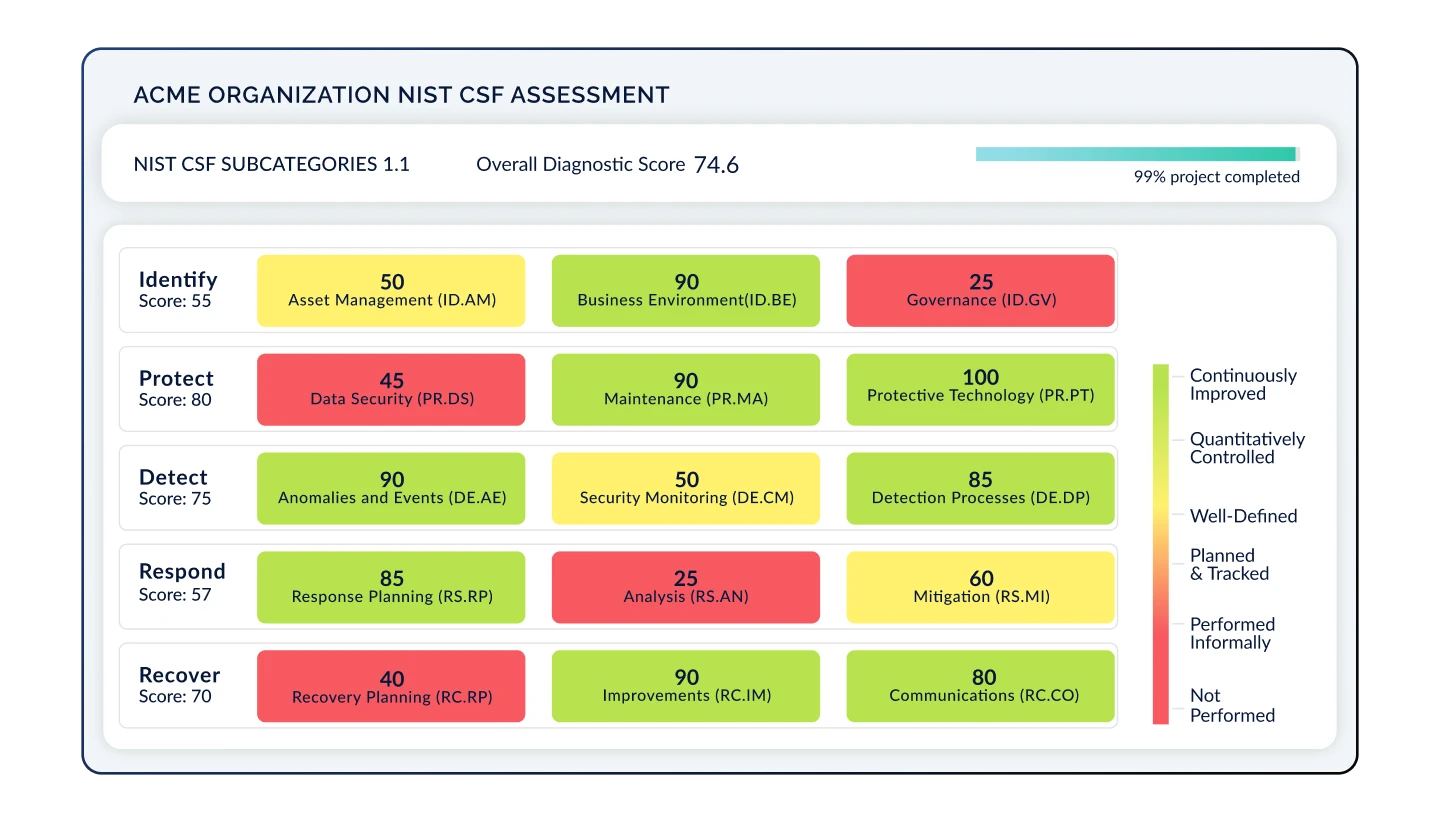
Ensure Complete Visibility & Accuracy
Capture real-time, comprehensive evidence - including structured and unstructured data - to stay continuously audit-ready. Collect screenshots, configuration files, system logs, and more automatically mapped to the controls they fulfill.
Eliminate Audit Fatigue
Evidence gathering consumes up to 60% of a compliance team’s time - time that could be spent on higher-value work. Trade long audits, unnecessary delays, and increased team burnout for accuracy and agility.
-1.png)
Go Beyond API Limits & Scale Without Complexity
APIs can’t reach every system or evidence type, and they introduce coverage gaps, security concerns, and rigid workflows. Agentic evidence collection eliminates these constraints by autonomously gathering evidence across environments that APIs miss, ensuring full coverage without sacrificing flexibility, scalability or security.
Enforce Guardrails Without Sacrificing Agility
Run agentic evidence collection within strict, pre-defined boundaries, ensuring every action is logged, permissioned, and auditable. With built-in security guardrails, lightweight agents scale secure automation across complex environments without compromising trust or control.
Agentic Evidence Collection Solution Sheet
Accelerate Continuous Compliance
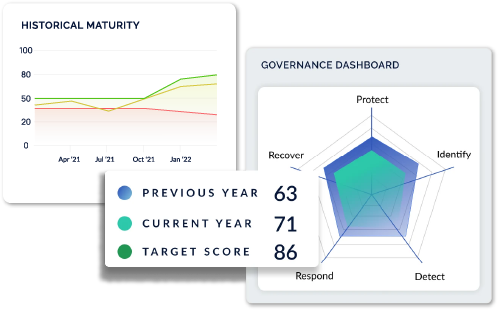
Agentic Evidence Collection feeds your CyberStrong instance with real-time data, keeping your controls continuously validated and your reports always up to date. Download the overview to learn more.
Becoming CyberStrong
CyberStrong has transformed our approach to cyber risk management. The real-time insights and automated assessments have not only streamlined our processes and saved costs but have also significantly enhanced our decision-making capabilities. I feel confident justifying the dollars in my budget towards key initiatives, because I can quantify the impact we're making.
Thanks to CyberStrong, we can now present our cybersecurity strategy and its financial implications to our executives in a language they understand. This has significantly improved executive buy-in and the maturity of our cyber practice.
The SEC requirements have elevated the conversation around cyber risk to the Boardroom. CyberSaint’s platform not only hits on the need for increased automation at the foundational compliance level, but also the need to link controls to risks to make cyber risk management real-time. Companies now can have a clear understanding of their cyber risk posture and optimize accordingly based on their most likely cyber losses, risk mitigated, and ROSI. Translating cyber risk into financial terms is a game-changer for C-suites and Boards, and CyberSaint has cracked the code on rapid time to value and scalability for enterprise cyber risk quantification. The CyberStrong platform is a powerful solution for every enterprise CISO looking to master their cyber risk posture.
CyberStrong has transformed our approach to cyber risk management. The real-time insights and automated assessments have not only streamlined our processes and saved costs but have also significantly enhanced our decision-making capabilities. I feel confident justifying the dollars in my budget towards key initiatives, because I can quantify the impact we're making.
Thanks to CyberStrong, we can now present our cybersecurity strategy and its financial implications to our executives in a language they understand. This has significantly improved executive buy-in and the maturity of our cyber practice.
The SEC requirements have elevated the conversation around cyber risk to the Boardroom. CyberSaint’s platform not only hits on the need for increased automation at the foundational compliance level, but also the need to link controls to risks to make cyber risk management real-time. Companies now can have a clear understanding of their cyber risk posture and optimize accordingly based on their most likely cyber losses, risk mitigated, and ROSI. Translating cyber risk into financial terms is a game-changer for C-suites and Boards, and CyberSaint has cracked the code on rapid time to value and scalability for enterprise cyber risk quantification. The CyberStrong platform is a powerful solution for every enterprise CISO looking to master their cyber risk posture.
Unlock More Value From CyberStrong
Build on a strong compliance foundation by layering in cyber risk quantification and executive insights
Risk Hub
Everything in the Compliance Hub, plus a flexible risk register, risk dashboards and reports, and a credible approach to cyber risk quantification. Manage your risk posture and clearly communicate cybersecurity in financial terms.
Learn MoreExecutive Hub
Everything in the Risk Hub, plus a robust Remediation Suite and compelling Executive Dashboard. Compare and track remediation projects, risk buy-down, and ROSI. Articulate your cyber posture compared to your peers and ensure impact and severity of cyber risks is understood.
Learn MoreCompliance in Motion
Pair Agentic Evidence Collection with Continuous Controls Monitoring for the ultimate compliance automation unlock
Continuous Controls Monitoring
Score controls automatically as data in your security tech stack changes, moving from point-in-time assessment to real-time assessment
Explore Compliance AutomationFeatured Resources
Discover the essentials of cyber risk management and enhance your expertise.

2025 Gartner® Hype Cycle™ for Cyber-Risk Management

AI-Powered Findings Management Solution Brief

Key Takeaways from Gartner's Market Guide for TPRM Technology Solutions
CYBERSTRONG PLATFORM DEMO
See CyberStrong in Action
CyberStrong is built on the principles of innovation, simplicity, and effectiveness, empowering you to continuously optimize your cyber posture with data-driven insights. We're excited to meet you!
What to expect:
-
Customer-Centric Discovery: This time is yours. We start by listening to you—understanding your unique challenges and goals. This enables us to propose solutions that can meet the specific needs of your industry and organization.
-
Interactive Platform Walkthrough: Get hands-on experience with our platform, from control automation to cyber risk quantification. See firsthand how CyberStrong turns complex cyber risk and compliance data into action.
-
Expert Guidance: Engage with our experts who will be available to answer your questions, discuss best practices used by our customers, and show you how CyberStrong integrates with your existing security infrastructure to enhance your cyber resilience.
What the community is saying...
The CyberStrong platform is a powerful solution for every enterprise CISO looking to master their cyber risk posture.






.png)