The Department of Defense (DoD)’s Cybersecurity Maturity Model Certification (CMMC) is the newest iteration of the DoD’s effort to protect controlled unclassified information (CUI), the defense industrial base (DIB), and the DoD’s supply chain. Building on the NIST SP 800-171 control set, the CMMC cybersecurity approach is a tiered scoring system ranging from basic cyber hygiene to dynamic and adaptive cybersecurity programs. The CMMC framework comprises 17 domains, with each tier layering in more practices and processes for each domain. This infographic will provide a high-level CMMC overview of the domains, define what CMMC certification entails, and show what to expect when working to meet your CMMC requirements.
Read more about DOD cybersecurity requirements here.
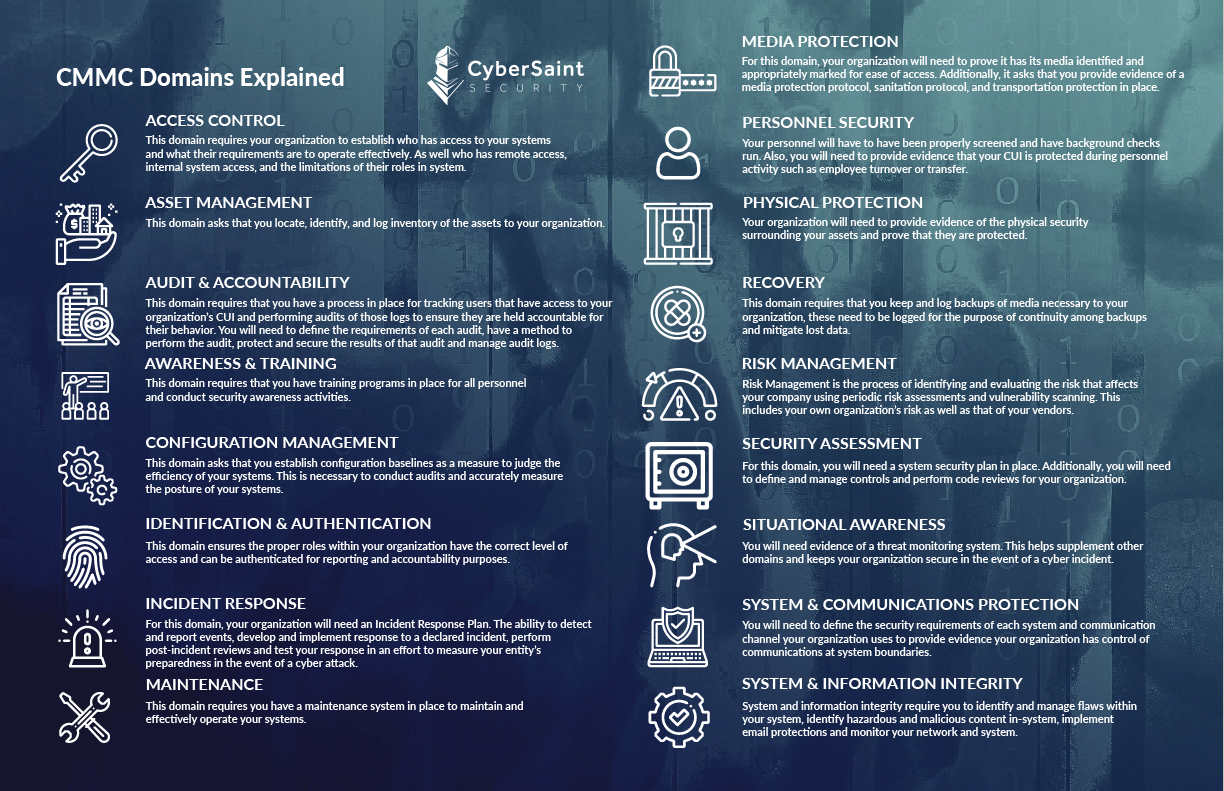
What Are the CMMC Domains?
CMMC Domain Name |
Domain Description |
| Access Control | This domain requires your organization to establish who has access to your systems and their requirements to operate effectively. It also includes who has remote access and internal system access, and the limitations of their roles in the system. |
| Asset Management | This domain asks that you locate, identify, and log the inventory of your organization's assets. |
| Audit & Accountability | This domain requires that you have a process in place for tracking users who have access to your organization’s CUI and performing audits of those logs to ensure they are held accountable for their behavior. You will need to define the requirements of each audit, have a method to perform the audit, protect and secure the results of that audit, and manage audit logs. |
| Awareness & Training | This domain requires you to have training programs for all personnel and conduct security awareness activities. |
| Configuration Management | This domain asks that you establish configuration baselines to judge the efficiency of your systems. This is necessary to conduct audits and accurately measure their posture. |
| Identification & Authentication | This domain ensures that the proper roles within your organization have the correct level of access and can be authenticated for reporting and accountability purposes. |
| Incident Response | For this domain, your organization will need an Incident Response Plan. This plan should include the ability to detect and report events, develop and implement responses to a declared incident, perform post-incident reviews, and test your response to measure your entity’s preparedness during a cyber attack. |
| Maintenance | This domain requires you to have a maintenance system in place to maintain and effectively operate your systems. |
| Media Protection | Your organization must prove its media is identified and appropriately marked for easy access for this domain. Additionally, it asks that you provide evidence of a media protection protocol, sanitation protocol, and transportation protection in place. |
| Personnel Security | Your personnel will have to have been properly screened and background checks run. You must also provide evidence that your CUI is protected during personnel activity, such as employee turnover or transfer. |
| Physical Protection | Your organization must provide evidence of the physical security surrounding your assets and prove that they are protected. |
| Recovery | This domain requires you to keep and log media backups necessary for your organization. These must be logged to ensure continuity among backups and mitigate lost data. |
| Risk Management | Risk Management is the process of identifying and evaluating the risk that affects your company using periodic risk assessments and vulnerability scanning. This includes your own organization’s risk as well as that of your vendors. |
| Security Assessment | For this domain, you will need a system security plan in place. Additionally, you will need to define and manage controls and perform code reviews for your organization. |
| Situational Awareness | You will need evidence of a threat monitoring system. This helps supplement other domains and keeps your organization secure in the event of a cyber incident. |
| System & Communication Protection | You will need to define the security requirements of each system and communication channel your organization uses to provide evidence that your organization controls communications at system boundaries. |
| System & Information Integrity | System and information integrity requires you to identify and manage flaws within your system, identify hazardous and malicious content in-system, implement email protections, and monitor your network and system. |
What are the CMMC Levels?
The Cybersecurity Maturity Model Certification (CMMC) consists of three levels, each with increasing cybersecurity requirements based on the type and sensitivity of the information handled:
-
Level 1 (Foundational): This level is focused on basic cybersecurity hygiene and is designed for companies that handle Federal Contract Information (FCI). It requires the implementation of 17 practices from the Federal Acquisition Regulation (FAR), which are common-sense security measures like access control and incident reporting.
-
Level 2 (Advanced): This level is designed for companies handling CUI and requires compliance with a subset of NIST SP 800-171. Level 2 requires implementing 110 practices that address more sophisticated threats and cover enhanced security protocols such as multi-factor authentication and encryption.
-
Level 3 (Expert): This highest level targets companies involved with critical DoD programs. It requires compliance with a full range of NIST SP 800-171 and additional controls based on NIST SP 800-172. This level focuses on advanced cybersecurity techniques like enhanced threat detection and response to safeguard against highly sophisticated threats, including nation-state attacks.
How to Achieve CMMC Certification
To achieve CMMC, organizations must follow a structured process. First, they should assess the level of certification required based on the type of information they handle, such as FCI or CUI. Next, organizations must conduct a thorough self-assessment or work with a consultant to identify gaps between their current cybersecurity practices and the required CMMC practices and controls. CyberStrong can automate assessments against any given control set, streamlining the assessment step and removing manual inaccuracies.
After addressing these gaps, they must schedule an audit with a CMMC Third-Party Assessment Organization (C3PAO), which will evaluate their compliance with the CMMC framework. Once the audit is complete, if the organization meets the necessary standards, it will be awarded certification at the appropriate level, valid for three years. Regular maintenance and updates of cybersecurity practices are essential to retain certification.
Preparing for CMMC 2.0
What are the changes in CMMC 2.0?
CMMC 2.0 introduces a streamlined and more flexible approach to cybersecurity compliance for the Defense Industrial Base (DIB). Announced in November 2021, the updated model reduces the compliance burden while maintaining strong cybersecurity standards. Key changes include:
-
Three Simplified Levels: CMMC 2.0 replaces the five-tiered structure of the original model with three levels:
-
Level 1 (Foundational): Equivalent to FAR 52.204-21; 17 basic cyber hygiene practices.
-
Level 2 (Advanced): Aligned with NIST SP 800-171; 110 practices with two assessment pathways.
-
Level 3 (Expert): Based on a subset of NIST SP 800-172; for high-priority programs, assessed by the government.
-
-
Self-Assessments for Lower Risk: Organizations at Level 1 and some at Level 2 can now complete annual self-assessments instead of requiring third-party certification.
-
Elimination of CMMC-Specific Practices: CMMC 2.0 removes unique CMMC requirements and realigns practices directly with NIST frameworks.
-
Waivers and POA&Ms (Plans of Action and Milestones): Introduces flexibility by allowing limited use of POA&Ms to achieve compliance over time and waivers in certain mission-critical scenarios.
How does CMMC 2.0 differ from CMMC?
CMMC 2.0 fundamentally shifts the focus from layered certification complexity to a more risk-aligned and NIST-based approach. Key differences include:
| CMMC 1.0 | CMMC 2.0 |
|---|---|
| 5 maturity levels | 3 streamlined levels |
| Required third-party assessments at all levels | Self-assessments are allowed for some levels |
| Included CMMC-specific practices | Fully aligns with NIST SP 800-171/172 |
| No allowance for POA&Ms | POA&Ms permitted under defined conditions |
| More rigid implementation timelines | Phased rollout with public comment periods |
This evolution reflects the DoD’s goal to make cybersecurity standards more achievable and aligned with existing regulations while still protecting CUI.
FAQ: CMMC Domains and CMMC 2.0
What is the current status of CMMC 2.0?
A: As of mid-2025, CMMC 2.0 rulemaking is ongoing under DFARS. While the final rule has not yet been enacted, contractors are encouraged to begin aligning with NIST 800-171 now in anticipation.
Who needs to comply with CMMC 2.0?
A: Any organization in the DoD supply chain that handles Federal Contract Information (FCI) or CUI must meet the applicable CMMC level based on contract requirements.
Will existing NIST 800-171 compliance meet CMMC 2.0 requirements?
A: For Level 2 compliance, yes. If an organization is already fully aligned with NIST 800-171, they are largely prepared for CMMC Level 2.
What is the difference between CUI and FCI?
A: FCI is information provided by or generated for the government that is not intended for public release. CUI is more sensitive and requires safeguarding according to NIST 800-171.
How often must CMMC assessments be conducted?
A: Self-assessments (where applicable) are required annually, while third-party assessments must be conducted every three years.
What domains are included in CMMC Level 2?
A: CMMC Level 2 encompasses 14 domains from NIST SP 800-171, including Access Control, Audit and Accountability, Configuration Management, and more.
Learn more: Mapping NIST CSF to the CMMC Domains





.png)
.png)
.png)
%201.png)
.png)




