CISOs and Board Members can no longer ignore the importance of cybersecurity. New cyber attacks and threats surface every week and threaten the security of business operations. Non-technical teams and leadership must learn and invest in cybersecurity actively. Cyber can no longer be thought of as a siloed process. At the board level and among other non-technical leaders, cyber investment and interest are necessary for a business’s success and continuity.
With cybersecurity as a board-level issue, many CISOs face the same inquiry and scrutiny as a CFO or CEO. Cyber is no longer an abstract concept that can be assessed with “Are we secure?” and a brief “Yes.” Successful CISOs are leaders, communicators, and managers. All CISOs must be prepared to convey their organization's progress to ensure business continuity, make informed decisions, and improve cybersecurity incident response plans.
When a CISO reports to the Board of Directors, it is their responsibility to communicate the organization’s security posture, risks, and the potential impact of future threats. To do this, CISOs must avoid technical details and cyber jargon to avoid confusing non-technical board members. The CISO’s cybersecurity board report should include proposed solutions and the potential impact of time and money on cybersecurity programs.
Read below to learn how to structure your CISO Board report template.
Template for Your Cybersecurity Board Report
Report Contextually on Company Security Posture
It is impossible to achieve 100% security and business growth within an organization. Growth and risk go hand in hand. A CISO must communicate this so the board understands that certain risks are associated with business growth and are necessary to absorb to grow the business.
The CISO should communicate that risk should be viewed through the lens of good vs. bad instead of high vs. low - good risk is associated with risk that can grow the business. CISOs should consider communicating this through a risk appetite statement. A risk appetite statement defines the amount of risk an organization can take to pursue its goals. In doing so, security initiatives should be considered part of business objectives. As an organization grows, the business needs to accept certain risks for growth.
Overview of the Company’s Cybersecurity Posture
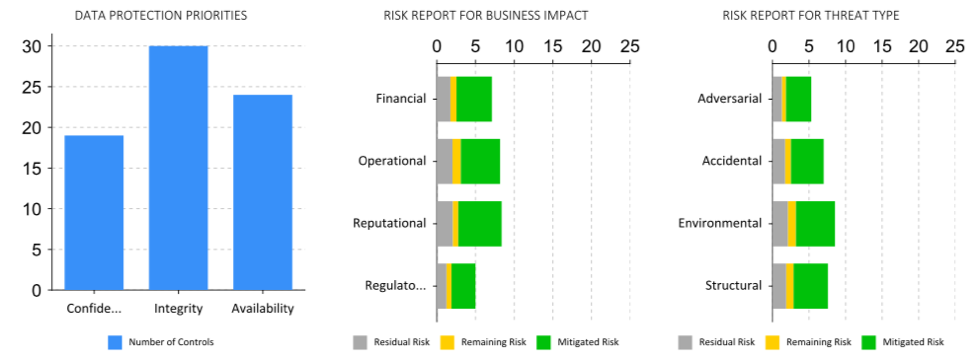
As board members become more interested in cybersecurity, the CISO needs to provide information on the company's most critical security threats and risks, the controls in place, how things can change over time, and proposed solutions. CISOs can convey this information through an Executive Risk Report, a high-level overview of the company’s risk. This risk report can give an overview of the organization's overall risk and illustrate alignment with the risk appetite statement.
The CyberStrong platform offers an Executive Risk Report that visualizes risk by threat type and business impact. This risk report also delivers a risk report breakdown for control families. A CyberStrong Executive Risk report includes a more granular analysis of the control family's risk posture by breaking the categories of risk down into three groups: inherent risk (total risk by family), residual risk (a risk that remains after some implementation of controls), and opportunity (the amount of risk that remains to be mitigated). These easy-to-use visualizations help you centralize and focus your top cybersecurity metrics for board reporting.
Financialize Cyber Risk with the FAIR Model
The FAIR model measures risk by financial impact. By translating quantified risk into monetary terms, board members and non-technical stakeholders can better understand risk. Presenting cyber risk in a business context will encourage executive buy-in and demonstrate the impact of time and money on cybersecurity and operational risk.
The CyberStrong platform allows users to quantify risk via the FAIR model. Using the risk register, CISOs can display the financial impact of risk using a graphical representation of a Monte Carlo simulation with an identified risk.
Leverage a Cybersecurity Board Reporting Dashboard
CISOs can display real-time information using dashboards. CyberStrong offers users updated Governance Dashboards to show updates on their security program. Governance Dashboards are business-friendly visualizations of compliance and risk initiatives that combine quantitative and qualitative methods to allow CISOs to give meaningful metrics to CEOs and the board.
Governance Dashboards enable a seamless flow of information up and down the chain of command. View compliance posture by business unit, geography, site, vertical, or any other tagging taxonomy in addition to year-over-year comparisons. These dashboards can also display where weaknesses exist in the organization. CyberStrong’s Risk Dashboard and NIST CSF Scorecard illustrate the Return on Security Investment (RoSI), where the spending goes, and the impact on the organization's risks.
Streamline Your Cybersecurity Board Report
CISOs must clearly and cohesively report on cybersecurity to the Board to secure buy-in and meet SEC Reporting Requirements. Cyber is a critical business function. Therefore, a CISO must use the right tools to communicate an organization’s cyber posture. FAIR risk quantification frames cyber in a financial context, and dashboards help visualize and synthesize cyber initiatives to better understand them.
Contact us to learn more about improving your cybersecurity board report for board meetings with CyberStrong.
FAQ: Cybersecurity Board Report
What is a CISO report template?
A CISO report template is a structured format that helps Chief Information Security Officers effectively communicate cybersecurity posture, risks, and program progress to executive leadership and board members. It typically includes a summary of key threats, control status, cyber risk quantification, incident response readiness, and alignment with business goals.
Why do I need a cybersecurity board report template?
A cybersecurity board report template enables CISOs to present complex security information in a clear, business-relevant format. With cybersecurity now a board-level issue, it's essential to align cyber risk with business priorities, demonstrate ROI, and provide executive decision-makers with actionable insights.
What should be included in a cybersecurity board report?
Your cybersecurity board report template should include:
-
An overview of the organization’s current cybersecurity posture
-
Key threats and vulnerabilities
-
Status of critical controls
-
A risk appetite statement
-
Quantified risks using models like FAIR
-
Visualizations via dashboards (e.g., risk heatmaps, RoSI metrics)
-
Proposed investments and their projected impact on risk reduction
How does the FAIR model help improve my CISO board report?
The FAIR (Factor Analysis of Information Risk) model helps CISOs financialize cyber risk, making it easier for board members to understand threats in terms of dollars and business impact. Integrating FAIR into your CISO report template provides clarity and enables better risk-based decisions.
Can dashboards be included in a CISO board report?
Yes. Dashboards are a powerful way to enhance your CISO report template. Tools like CyberStrong offer Governance Dashboards that visualize compliance and risk metrics in real time, helping boards quickly grasp where the organization stands and what actions are needed.
How can I streamline my cybersecurity board reporting process?
Use a cybersecurity platform like CyberStrong to:
-
Automate data collection and analysis
-
Quantify cyber risk with FAIR or NIST 800-30
-
Generate executive-ready risk reports
-
Leverage Governance Dashboards for real-time metrics
This approach reduces manual work and improves the consistency and quality of your cybersecurity board report template.





.png)
.png)
.png)
%201.png)
.png)