Audit software is a type of cybersecurity application that helps to improve and automate the audit process. Cybersecurity audit software can also be used to generate reports that can be used to demonstrate compliance with industry regulations. Cybersecurity audit software can be used by organizations of all sizes, from small businesses to large enterprises. It is an essential tool for any organization that wants to protect its data and systems from cyberattacks.
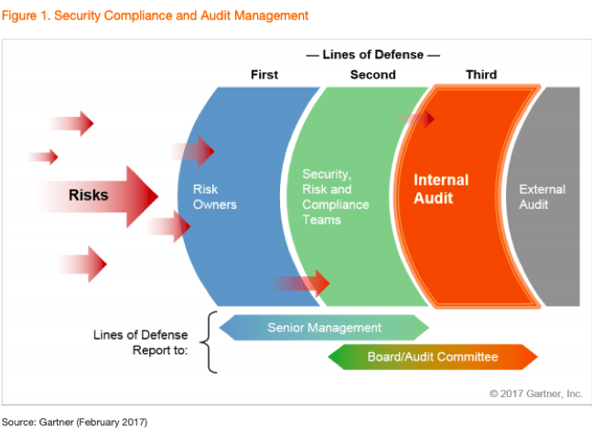
Comparable to typical accounting software, audit software is generally used to help evaluate and test accounting procedures. Others are developed to collect proof, perform analytical tests, and assess in-house control. There are more robust programs that integrate all of these functionalities into one package.
Copyright © 2026 CyberSaint Security. All Rights Reserved. Privacy Policy.