Cyber risk leaders leverage CyberStrong's purpose-built functionality to standardize, centralize, and automate cyber risk management.
CyberStrong's Cyber Risk Management Platform empowers you to see cyber risk in real-time, not point-in-time. Take a dynamic and defensible approach to risk quantification, while leveraging automation that shows real-time updates to risk posture based on controls. Stay informed as your risk profile changes, and always be one step ahead.
KEY BENEFITS
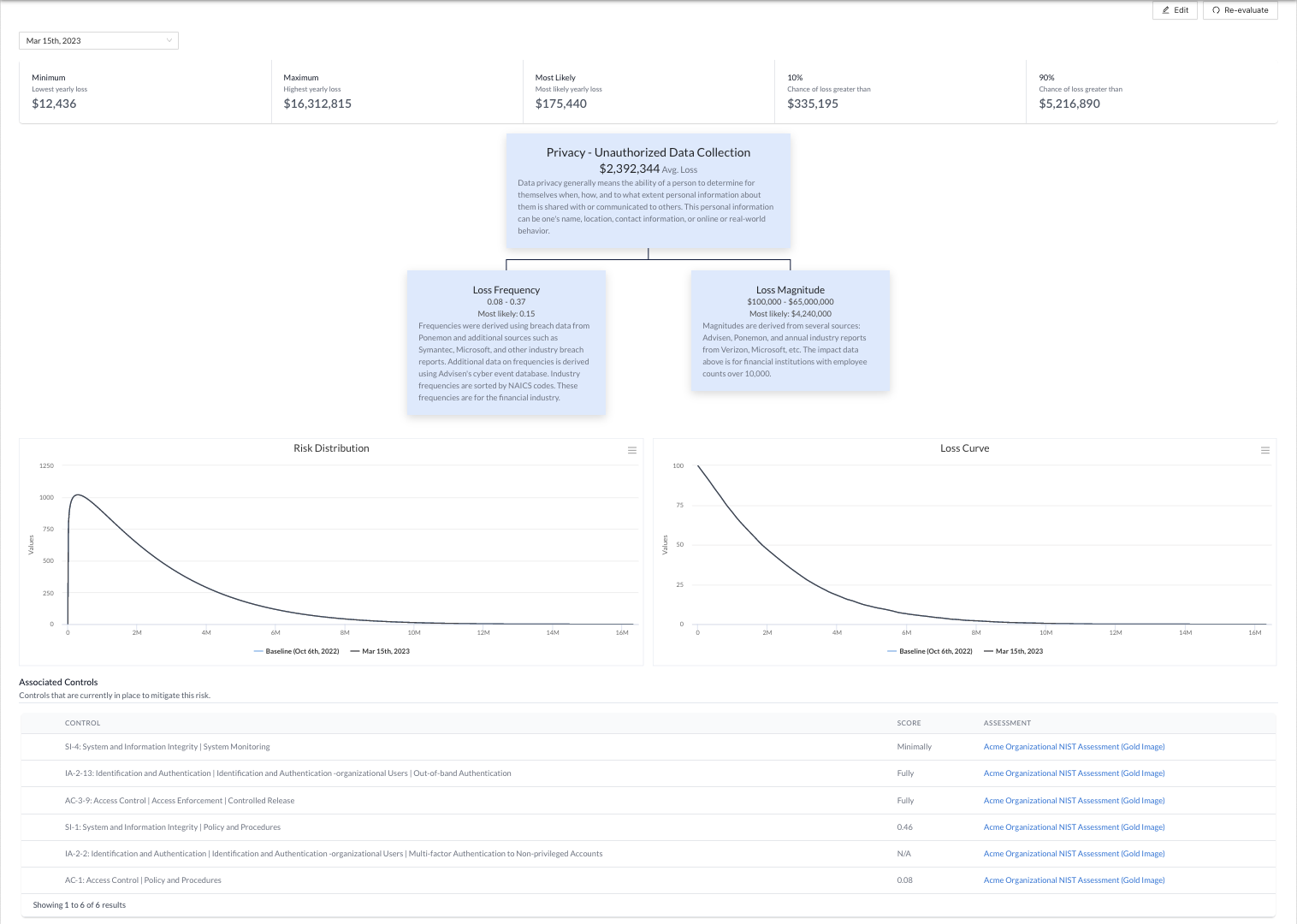
Quantify cyber risk in context with transparent, explainable risk models such as NIST SP 800-30, FAIR and CyberInsight, as well as custom risk models.
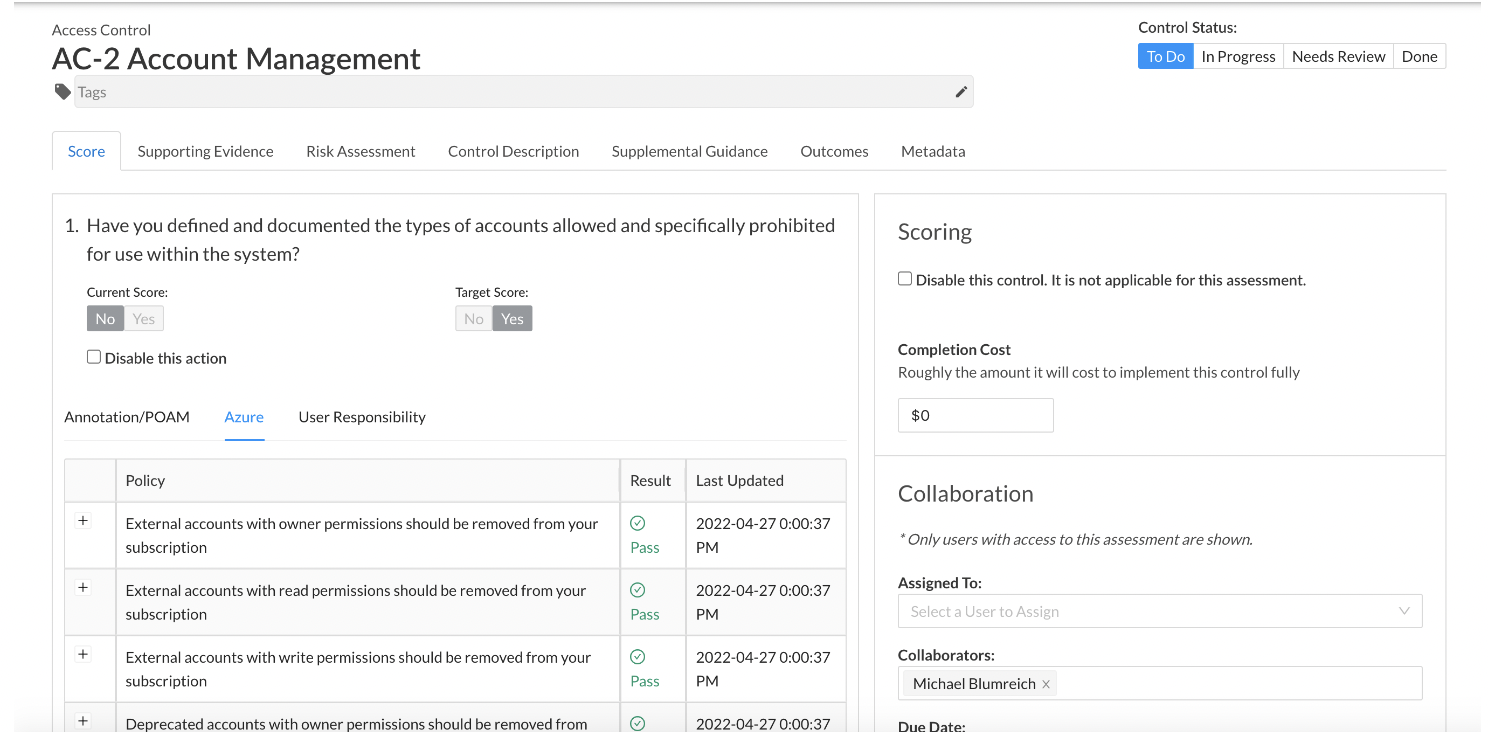
Using CCA integrations, control scores are automatically updated in real-time and roll up to risk dashboards and reports.
An Executive Dashboard built with Fortune 50, leading consulting organizations, and practitioner design partners to present cyber risk in the most actionable way possible.
Quantify cyber risk in context with transparent, explainable risk models such as NIST SP 800-30, FAIR and CyberInsight, as well as custom risk models.
Using CCA integrations, control scores are automatically updated in real-time and roll up to risk dashboards and reports.
Leave point-in-time behind and make use of real-time insights into control scores and their impacts to your organization's risk profile.
An Executive Dashboard built with Fortune 50, leading consulting organizations, and practitioner design partners to present cyber risk in the most actionable way possible.
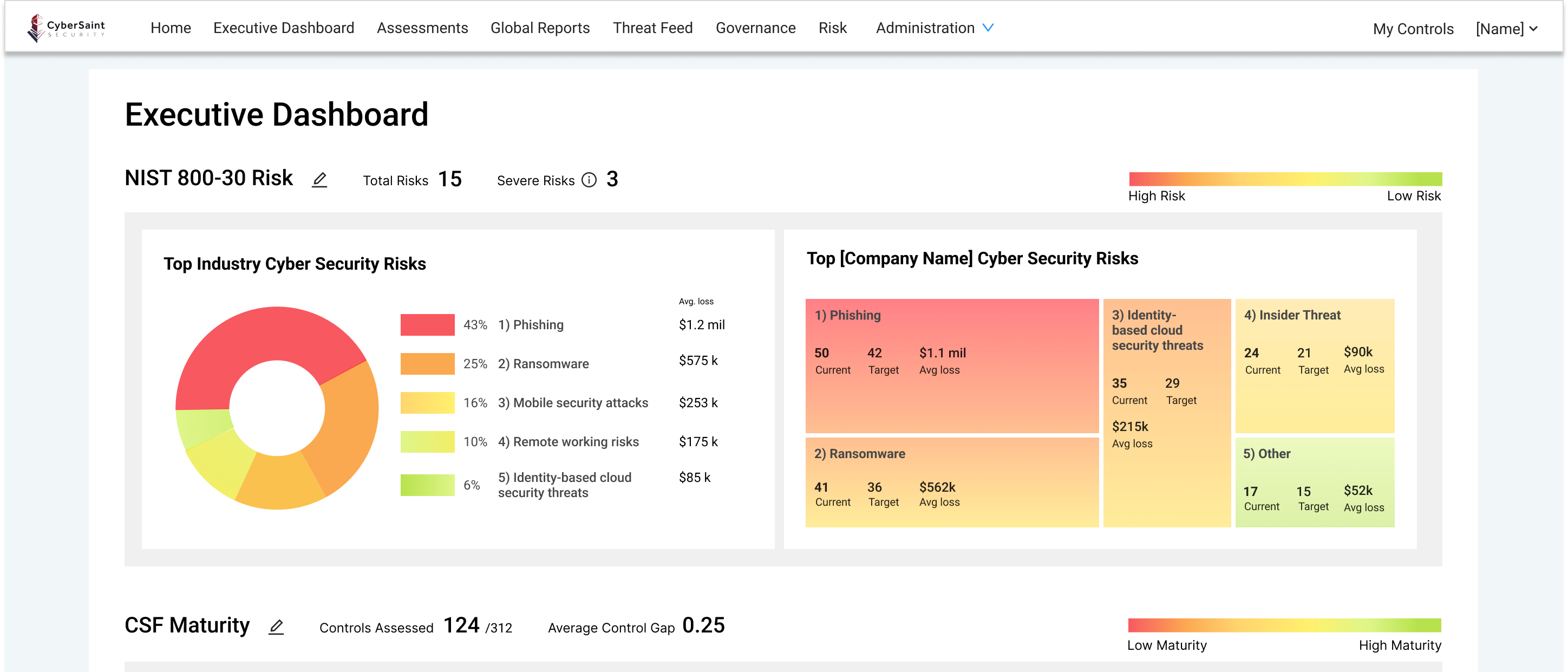
Purpose-built for C-suite and Board level conversations about cyber risk, CyberStrong's Executive Dashboard delivers a clear and defensible illustration of your cyber risk management program.
It's organizations like yours that inspire where our product roadmap is headed. CyberSaint customers have a direct influence on our roadmap and we work to address all your feature requests in record time.
Boards and the C-Suite are now more interested in knowing the ins and outs of your cyber posture. CyberStrong gives CISOs and teams the tools to easily roll up cyber risk to business risk.
AI and ML have been used in other areas of cyber and tech, why not risk and compliance? Organizations have been pouring over spreadsheets for too long, and we've proven there is a credible way to automate.
CCA takes the data gathered via integrations and allows you to associate that data with controls, leading to automated control scoring, real-time reports and dashboards, and a dynamic risk register.
Download the Automation One Pager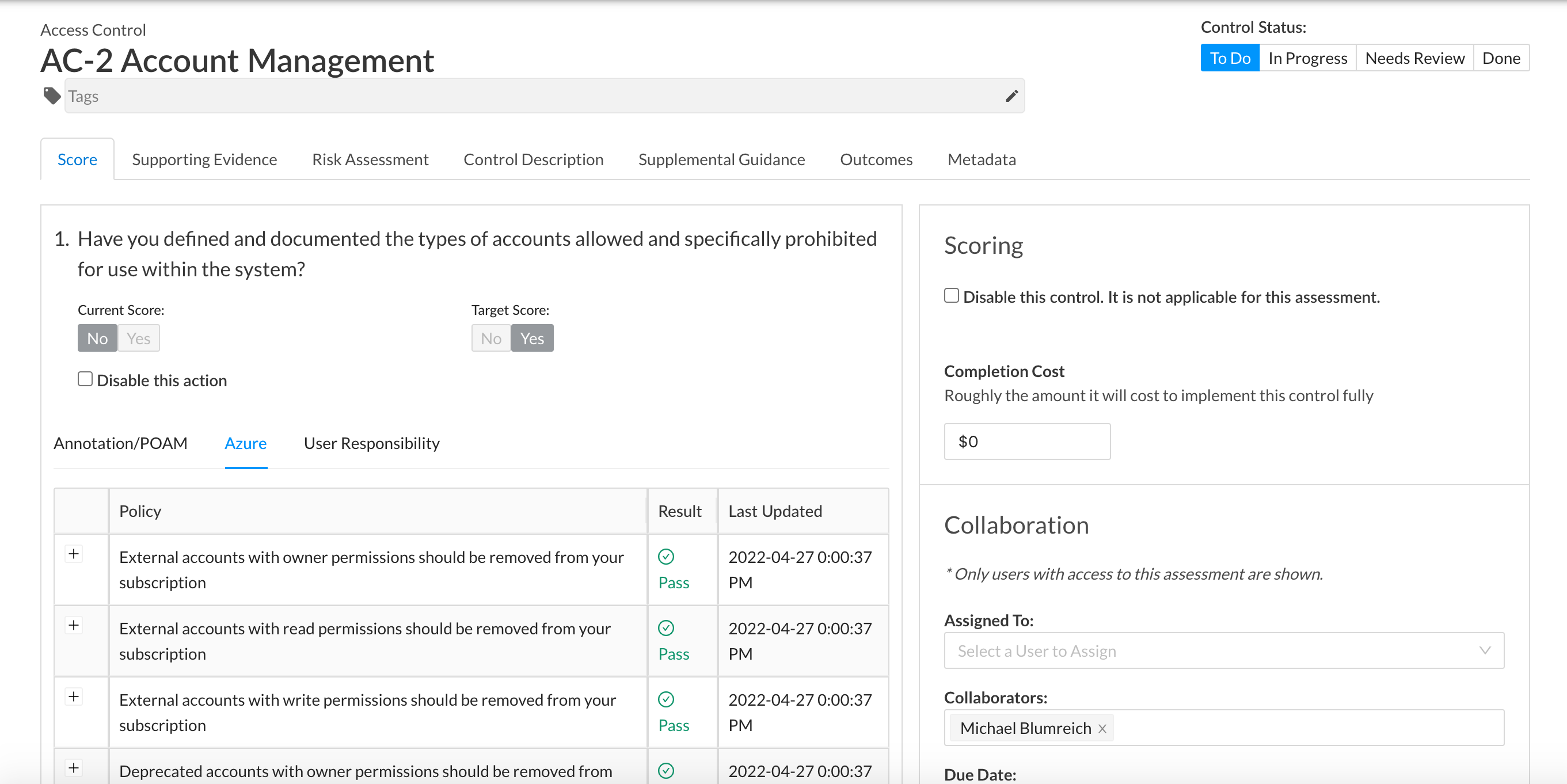
Leverage data coming from your systems to automate controls, tailoring business logic around what controls are updated when specific vulnerabilities or other data points are identified.
Request a Demo
.png)

- Bruce Forman, CISO, UMass Memorial Health Care
- Javed Ikbal, CISO, VP of Information Security, Risk Management & Compliance, Bright Horizons Family Solutions
- Mark Evans, Director of Cybersecurity, Salt Lake County, Utah
- Shawn Lane, Security and Compliance Engineer, Vertek Corporation
- Consulting Risk Leader and Senior Manager, Big Four Consulting Practice
Copyright © 2026 CyberSaint Security. All Rights Reserved. Privacy Policy.