Created In Response to the Evolving Threat Landscape
The United States Department of Defense (DoD) supply chain is highly critical to national security and protecting individuals in the armed forces. Regardless of where contractors sit in that supply chain, security is critical to avoid intellectual property theft or, worse, sabotage from bad actors.
With the rise of digital technologies and information systems that many contractors have embraced to increase efficiency and enable business growth has come new cyber threats. The Defense Federal Acquisition Regulation Supplement (DFARS) clause that went into effect in 2018 was the DoD’s first stake in the ground, indicating that members of the defense industrial base (DIB) must be held to a standard of security to protect the nation. The self-certification process proved too unwieldy to track and verify.
Recognizing that there needed to be more structure than the self-certification of compliance with NIST SP 800-171, the DoD began developing what would become the Cybersecurity Maturity Model Certification (CMMC).
What Is CMMC Compliance?
In developing this cyber maturity model, the DoD recognized that not all contractors have the bandwidth to develop security programs on par with a prime, and nor should they have to. Recognizing that contractors’ security should depend on the form and caliber of controlled unclassified information (CUI) that they are working with, the CMMC is a tiered model. Ranging from Tier 1 (Basic Cyber Hygiene) to Tier 5 (Advanced/Progressive), these maturity levels are designed to enable vendors to meet the security requirements necessary for good cyber hygiene with the DoD contracts they are bidding for rather than having to invest in unnecessary requirements meant for a higher bid.
The CMMC has been developed in partnership with academia (Johns Hopkins and Carnegie Mellon) and industry leaders through a listening tour and draws from a library of standards and frameworks, including NIST SP 800-171 and the NIST Cybersecurity Framework.
The CMMC framework introduces new terminology to classify what most information security practitioners will recognize as categories, control families, and security controls. In a CMMC assessment, one will recognize what are called “Domains” as categories and subcategories from NIST SP 800-53 for protecting CUI:
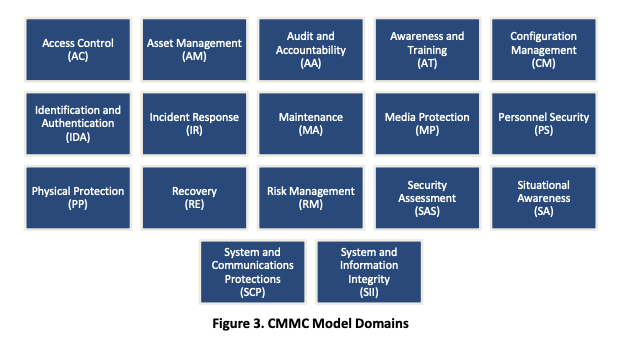
From there, each Domain has a collection of “Capabilities” resembling control families in other frameworks like SP 800-171 and the CSF. Finally, the capabilities have specific “Practices and Processes” associated with them, and security leaders can see these as more granular controls.
Tips to Proactively Meet The CMMC
For most vendors, the CMMC levels are the biggest concern. Given that they are the heart of the certification, the tiers are critical to proactively meeting the CMMC requirements. The Tier-level certification requirements for a given contract will be included in the RFI and subsequent RFP.
CMMC Model Certification 0.6 Practices per Reference |
||||
| CMMC Level | Total | 48 CFR 52.204-21 | NIST SP 800-171r1 | Draft NIST SP 800-171B |
| Level 1 | 17 | 15 | 17 | - |
| Level 2 | 58 | - | 51 | - |
| Level 3 | 56 | - | 42 | - |
| Level 4 | 62 | - | - | 17 |
| Level 5 | 26 | - | - | 9 |
| N/A Excluded | - | - | - | 7 |
| Total | 219 | 15 | 110 | 33 |
From our field intel, we have gleaned that most contract requirements in the supply chain will fall in Tier 3 and below. Primes will be responsible for achieving Tier 4 and 5 certification levels and cybersecurity practices.
We recommend proactive defense contractors start working towards Tier 3 compliance. Based on the timeline given Office of the Under Secretary of Defense for Acquisition & Sustainment, we anticipate that Tier 3 and below are at least in their semi-final (if not final) stages, and contractors can start working towards the requirements.
We have good news if you are pursuing Tier 3 compliance - if you have used CyberStrong to achieve DFARS compliance, we have identified only 19 Processes/Practices (controls) referenced from frameworks outside of NIST SP 800-171. We also support Tier 3 Processes and Practices in CyberStrong and CMMC audits.
Discover why leading DoD contractors and prime contractors are choosing CyberStrong:





.png)
.png)
.png)
%201.png)
.png)




