As many organizations mature their cybersecurity program, they shift to a risk-based approach to advance their security and privacy controls. In most cases, security leaders are no strangers to leveraging risk management processes to complement the regulations and compliance standards to improve security status.
The NIST management framework is a culmination of multiple special publications produced by the National Institute of Standards and Technology (NIST). As we’ll see below, the 6 NIST RMF Steps—Step 1: Categorize/ Identify, Step 2: Select, Step 3: Implement, Step 4: Assess, Step 5: Authorize, and Step 6: Monitor—uniquely lend themselves to a given NIST special publication (e.g., NIST SP 800-37 and NIST SP 800-53).
Risk Management Framework Steps
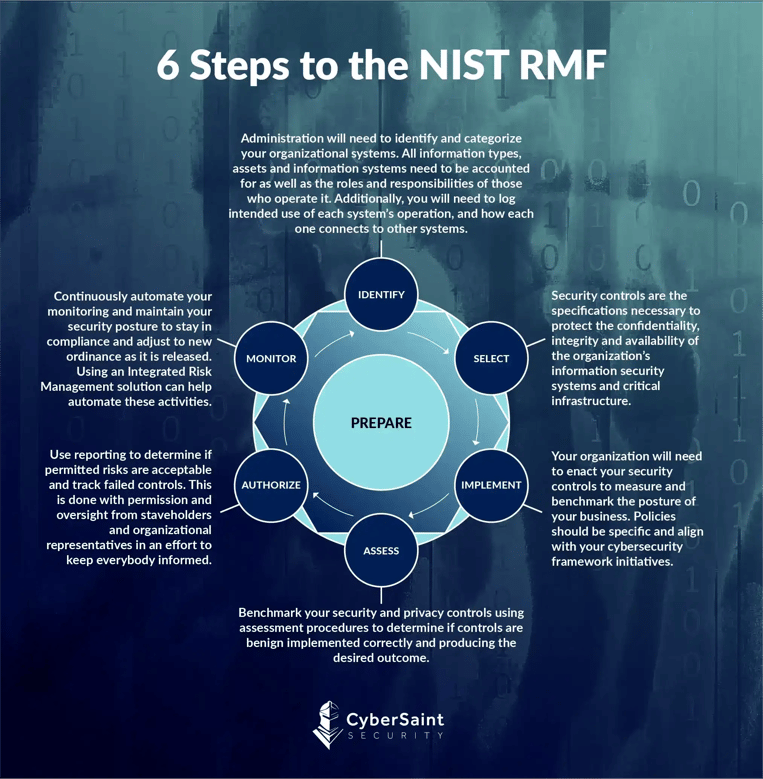
To begin aligning with business objectives, information security leaders must embrace the language and, to an extent, the business processes that other business units have been practicing for years. Information systems and organizations have operated in a siloed function for years. Yet, with the increased concern from CEOs and Boards, CISOs must now prepare steps to communicate organization-wide cybersecurity risk in the same way that the CFO and COO present financial and operational risk, respectively.
NIST Risk Management Framework
While the RMF 6 Step Process and the supporting NIST publication were designed to secure federal agencies and federal information systems, similar to the NIST CSF, the gold standard that these cyber risk management frameworks have set has proven to be of great value to private sector organizations as well to support security control assessments and determining a control baseline to direct system security investments moving forward.
Throughout the information system-based development life cycle, ensuring the risks associated with a given strategy and effectively communicating that information to both technical and business-side stakeholders is critical. Security teams can use the NIST RMF for continuous monitoring, risk identification, risk assessments, and flagging potential security issues. NIST SP 800-37 is a guideline for applying the RMF to federal information systems. The RMF can also quantify and manage your organization's risks so that management understands and empowers your security leadership team.
What is NIST 800-37?
The NIST RMF, also known as NIST SP 800-37, is a methodology for building a risk management framework; it is not a ready-made risk management program. According to NIST, "The RMF provides a disciplined, structured, and flexible process for managing security and privacy risk that includes information security categorization; control selection, implementation, and assessment; system and common control authorizations; and continuous monitoring. The RMF includes activities to prepare organizations to execute the framework at appropriate risk management levels."
The CyberStrong platform is built on gold-standard cybersecurity risk management frameworks to enable success for practical risk management activities and to achieve and maintain a continuous monitoring program and compliance using frameworks like the NIST Cybersecurity Framework and Risk Management Framework. Request a demo with the CyberSaint team if you have questions about the NIST RMF or any other security and risk questions.





.png)
.png)
.png)
%201.png)
.png)




