ADVANCE YOUR STRATEGY
CyberStrong
Risk Hub
Holistically manage every aspect of your cyber risk program from automated risk assessment to credible cyber risk quantification
CyberStrong Risk Hub
The CyberStrong Risk Hub revolutionizes how organizations identify and compare risks against industry benchmarks while quantifying cyber risk into financial terms
-1.webp)
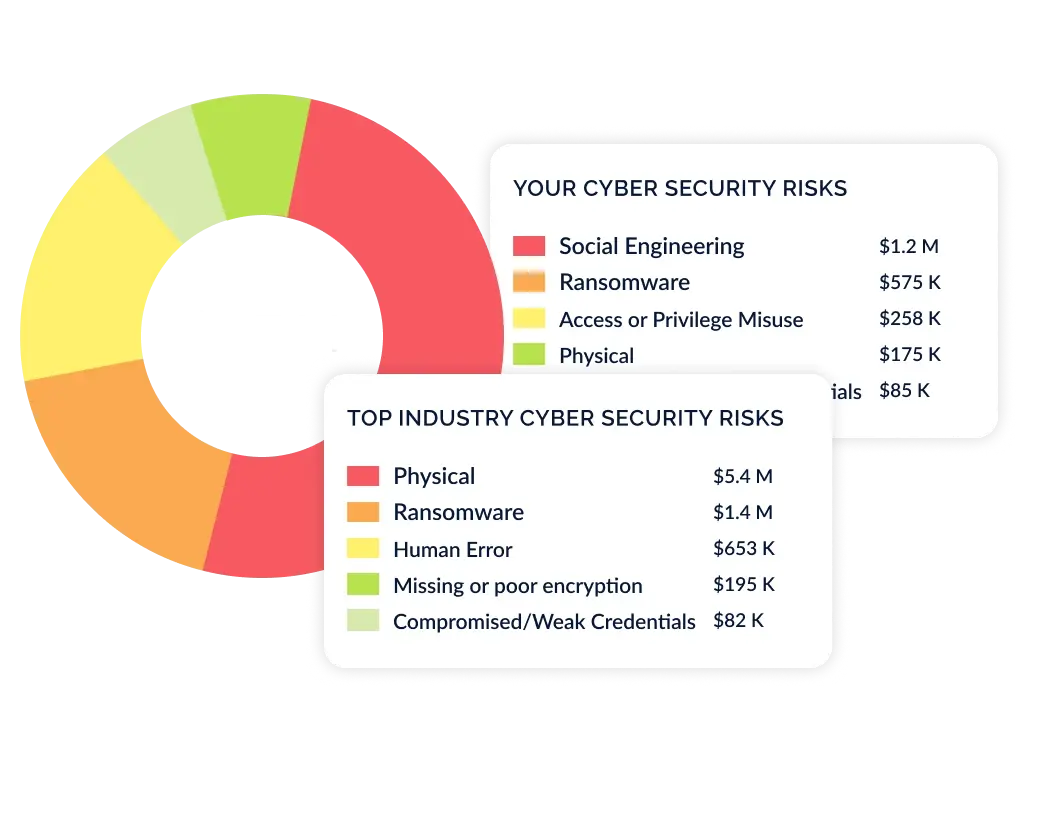
Identify Your Top Risks
Streamline your cyber risk management strategy by benchmarking your risk profile against your peers. Uncover critical risks and enhance your approach by comparing annualized loss expectancies to prioritize your cybersecurity initiatives.
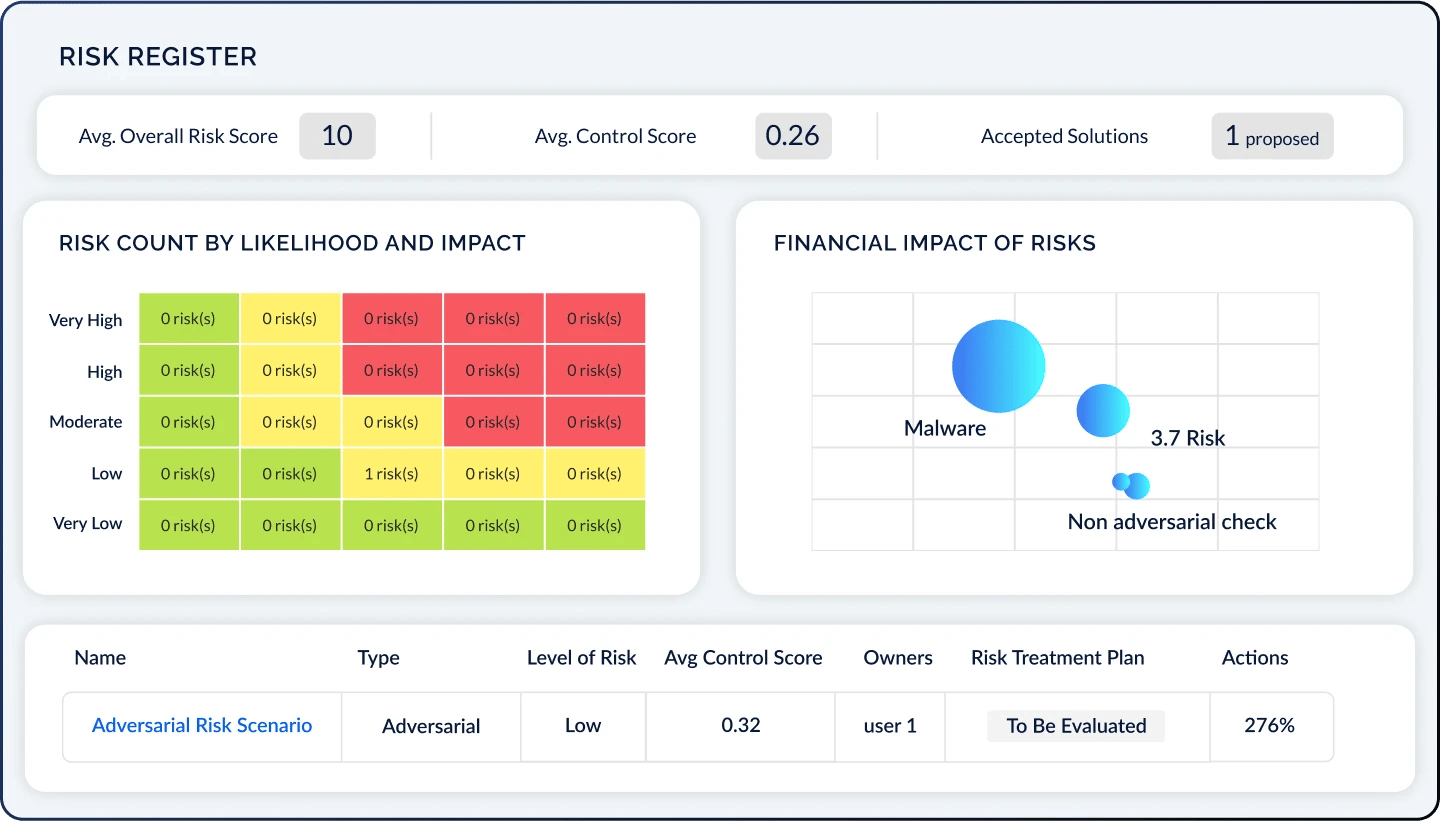
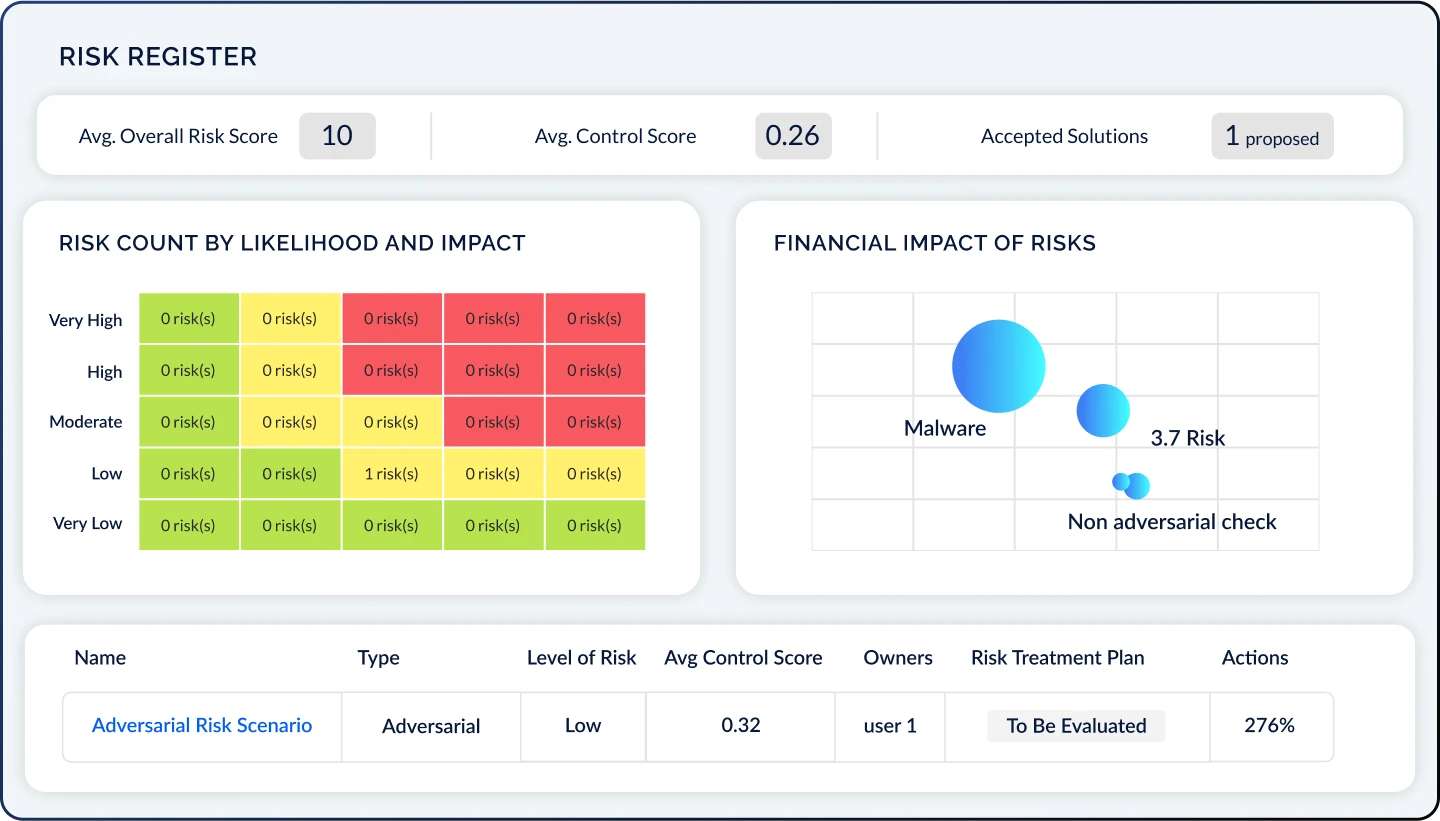
Initiate Proactive Action
Respond to risks and track risk acceptance, transfer, mitigation, and avoidance through an intuitive Risk Register. Illustrate your unique cyber risk posture with customizable heat maps, financial impact charts, and risk scenario modeling.
-1.png)
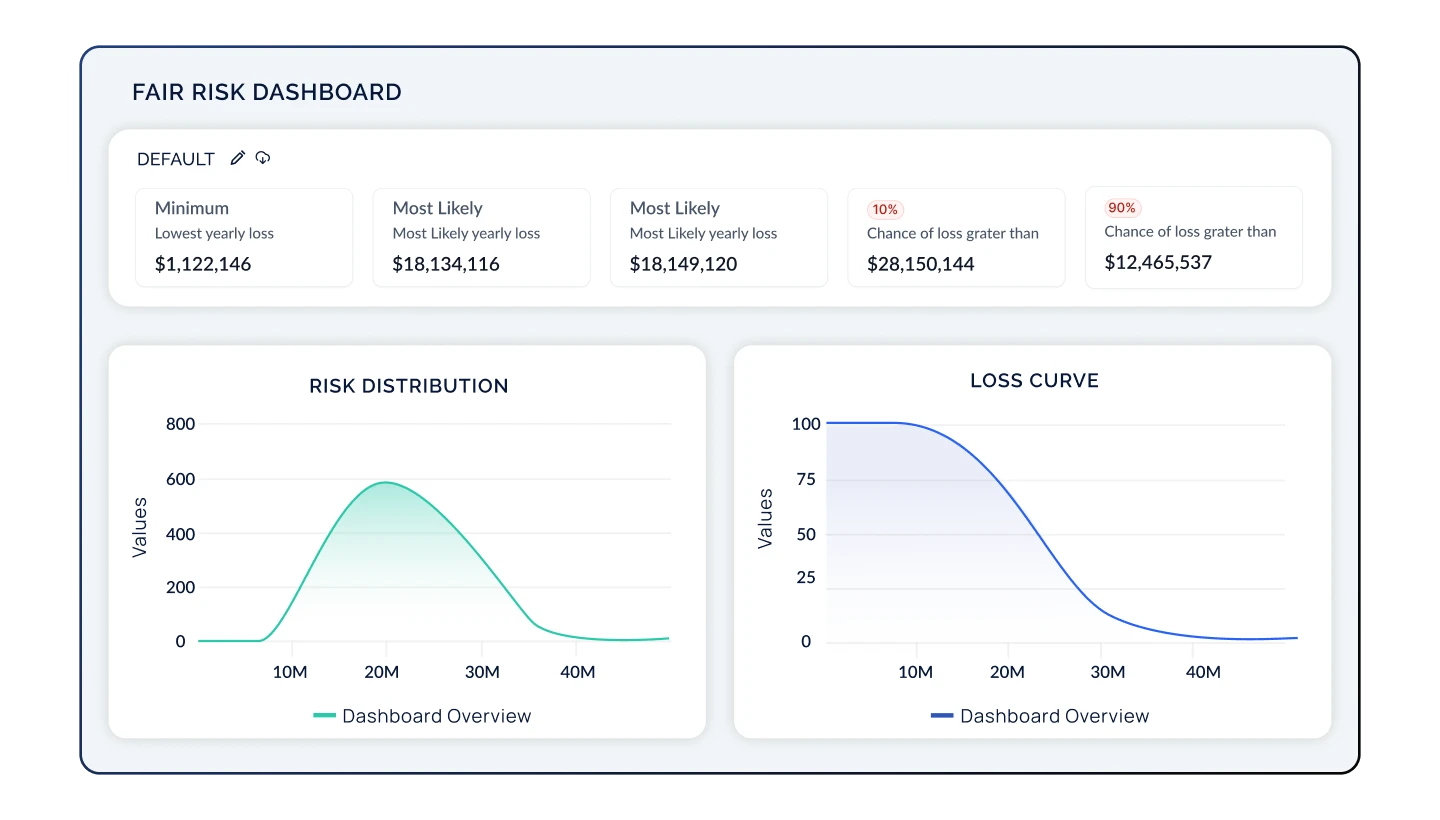
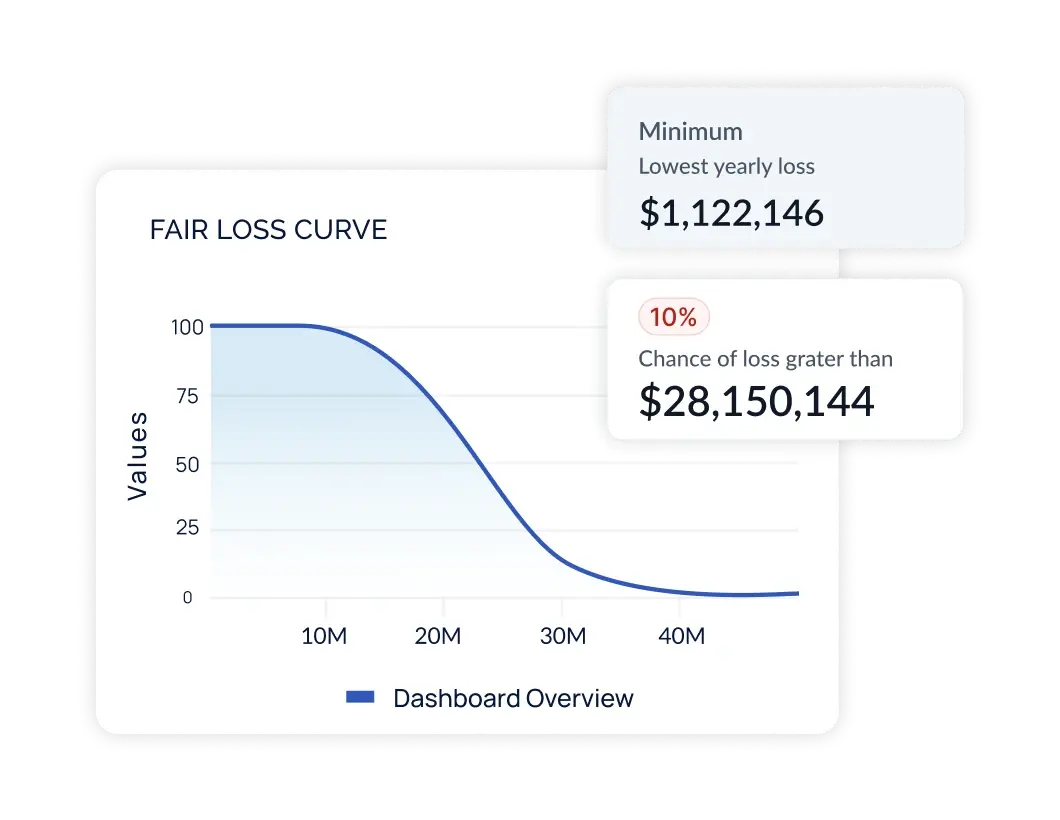
Financialize Your Cyber Risk Posture
Translate risks into financial terms to align cybersecurity initiatives with impacts on the bottom line. Implement the FAIR model, NIST 800-30, or other cyber risk quantification models easily and transparently with the ability to customize and scale.
Build an Interconnected Narrative
Tell the story of your cybersecurity program in a way that everyone can get behind by balancing quantitative and qualitative insights. Link cyber program components to weave a holistic story, illustrating the impact of controls on risks and investments on business impacts.
CYBER RISK INSIGHTS
Unlock the Combined Power of CCM + CRQ
Vendors tend to focus on either automation or quantification, but don't address both use cases. Consequently, CISOs end up investing in multiple tools to achieve mediocre results. CyberSaint recognizes the demand for a fully integrated platform that scales across numerous use cases, including Continuous Control Monitoring (CCM) and Cyber Risk Quantification (CRQ).
CCM offers real-time insights into control posture, aligning with key frameworks to ensure security controls are continuously scored and optimized. Coupled with CRQ, organizations can quantify risks, providing a clear view of potential financial impacts and enabling leadership discussions. This approach avoids the need for multiple point solutions and offers a credible, transparent approach to cyber risk management that is easily understood by leadership.
Becoming CyberStrong
Implementing CyberStrong was a game-changer for us. The platform's intuitive risk register and executive dashboards provided the clarity and precision we needed to communicate our cyber risk posture effectively to our board.
The SEC requirements have elevated the conversation around cyber risk to the Boardroom. CyberSaint’s platform not only hits on the need for increased automation at the foundational compliance level, but also the need to link controls to risks to make cyber risk management real-time. Companies now can have a clear understanding of their cyber risk posture and optimize accordingly based on their most likely cyber losses, risk mitigated, and ROSI. Translating cyber risk into financial terms is a game-changer for C-suites and Boards, and CyberSaint has cracked the code on rapid time to value and scalability for enterprise cyber risk quantification. The CyberStrong platform is a powerful solution for every enterprise CISO looking to master their cyber risk posture.
The Continuous Controls Automation feature within CyberStrong has drastically reduced the time and effort required for compliance assessments. It's like having an extra team dedicated to ensuring our controls are always up to date.
Implementing CyberStrong was a game-changer for us. The platform's intuitive risk register and executive dashboards provided the clarity and precision we needed to communicate our cyber risk posture effectively to our board.
The SEC requirements have elevated the conversation around cyber risk to the Boardroom. CyberSaint’s platform not only hits on the need for increased automation at the foundational compliance level, but also the need to link controls to risks to make cyber risk management real-time. Companies now can have a clear understanding of their cyber risk posture and optimize accordingly based on their most likely cyber losses, risk mitigated, and ROSI. Translating cyber risk into financial terms is a game-changer for C-suites and Boards, and CyberSaint has cracked the code on rapid time to value and scalability for enterprise cyber risk quantification. The CyberStrong platform is a powerful solution for every enterprise CISO looking to master their cyber risk posture.
The Continuous Controls Automation feature within CyberStrong has drastically reduced the time and effort required for compliance assessments. It's like having an extra team dedicated to ensuring our controls are always up to date.
Unlock More Value From CyberStrong
CyberStrong is designed to meet you at your current stage and grow with you
Compliance Hub
The foundational Hub of CyberStrong, leverage the CyberStrong Compliance Hub to identify risks and related controls, perform assessments against frameworks and standards, harmonize regulations with automated crosswalking, and view compliance from any angle.
learn moreExecutive Hub
Everything in the Risk Hub, plus a robust Remediation Suite and compelling Executive Dashboard. Compare and track remediation projects, risk buy-down, and ROSI. Articulate your cyber posture compared to your peers and ensure impact and severity of cyber risks is understood.
learn moreCompliance in Motion
Incorporate Continuous Control Automation™ into any CyberStrong Hub and replace manual processes with AI-powered, real-time compliance
Continuous Control Automation™
Score controls automatically as data in your security tech stack changes, moving from point-in-time assessment to real-time assessment
Learn MoreFeatured Resources
Discover the essentials of cyber risk management and enhance your expertise

2025 Gartner® Hype Cycle™ for Cyber-Risk Management

AI-Powered Findings Management Solution Brief

Key Takeaways from Gartner's Market Guide for TPRM Technology Solutions
CYBERSTRONG PLATFORM DEMO
See CyberStrong in Action
CyberStrong is built on the principles of innovation, simplicity, and effectiveness, empowering you to continuously optimize your cyber posture with data-driven insights. We're excited to meet you!
What to expect:
-
Customer-Centric Discovery: This time is yours. We start by listening to you—understanding your unique challenges and goals. This enables us to propose solutions that can meet the specific needs of your industry and organization.
-
Interactive Platform Walkthrough: Get hands-on experience with our platform, from control automation to cyber risk quantification. See firsthand how CyberStrong turns complex cyber risk and compliance data into action.
-
Expert Guidance: Engage with our experts who will be available to answer your questions, discuss best practices used by our customers, and show you how CyberStrong integrates with your existing security infrastructure to enhance your cyber resilience.
What the community is saying...
The CyberStrong platform is a powerful solution for every enterprise CISO looking to master their cyber risk posture.






.png)
