Disrupting cybersecurity risk management
Leveraging powerful, patented automation, our intuitive software solutions empower businesses to protect their critical assets, employees, customers, and partners — so they can focus on what matters most.



Trusted by


.png?width=102&height=63&name=Mask%20Group%20(2).png)

.png?width=58&height=53&name=Mask%20Group%20(1).png)

.png?width=115&height=63&name=Mask%20Group%20(3).png)
Continuous Control Automation
Automate control compliance at scale with powerful, agile AI.
Learn MoreIntegrations
Integrate with your security and IT tech stack to facilitate real-time compliance and risk management.
Learn MoreAutomated Crosswalking
Project compliance posture across regulatory frameworks, industry standards, or custom control sets to reduce duplicate efforts.
Learn MoreExecutive & Board Reporting
Present actionable insights in terms that clearly illustrate cybersecurity posture.
Learn MoreCyber Risk Register
Identify and track all risks, impacts, and mitigations in a single location.
Learn MoreFrameworks & Standards
Align with key requirements and provide assurance across the enterprise.
Learn More
Cybersecurity Maturity Model Certification & DFARS
Meet the necessary requirements to do business in the Department of Defense supply chain.
Learn MoreNIST Ransomware Framework
Show due care by aligning with NIST’s guidance for ransomware risk management.
Learn MoreANALYST REPORT
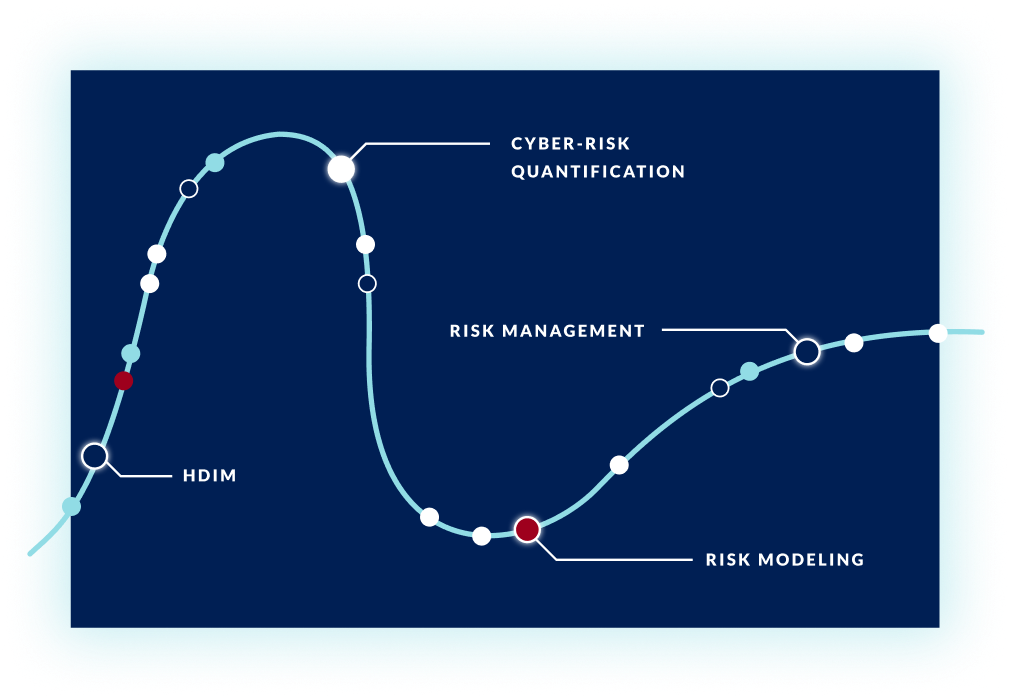
Gartner Hype Cycle for Cyber & IT Risk Management
Organizations around the world are reacting to an increase in cyber-attacks and new business challenges provoked by the realities of the pandemic. Security and Risk Management leaders can use Gartner's Hype Cycle to take a preventative approach to cybersecurity program management.

More Resources

Reports & E-Books
Gartner Cool Vendors in Cyber and IT Risk Management
What makes the CyberStrong platform new, innovative, and impactful? We believe in solving enterprise cybersecurity and IT risk management
Download Now
Reports & E-Books
The Integrated Risk Management Solutions Buying Guide
Gartner predicts that by 2021, 50 percent of large enterprises will use an IRM solution to provide
Download Now
Webinars & Videos
NIST's Golden Trio: The CSF, RMF, and Privacy Framework Unpacked
Learn how the NIST Privacy Framework is meant to be used, coupled with the NIST Cybersecurity
Watch Webinar
Information
The CyberStrong Platform Brochure
Learn how CyberStrong adds value to compliance and risk programs with its breakthrough integrated risk management capabilities in this
Download Now
Stay up to date
Join mailing list or subscribe to blog tagline aute in cillum dolore eu fugiat pariatur.