The industry data security standard for PCI DSS compliance - Payment Card Industry Data Security Standard (PCI DSS) - is not new for organizations dealing with credit card data. As cash is used less and less and businesses of all sizes embrace e-commerce, securing payment information has never been more important. From multi-factor authentication to reporting for service providers, there's a wealth of requirements for data security for those in the payment card industry to comply with and monitor. Especially for big brands or upcoming businesses with lots of momentum, becoming the focus of another Target credit card scandal is not on anyone's wishlist. The fear of being the next big scandal is why PCI DSS compliance is so important and why you and your team should take your PCI security assessment and compliance auditing seriously. PCI compliance tools - most often those that help to accelerate governance, risk, and compliance activities in addition to PCI DSS compliance - help to keep all of these requirements measured, monitored, and on track with program objectives.
According to the PCI Security Standards Council, "PCI security standards are technical and operational requirements set by the PCI Security Standards Council (PCI SSC) to protect cardholder data. The standards apply to all organizations that store, process, or transmit cardholder data – with guidance for software developers and manufacturers of applications and devices used in those transactions. The Council is responsible for managing the security standards. In contrast, compliance with the PCI set of standards is enforced by the founding members of the Council, American Express, Discover Financial Services, JCB International, MasterCard, and Visa Inc."
Some key PCI DSS compliance requirements included in a typical self-assessment questionnaire (SAQ) are on the checklist below, including guidelines and remediation steps. These functions can be accelerated using tools for PCI compliance standards that help automate governance, risk, and compliance activities.
Achieve PCI Compliance
The goal of the prioritized approach is to help develop a roadmap that an organization can use to address its risks in priority order that empowers a pragmatic approach that allows for “quick wins” in milestone target controls, supports financial and operational planning in compliance efforts and ensures objective and measurable progress towards finalizing remaining compliance efforts, and helps promote consistency among assessors. PCI compliance tools help organizations achieve these goals and more, leveraging measurement, automation, visualization, and reporting to create a more proactive, manageable program whose value is understood by technical and non-technical leadership.
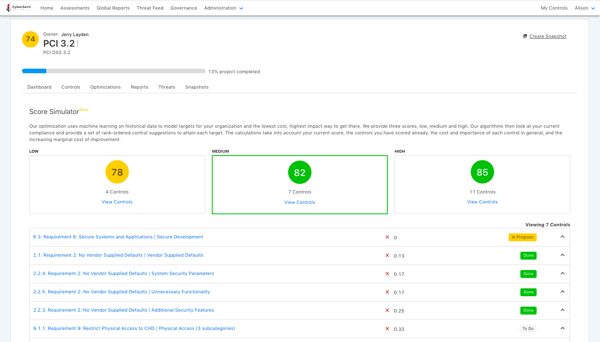
If you want to implement the Prioritized Approach to PCI DSS Compliance, CyberStrong can get you there with a systematic and optimized approach. CyberStrong uses credible risk data to help you prioritize your PCI control remediation plan. In addition, you'll get an AI-optimized roadmap that incorporates the controls within your existing gaps, presenting you and your team with the highest impact and lowest cost plan of action on how to proceed.





.png)
.png)
.png)
%201.png)
.png)




