The General Data Protection Regulation may certainly seem complex to implement for those who haven’t focused on data protection and privacy measures in the past.
For organizations who are thinking of adopting the NIST Cybersecurity Framework (CSF)or who have already, it makes sense to use existing best practices provided by National Institute of Standards and Technology (NIST) than to wait until more EU guidance on how to actually attack this project comes out.

You’re probably aware of the ramifications and fines associated with a breach and non-compliance, or the “right to be forgotten”. We have extensive experience working with executives on security and risk projects (CyberSaint's CEO and Founder, George Wrenn, worked on the NIST Cybersecurity Framework himself). We have the knowledge of NIST CSF as well as data privacy to give you an understanding on how to “hack” GDPR with the NIST CSF.
The backbone of your privacy and data protection initiatives should be build on understanding and having real visibility into the data you have across your company’s processes and lifecycles. You must scope your information flows that both leave and enter your organization - and this isn’t just technical! It’s physical manifestations of data too, like spreadsheets and forms.
Using NIST Controls to Fulfill GDPR Requirements
The real point of GDPR? Accountability, data privacy and data protection. Using the NIST Cybersecurity Framework can add immense value on your journey to GDPR compliance. Various NIST security controls can help your company secure the confidential data that you need to through the five NIST Functions: Identify, Protect, Detect, Respond and Recover.
NIST 800-53 Publication, “Assessing Security and Privacy Controls in Federal Information Systems and Organizations” can help you introduced the continuous evaluation of your security procedures in your organization related to the GDPR.
Interestingly enough, NIST just published a new draft of its Risk Management Framework (RMF) to include measures on data privacy. The NIST 800-37, “Guide for Applying the Risk Management Framework to Federal Information Systems,” or Risk Management Framework (RMF) can help you achieve GDPR requirements by following it.
Not only does the CyberStrong Platform have the NIST 800-30 Risk Management Framework built in to assess your risk and data type, but it also has NIST's Appendix J built in to make GDPR compliance a no-brainer, while also aligning with NIST's gold-standard cyber practices.
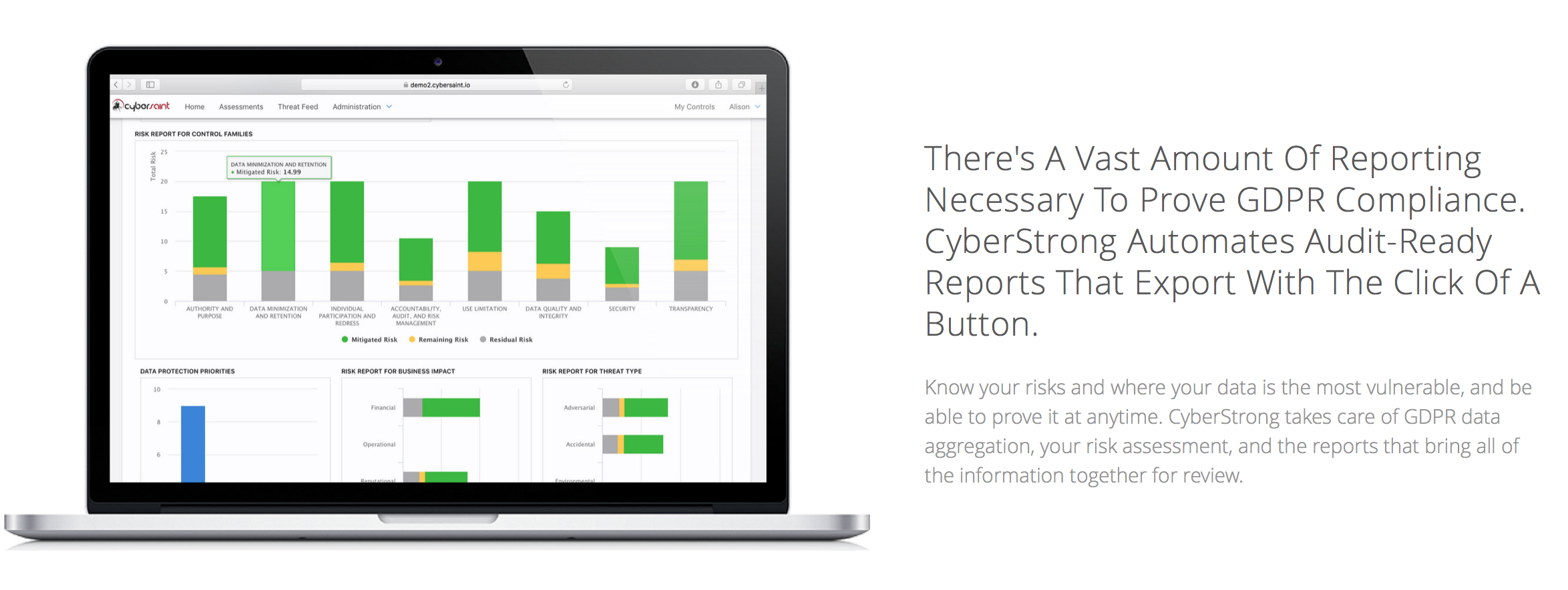
If you want an entry level introduction into handling sensitive data, or even ever consider selling to the government, consider adopting NIST 800-171 - originally required by the Department of Defense for all of its large contractors and suppliers, now being made into a FAR (Federal Acquisition Regulation) for anyone who sells to the government. The NIST 800-171 Special Publication, “Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations” is certainly where you could begin.
You must assess risks in a continuous manner to address the GDPR, and this can be a big undertaking if you haven’t already set up a continuous compliance program.
If you don’t have a platform like CyberStrong that makes continuous compliance and reporting easy (Not just for GDPR.. for NIST Risk Assessments, NIST Cybersecurity Framework, New York Financial Regs, PCI Compliance, ISO2002 and any other framework you can think of..) you should probably consider it in order to save time, people hours and get off spreadsheets.
You must have an adequate, at the very least, risk assessment in place and procedures by which you deploy risk management initiatives (NIST RMF is a great option). CyberStrong helps you automate your risk assessment continuously as well, so that you can streamline your continuous compliance program for General Data Protection Regulation and any other standard you may need to address both now and in the future.











