One Platform, Complete Cyber Risk Intelligence
CyberStrong seamlessly ingests data from your tech stack, benchmarks risks against industry peers, and correlates internal and external signals to prioritize your remediation efforts.
TRUSTED BY INDUSTRY LEADERS
Cyber Risk Success. Measured.
$ 0 T+
0 M+
$ 0 M+
AI & Automation Powering Every Critical Use Case
There's more that you cybersecurity data can tell you. CyberStrong delivers on key use cases with proprietary AI and advanced automation, using open and transparent methodologies and frameworks to deliver a complete picture of first-and-third-party risk
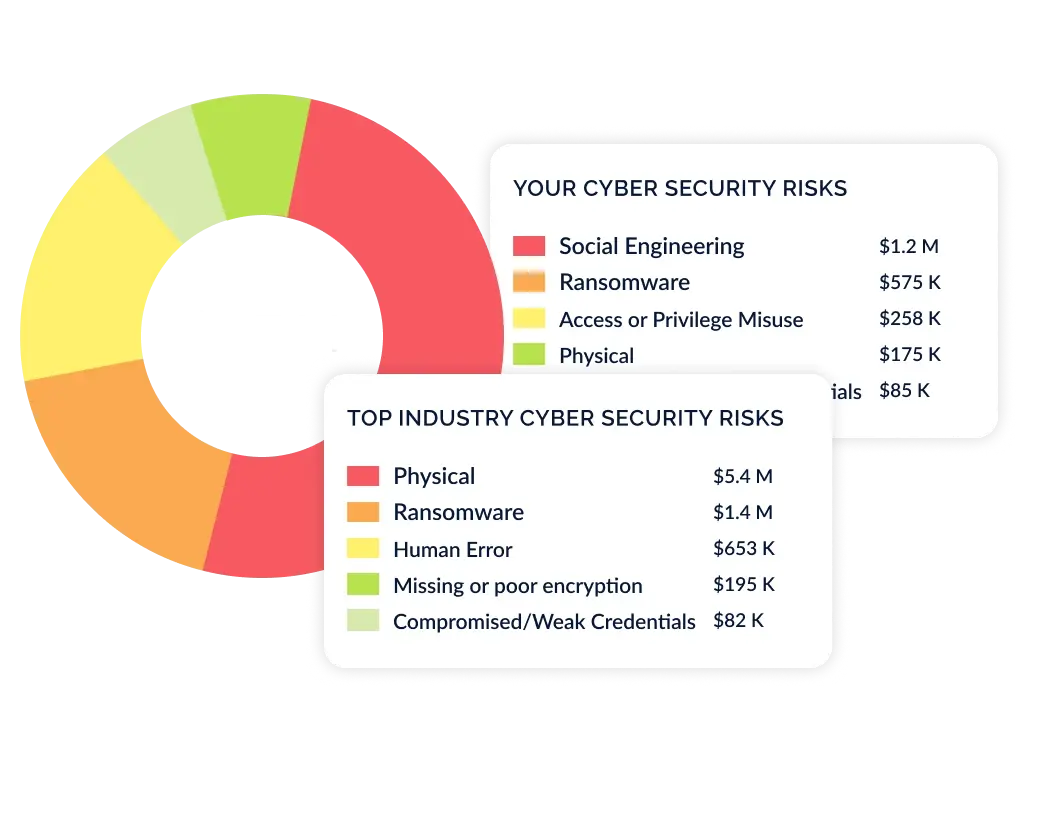
Benchmarking Backed by the Largest Cyber Loss Dataset
CyberStrong's industry risk capability leverages the world's largest dataset of cyber loss data, updated monthly, to provide tailored risk insights. Identify and prioritize the top cyber risks specific to your industry, company size, and revenue, ensuring a targeted and effective risk management and compliance strategy backed by data.
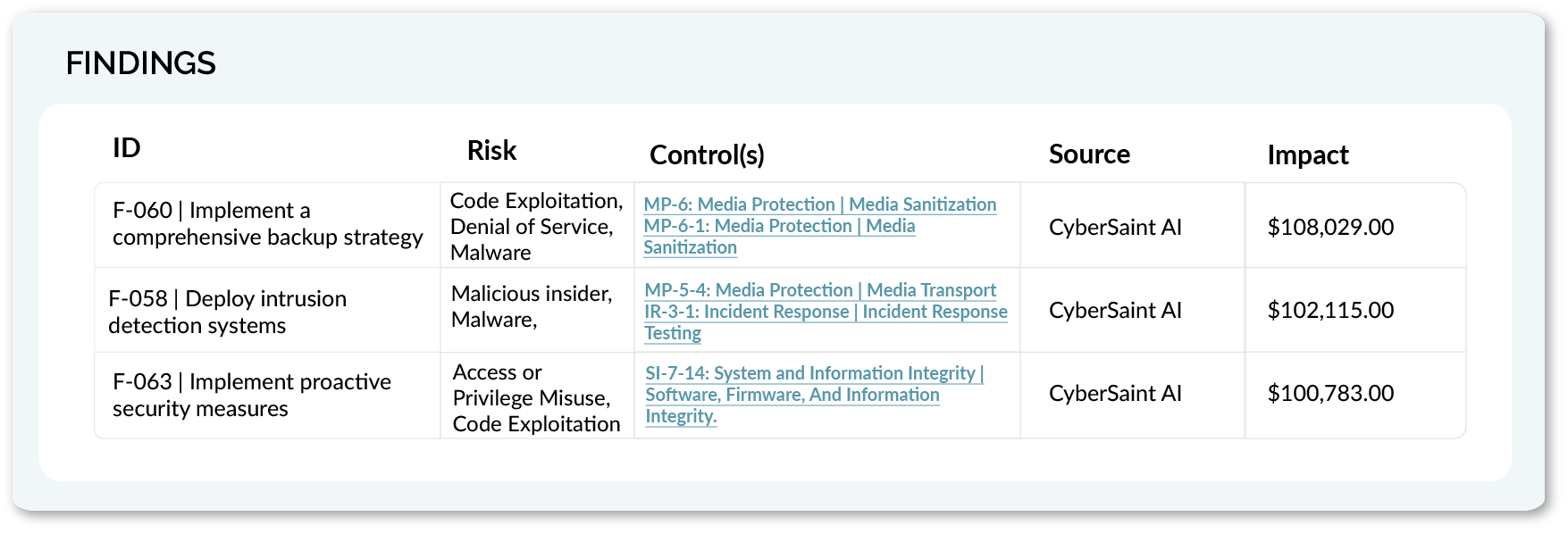
AI-Powered Prioritized Findings
Backed by CyberSaint AI, security leaders and their teams see findings in context - now, the top priorities are not lost in a notification deluge. See the threats that matter mapped to tracked controls and risks dynamically.
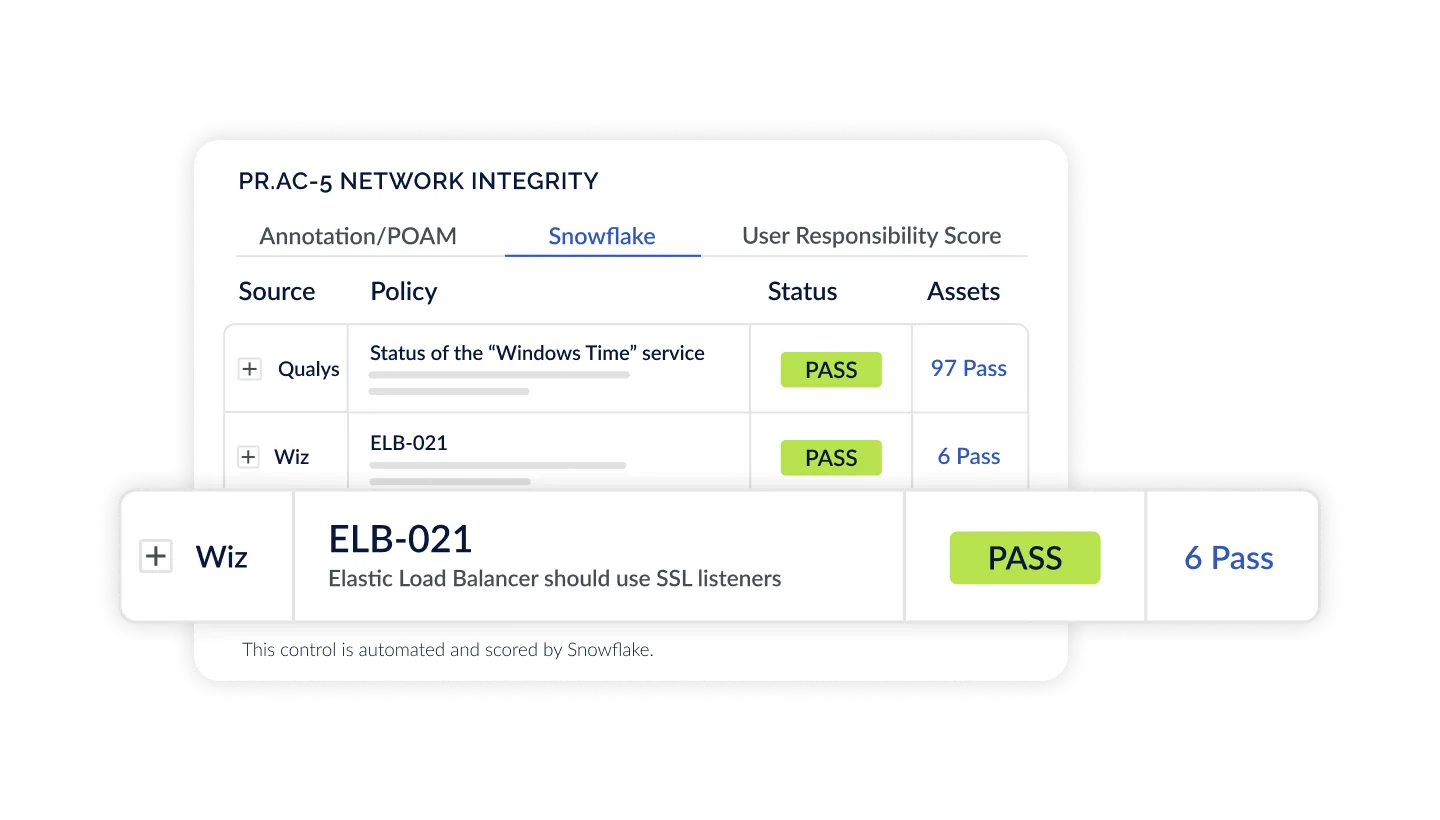
Automated Control Monitoring & Agentic Evidence Collection
Compliance remains a massive tax on security teams. CyberStrong automates multiple aspects of the assessment process: technical control scoring using Continuous Control Monitoring, evidence collection using computer vision-based agents, and NLP-based crosswalking to map controls based on intent. All combining to deliver a real-time view of compliance posture while reducing manual effort by over 70%.
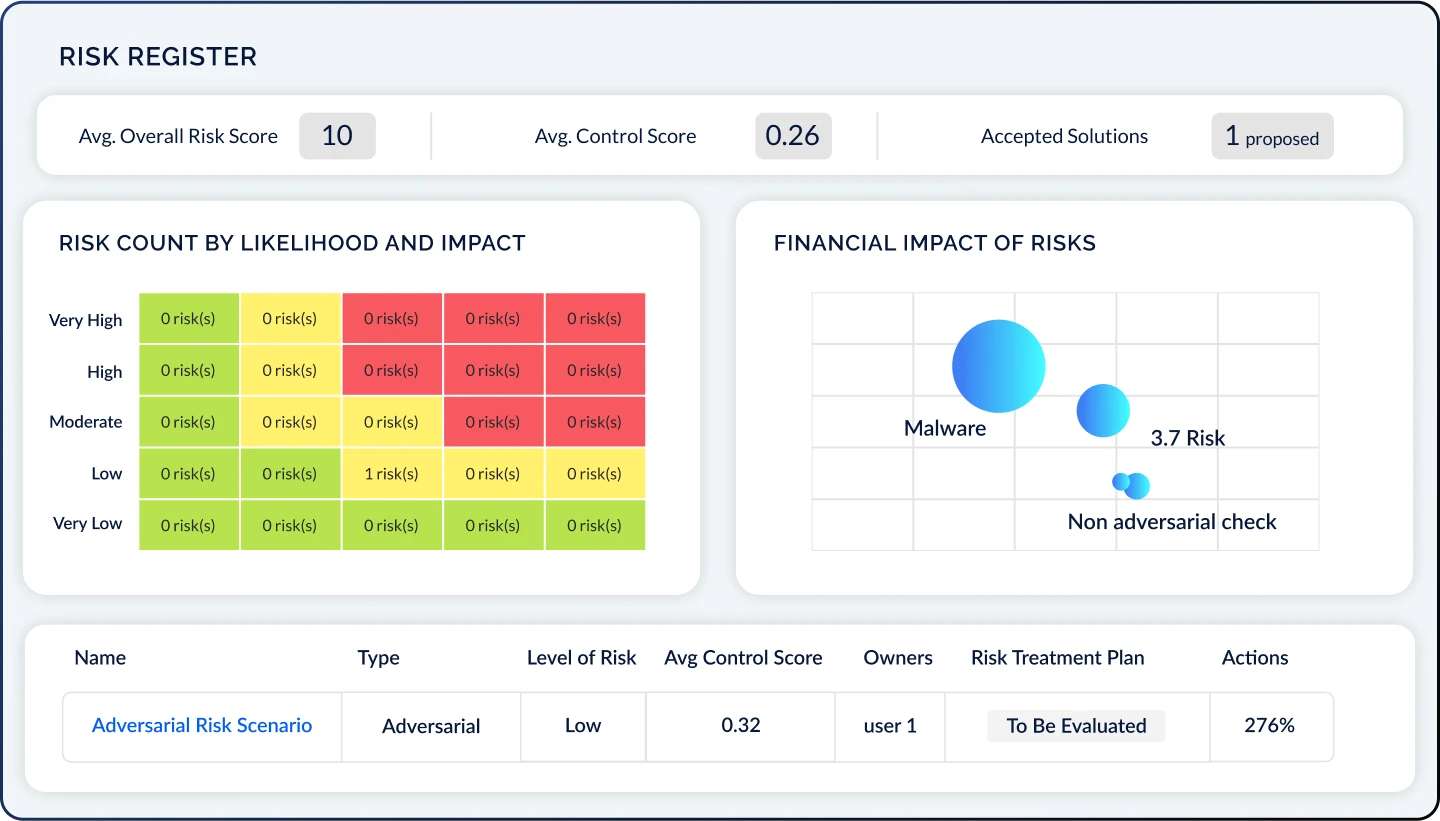
Dynamic Risk Register & Cyber Risk Quantification
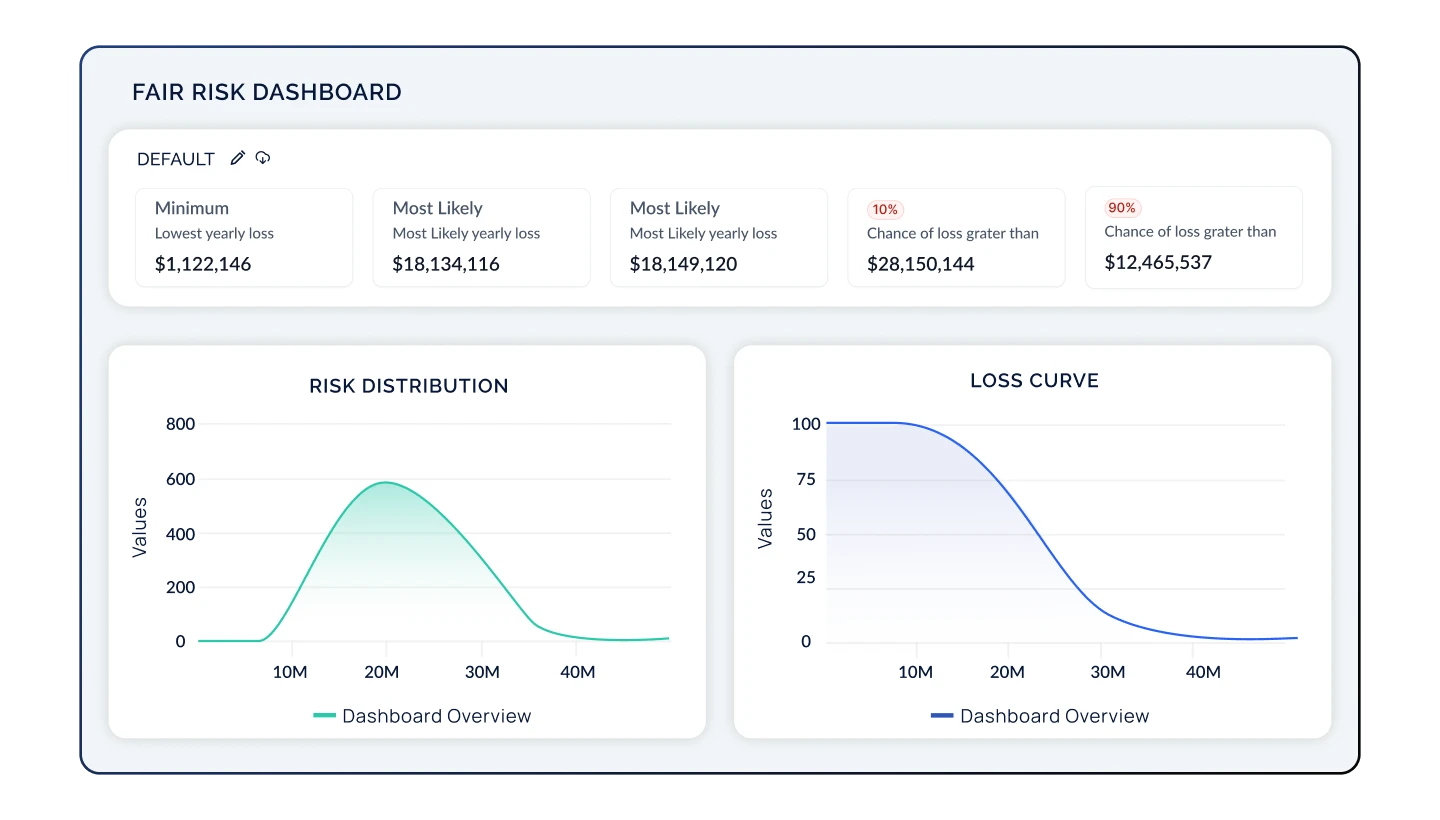
CyberStrong makes cyber risk quantification transparent, scalable, and easy to deploy, offering various models such as FAIR and NIST 800-30. The Risk Register offers customizable heat maps, financial impact charts, and additional features to help you transfer, avoid, accept, or mitigate risk. Streamline the process of identifying, quantifying, and prioritizing cybersecurity initiatives, which spurs action and allows you to close gaps with confidence.
ROSI Calculation & Scenario Analysis
CyberStrong's Remediation Suite offers a robust set of tools for tracking remediation efforts and their impact on your cyber risk posture. This approach encompasses cost simulations, Return on Security Investment (RoSI) analysis, and project timeline forecasting, facilitating informed decision-making on the optimal strategies to reduce your cyber risk exposure.
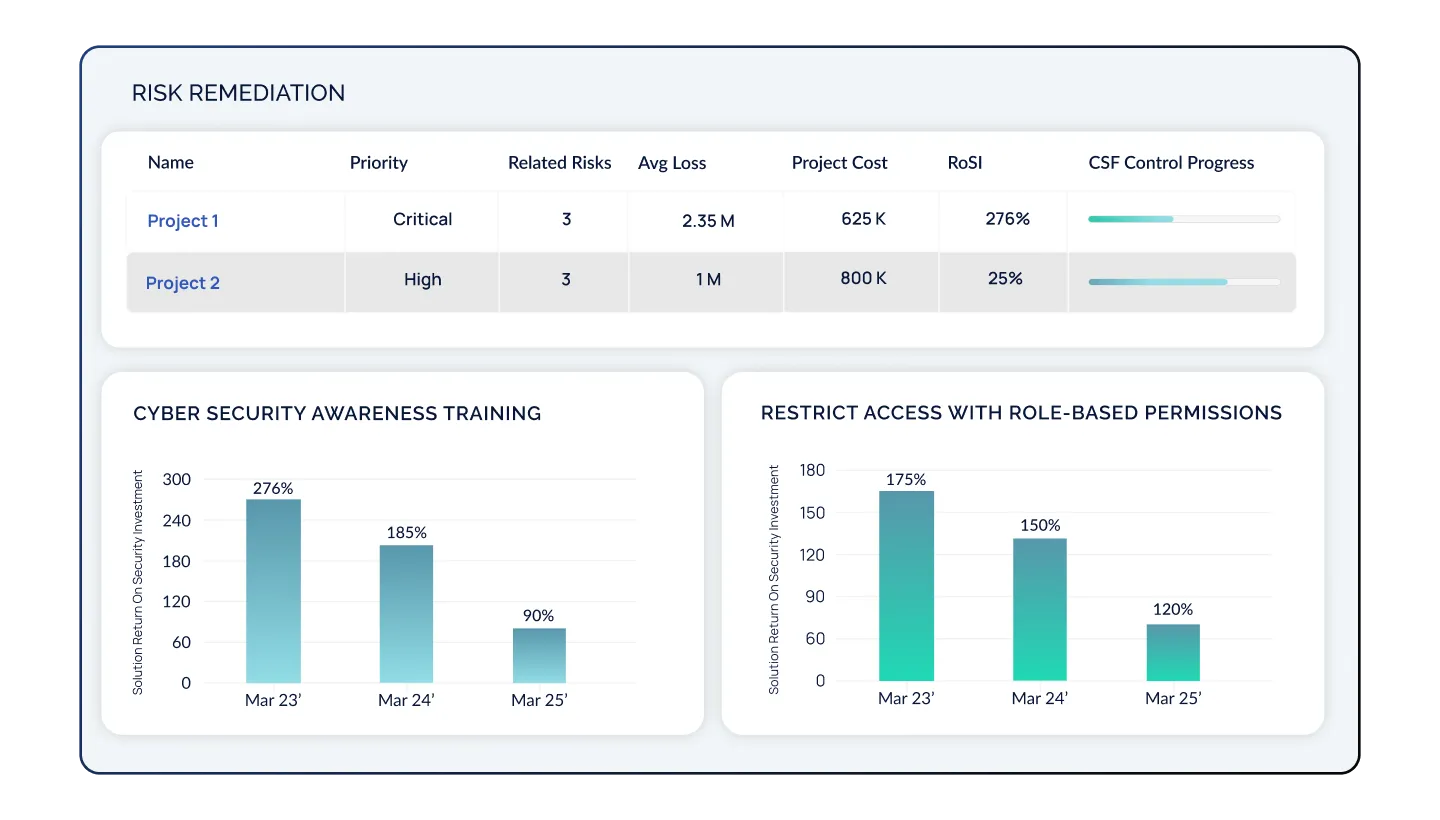
Executive Dashboarding & Boardroom Storytelling
The Executive Dashboard enables CISOs to present a compelling narrative about the business impact of cybersecurity. Communicate the financial implications of cyber risks, how your posture compares to your peers, remediations in progress, justify spend, and influence decisions at the highest levels.
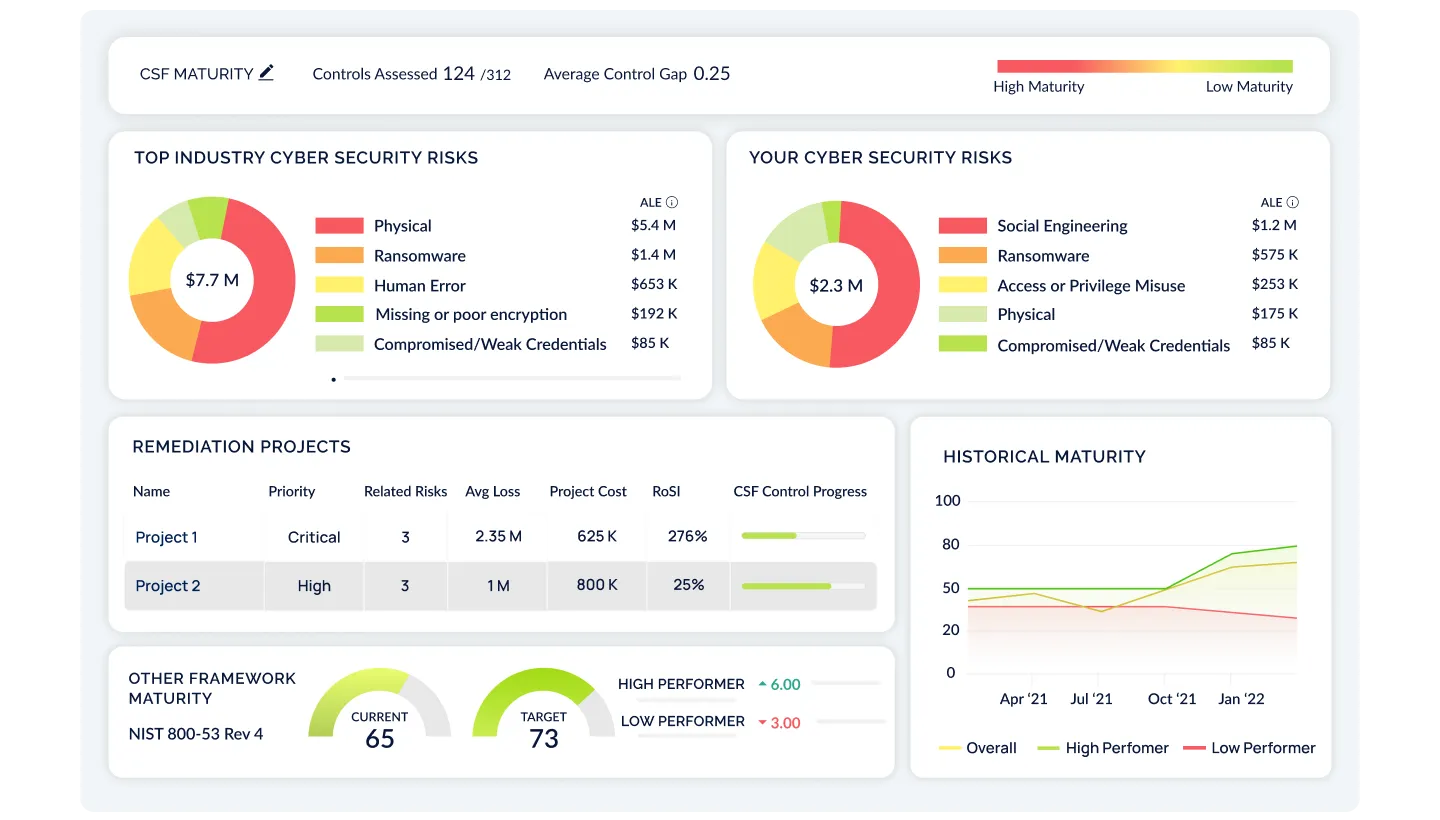
Benchmarking Backed by the Largest Cyber Loss Dataset
CyberStrong's industry risk capability leverages the world's largest dataset of cyber loss data, updated monthly, to provide tailored risk insights. Identify and prioritize the top cyber risks specific to your industry, company size, and revenue, ensuring a targeted and effective risk management and compliance strategy backed by data.

AI-Powered Prioritized Findings
Backed by CyberSaint AI, security leaders and their teams see findings in context - now, the top priorities are not lost in a notification deluge. See the threats that matter mapped to tracked controls and risks dynamically.

Automated Control Monitoring & Agentic Evidence Collection
Compliance remains a massive tax on security teams. CyberStrong automates multiple aspects of the assessment process: technical control scoring using Continuous Control Monitoring, evidence collection using computer vision-based agents, and NLP-based crosswalking to map controls based on intent. All combining to deliver a real-time view of compliance posture while reducing manual effort by over 70%.

Dynamic Risk Register & Cyber Risk Quantification
CyberStrong makes cyber risk quantification transparent, scalable, and easy to deploy, offering various models such as FAIR and NIST 800-30. The Risk Register offers customizable heat maps, financial impact charts, and additional features to help you transfer, avoid, accept, or mitigate risk. Streamline the process of identifying, quantifying, and prioritizing cybersecurity initiatives, which spurs action and allows you to close gaps with confidence.

ROSI Calculation & Scenario Analysis
CyberStrong's Remediation Suite offers a robust set of tools for tracking remediation efforts and their impact on your cyber risk posture. This approach encompasses cost simulations, Return on Security Investment (RoSI) analysis, and project timeline forecasting, facilitating informed decision-making on the optimal strategies to reduce your cyber risk exposure.

Executive Dashboarding & Boardroom Storytelling
The Executive Dashboard enables CISOs to present a compelling narrative about the business impact of cybersecurity. Communicate the financial implications of cyber risks, how your posture compares to your peers, remediations in progress, justify spend, and influence decisions at the highest levels.


Powered by CyberSaint AI
Curious how we're automating cyber risk management at enterprise scale? It's not just APIs and workflow. Learn about our AI-native approach and where we're headed.
Delivering Tangible Results for Industry Leaders
Take your cyber risk management program from point-in-time to real-time with proven technology that delivers unquestionable value
Unlock Increased Value as Your Program Matures
CyberStrong is designed to grow with you. Get instant results by starting with the software package that aligns with your immediate needs and unlock functionality as your strategy evolves.
Compliance Hub
Risk Hub
Executive Hub
Compliance Hub
The most basic CyberStrong package, built to address risk-based compliance management.
- Uncover what top cyber risks impact your business, and use these insights to inform your control assessment strategy
- Access a flexible controls library, hundreds of frameworks, and perform assessments
- Harmonize frameworks with AI-powered automated crosswalking to "assess once, use many"
- Leverage flexible dashboards and reports to track trends over time, gap-to-goal analysis, and view compliance by geography, business unit, assets, and more
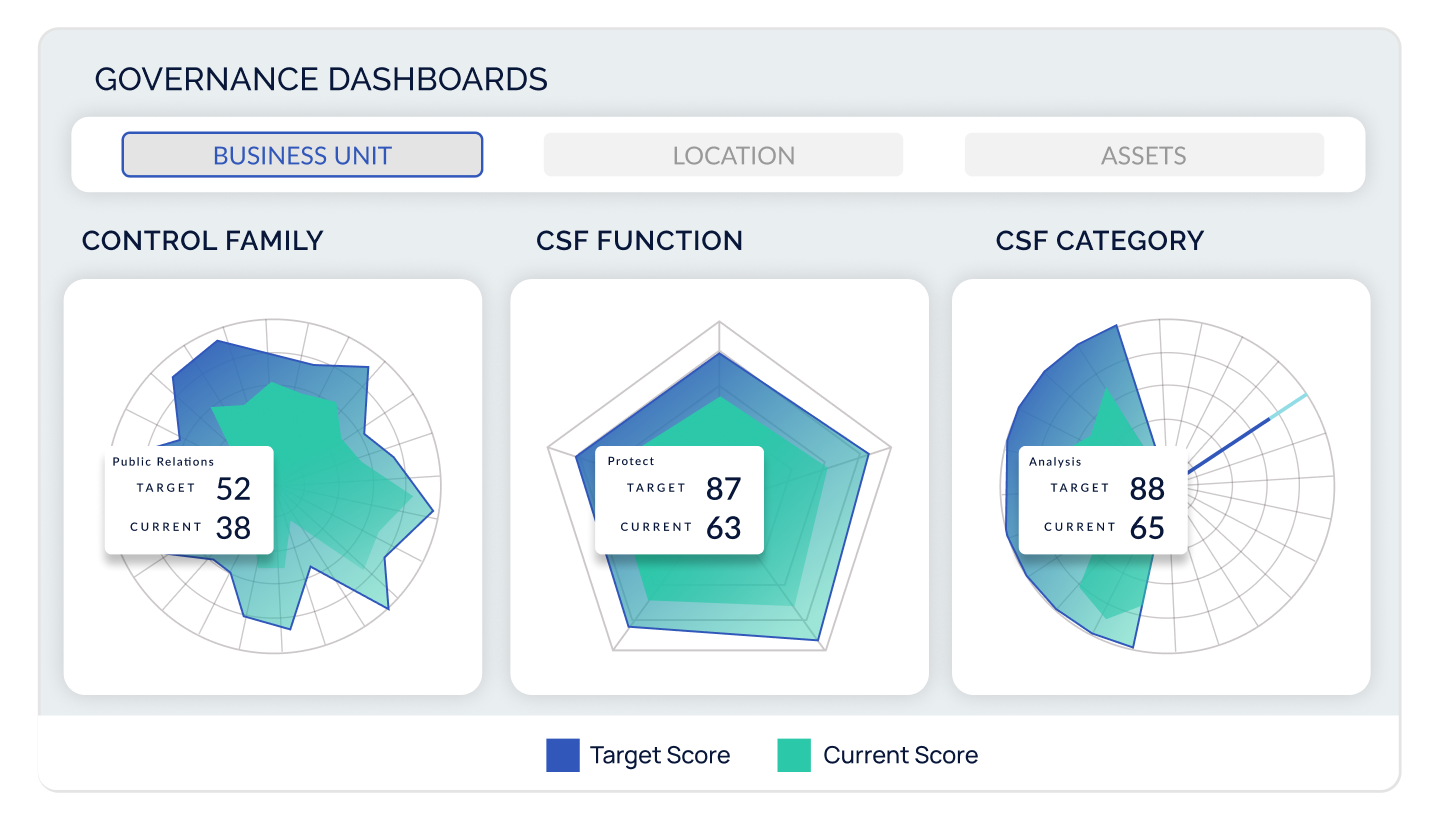
Risk Hub
Designed to connect the dots between controls, risks, and finance, the Risk Hub includes everything in the Compliance Hub plus the ability to:
- Tie control groups from assessments and frameworks you are already tracking to risks in an intuitive risk register
- Benchmark your top risks versus those of your peers based on industry, company size, and revenue
- Quantify risk into financial metrics with transparent models such as FAIR and NIST 800-30, designed for rapid implementation and scalability
- Customize heat maps, risk dashboards, and reports to view risk from any angle

Executive Hub
Our most robust package, the Executive Hub elevates the cyber risk conversation. Leverage everything offered in the Risk Hub, plus the ability to:
- Present cyber risk initiatives in a business context, making complex cyber risk data accessible and understandable to non-technical stakeholders, regulators, and cross-functional teams, especially the C-Suite and Board
- Influence budgeting decisions by modeling out security investments with clear remediation project timelines, tracking, and ROI analysis
- Refine and optimize your cyber risk strategy as new controls or risks are added, uncovering new opportunities for risk remediation, budget unlock, and value creation on an ongoing basis
Becoming CyberStrong
CyberStrong has transformed our approach to cyber risk management. The real-time insights and automated assessments have not only streamlined our processes and saved costs but have also significantly enhanced our decision-making capabilities. I feel confident justifying the dollars in my budget towards key initiatives, because I can quantify the impact we're making.
Thanks to CyberStrong, we can now present our cybersecurity strategy and its financial implications to our executives in a language they understand. This has significantly improved executive buy-in and the maturity of our cyber practice.
The SEC requirements have elevated the conversation around cyber risk to the Boardroom. CyberSaint’s platform not only hits on the need for increased automation at the foundational compliance level, but also the need to link controls to risks to make cyber risk management real-time. Companies now can have a clear understanding of their cyber risk posture and optimize accordingly based on their most likely cyber losses, risk mitigated, and ROSI. Translating cyber risk into financial terms is a game-changer for C-suites and Boards, and CyberSaint has cracked the code on rapid time to value and scalability for enterprise cyber risk quantification. The CyberStrong platform is a powerful solution for every enterprise CISO looking to master their cyber risk posture.
CyberStrong has transformed our approach to cyber risk management. The real-time insights and automated assessments have not only streamlined our processes and saved costs but have also significantly enhanced our decision-making capabilities. I feel confident justifying the dollars in my budget towards key initiatives, because I can quantify the impact we're making.
Thanks to CyberStrong, we can now present our cybersecurity strategy and its financial implications to our executives in a language they understand. This has significantly improved executive buy-in and the maturity of our cyber practice.
The SEC requirements have elevated the conversation around cyber risk to the Boardroom. CyberSaint’s platform not only hits on the need for increased automation at the foundational compliance level, but also the need to link controls to risks to make cyber risk management real-time. Companies now can have a clear understanding of their cyber risk posture and optimize accordingly based on their most likely cyber losses, risk mitigated, and ROSI. Translating cyber risk into financial terms is a game-changer for C-suites and Boards, and CyberSaint has cracked the code on rapid time to value and scalability for enterprise cyber risk quantification. The CyberStrong platform is a powerful solution for every enterprise CISO looking to master their cyber risk posture.
RESEARCH SPOTLIGHT
Gartner® Hype Cycle™ for Cyber-Risk Management, 2025
Explore the future of cyber-risk management with the latest Gartner Hype Cycle, recognizing CyberSaint as a Sample Vendor for Cyber GRC for the second consecutive year. Cyber GRC is a strategic approach that uses specialized tools to help businesses meet security requirements, manage risks, and comply with regulations. By adopting this technology, security and risk leaders can streamline cybersecurity governance by consolidating fragmented cyber risk data, enabling faster and more effective risk management decisions.
Gartner, a company that delivers actionable, objective insight to executives and their teams, brings you in-depth research on Cyber GRC. This method focuses on real-time risk management and a proactive approach to security, keeping your organization one step ahead of potential threats.
CYBERSTRONG PLATFORM DEMO
See CyberStrong in Action
CyberStrong is built on the principles of innovation, simplicity, and effectiveness, empowering you to continuously optimize your cyber posture with data-driven insights. We're excited to meet you!
What to expect:
-
Customer-Centric Discovery: This time is yours. We start by listening to you—understanding your unique challenges and goals. This enables us to propose solutions that can meet the specific needs of your industry and organization.
-
Interactive Platform Walkthrough: Get hands-on experience with our platform, from control automation to cyber risk quantification. See firsthand how CyberStrong turns complex cyber risk and compliance data into action.
-
Expert Guidance: Engage with our experts who will be available to answer your questions, discuss best practices used by our customers, and show you how CyberStrong integrates with your existing security infrastructure to enhance your cyber resilience.
What the community is saying...
The CyberStrong platform is a powerful solution for every enterprise CISO looking to master their cyber risk posture.




