The Center for Internet Security (CIS) is a non-profit organization that develops best practices to improve Internet security and protect against security incidents.
The frameworks set forth by CIS affect everybody, from people to organizations and governments, and were created to create safe, reliable standards of protection for IT systems and cybersecurity programs from data breaches. The CIS Controls, formerly the CIS Top 20, make a strong foundation for a newly maturing cybersecurity program. Below, we explore the top 20 Critical Security Controls and their requirements.
In response to the changing technology, work, and threat landscape, The Center for Internet Security (CIS) has launched CIS Top 18 Controls (v8). This update has 18 key controls with 153 safeguards and addresses cloud and mobile technologies.
What Does CIS Stand For?
CIS stands for the Center for Internet Security. This organization aims to help businesses, people, and organizations protect themselves from cybersecurity threats.
The CIS Critical Security Controls
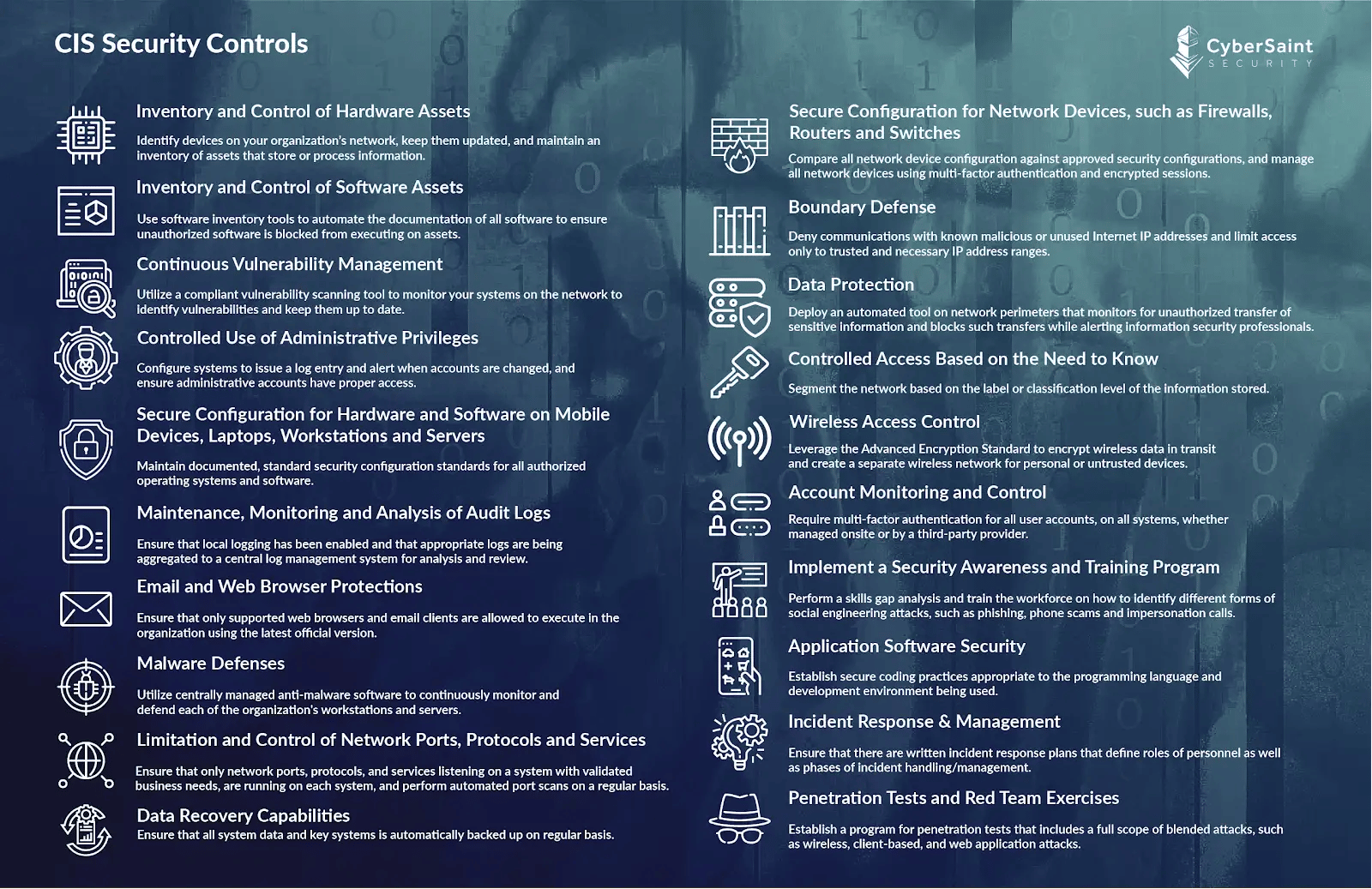
CIS Cybersecurity Controls
|
Inventory and Control of Hardware Assets |
Identify devices on your organization’s network, update them, and maintain an inventory of assets that store or process information. |
|
Inventory and Control of Software Assets |
Use software inventory tools to automate all software documentation to prevent unauthorized software from executing on assets. |
|
Continuous Vulnerability Management |
Utilize a complaint vulnerability scanning tool to monitor your systems on the network to identify vulnerabilities and keep them up to date. |
|
Controlled Use of Administrative Privileges |
Configure systems to issue log entries, alert when accounts are changed, and ensure administrative accounts have proper access. |
|
Secure Configuration for Hardware and Software on Mobile Devices, Laptops, Workstations, and Servers |
Maintain documented, standard security configuration standards for all authorized operating systems and software. |
|
Maintenance, Monitoring, and Analysis of Audit Logs |
Ensure that local logging has been enabled and appropriate logs are aggregated to a central log management system for analysis and review. |
|
Email and Web Browser Protections |
Ensure that only supported web browsers and email clients can execute in the organization using the latest official version. |
|
Malware Defenses |
Utilize centrally managed anti-malware software to continuously monitor and defend each organization's workstations and servers. |
|
Limitations and Control of Network Ports, Protocols, and Services |
Ensure that only network ports, protocols, and services listening on a system with validated business needs are running on each system, and perform automated port scans regularly. |
|
Data Recovery Capabilities |
Ensure that all system data and key systems are automatically backed up regularly. |
|
Secure Configuration for Network Devices, such as Firewalls, Routers, and Switches |
Compare all network device configurations against approved security configurations and manage all network devices using multi-factor authentication and encrypted sessions. |
|
Boundary Defense |
Deny communications with known malicious or unused Internet IP addresses and limit access to trusted and necessary IP address ranges. |
|
Data Protection |
Deploy an automated tool on network perimeters that monitors for unauthorized transfer of sensitive information and blocks such transfers while alerting information security professionals. |
|
Controlled Access Based on the Need to Know |
Segment the network based on the label or classification level of the information stored. |
|
Wireless Access Control |
Leverage the Advanced Encryption Standard to encrypt wireless data in transit and create a separate wireless network for personal or untrusted devices. |
|
Account Monitoring and Control |
Require multi-factor authentication (MFA) for all system user accounts, whether managed onsite or by a third-party provider. |
|
Implement a Security Awareness and Training Program |
Perform a skills gap analysis and train the workforce to identify social engineering attacks, such as phishing, phone scams, and impersonation calls. |
|
Application Software Security |
Establish secure coding practices appropriate to the programming language and development environment being used. |
|
Incident Response & Management |
Ensure written incident response plans define personnel roles and incident handling/management phases. |
|
Penetration Tests and Red Team Exercises |
Establish a program for penetration tests that includes a full scope of common attacks, such as wireless, client-based, and web application attacks. |
Gain insights on mapping the CIS Controls to NIST CSF here.
Understanding the CIS Critical Controls Framework
The CIS Critical Controls are a set of 20 security measures developed by cybersecurity experts worldwide. These controls are designed to mitigate the most prevalent cyber-attack vectors and provide a clear path toward a stronger security posture. Organizations implementing these controls can significantly reduce their cybersecurity risk.
The controls are organized into three implementation groups:
- Basic (IG1): Essential cyber hygiene for all organizations
- Foundational (IG2): Technical best practices for organizations with moderate complexity
- Organizational (IG3): Advanced capabilities for organizations with significant resources and expertise
Implementing CIS controls doesn’t need to be as daunting as it seems with the help of an automated risk assessment solution like CyberStrong. The CyberStrong platform can streamline and automate your compliance efforts with these 20 critical security controls and many other gold-standard frameworks, such as the NIST CSF, DFARS, and ISO 27001.
Schedule a conversation if you have any additional questions about the CIS cybersecurity controls, cyber risk management, or how CyberStrong can help bolster your cybersecurity and compliance objectives.
NIS2 is a growing requirement for organizations of all sizes and maturity. Get the latest insights on the NIS2 Directive Resources.





.png)
.png)
.png)
%201.png)
.png)




