NIST CSF Function: Detect
The Detect function requires the development and implementation of the appropriate activities to recognize the occurrence of a cybersecurity event.
"The Detect function enables the timely discovery of cybersecurity events. Examples of outcome Categories within this Function include Anomalies and Events, Security Continuous Monitoring, and Detection Processes."
The Framework Core's detection function is a critical step to a robust cyber program. The faster a cyber event is detected, the faster the repercussions can be mitigated.
Examples of how to accomplish steps towards a specific detection function:
- Anomalies & Events: Prepare your team to have the knowledge to collect and analyze data from multiple points to detect a cybersecurity event.
- Security & Continuous Monitoring: Have your team monitor your assets 24/7, or consider using an MSS to supplement their efforts.
- Detection Processes: Attempt to know about a breach as soon as possible and follow disclosure requirements as needed. Your program should be able to detect inappropriate access to your data as quickly as possible.
Detecting a breach or event can be life or death for your business, making the Detect function of the Cybersecurity Framework critical to both security and business success. Following these standards and best practices and implementing these solutions will help you scale your program and mitigate cybersecurity risks.
Explore the NIST CSF Function Detect in-depth with these guidelines.
NIST CSF Function: Respond
NIST defines the Respond function as "Develop and implement appropriate activities to take action regarding a detected cybersecurity incident.”
"The Respond Function supports the ability to contain the impact of a potential cybersecurity incident. Examples of outcome Categories within this Function include Response Planning, Communications, Analysis, Mitigation, and Improvements.
The Respond function utilizes response planning, analysis, and mitigation activities to ensure that the cybersecurity program continually improves.
Starting with an incident response plan is a vital first step in adopting the Respond function, ensuring compliance with necessary reporting requirements and encrypting and transmitting data securely for a given location and industry. An excellent next step is to develop a mitigation plan - what steps will your team take to remediate the identified risks to your program and organization?
NIST CSF Function: Recover
The Framework Core then identifies underlying key categories and subcategories for each function. It matches them with examples of Informative References, such as existing standards, guidelines, and practices for each subcategory (NIST).
According to the NIST framework, Recover is defined as the need to "develop and implement the appropriate activities to maintain plans for resilience and restore any impaired capabilities or services due to a cybersecurity event.
The Recovery Function supports timely recovery to normal operations, reducing the impact of a cybersecurity event. Outcomes for this Framework's Core function include Recovery Planning, Improvements, and Communications.
NIST CSF Recover includes these areas:
- Recovery Planning: Recovery procedures are tested, executed, and maintained so that your program can mitigate the effects of an event sooner rather than later
- Improvement: Recovery planning and processes are improved when events happen, areas for improvement are identified, and solutions are put together
- Communication: Coordinate internally and externally for greater organization, thorough planning, and execution
The Recover function is essential not only to the business and security teams but also to customers and the market. Swift recovery with grace and tact puts businesses in a better position both internally and externally than otherwise. Aligning a recovery plan will help ensure that, if a breach occurs, the company can stay on track to achieve the necessary goals and objectives and distill important lessons learned.
What is the NIST CSF 2.0?
NIST CSF 2.0 introduces several significant changes. The most notable update is the addition of a sixth core function, called "Govern," which emphasizes the importance of cybersecurity governance and strategic planning. The framework's scope has been expanded to cater to organizations of all sizes and sectors, with improved usability and implementation guidance.
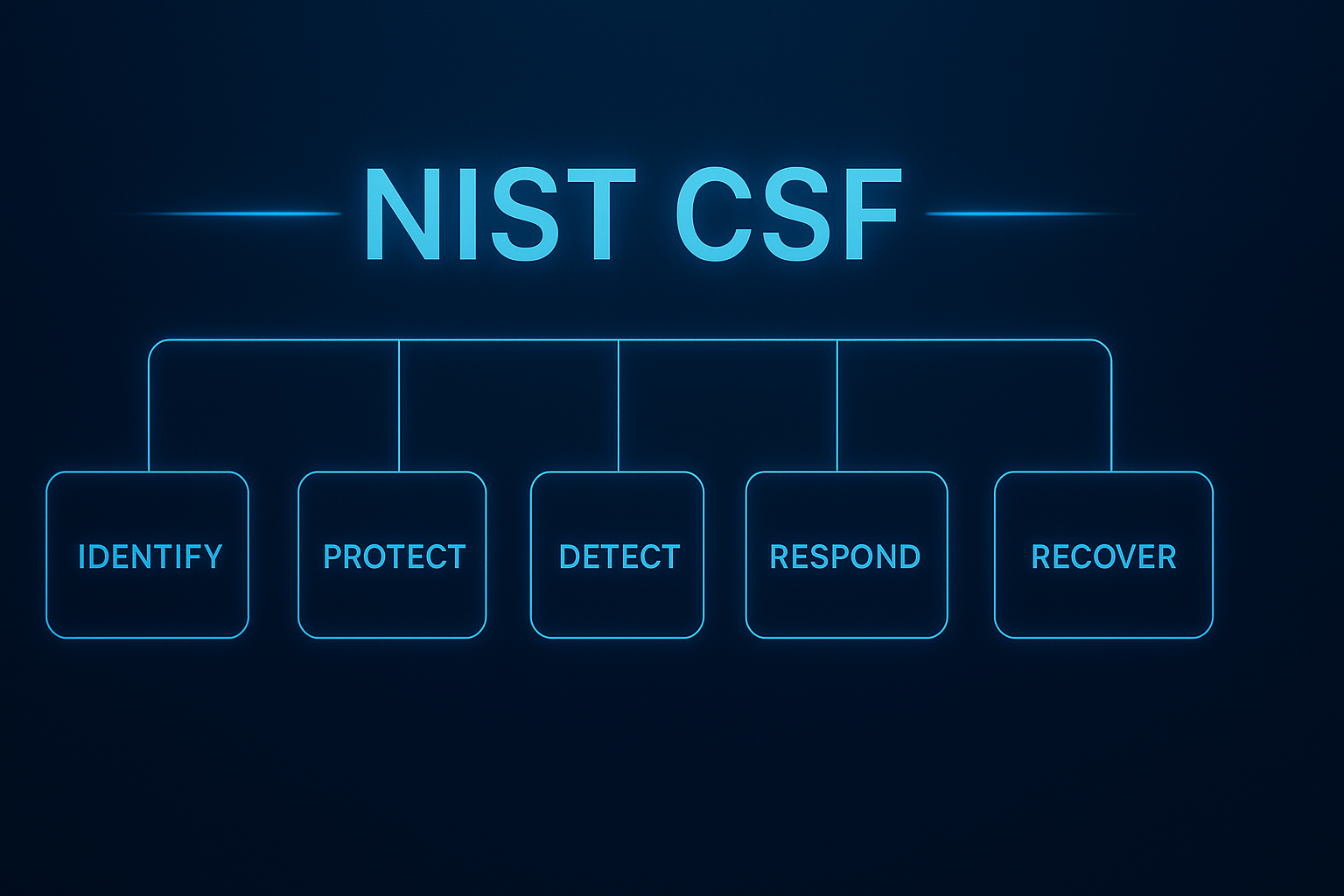
NIST CSF 2.0 also restructures the original five functions (Identify, Protect, Detect, Respond, and Recover) to enhance clarity and relevance. It places a greater focus on emerging threats, supply chain risk management, and the integration of privacy considerations. The updated framework includes clear metrics for measuring compliance and provides additional resources, such as the NIST CSF 2.0 Reference Tool, to improve overall usability and adaptation to modern cybersecurity risks.
|
NIST CSF Function |
Function Overview |
|
Identify |
Establishes a clear understanding of assets, systems, data, and risks to prioritize cybersecurity efforts and resources. |
|
Protect |
Focuses on implementing safeguards and controls to prevent or limit the impact of potential cybersecurity events. |
|
Detect |
Enables timely discovery of cybersecurity incidents through monitoring, analysis, and detection processes. |
|
Respond |
Guides how to contain, mitigate, and communicate during cybersecurity incidents to minimize damage. |
|
Recover |
Emphasizes resilience—restoring services and operations quickly and improving from past incidents. |
|
Govern (Added in NIST CSF 2.0) |
Embeds cybersecurity into enterprise governance by defining policies, roles, accountability, and risk management strategy. |
How to Use the NIST Framework Core to Guide Implementation
Cybersecurity based on the NIST Cybersecurity Framework can be a challenge. Regardless of how challenging it may be, it will be worthwhile. Given that the Framework is based on outcomes rather than specific controls, it enables organizations to build on a strong foundation and supplement it to achieve compliance with new regulations as they emerge.
The core functions are to identify, protect, detect, respond to, and recover from cybersecurity events, aiding organizations in their efforts to spot, manage, and counter them promptly.
NIST CSF Compliance
Achieving and maintaining NIST CSF compliance is more than checking boxes, it’s about operationalizing a living, risk-based framework that continuously strengthens your cybersecurity posture. As the gold standard for mature cybersecurity programs and the foundation for many emerging regulations, the NIST CSF provides the structure organizations need to identify, protect, detect, respond to, and recover from risks and threats while aligning security investments with business outcomes.
CyberStrong is purpose-built on the pillars of the NIST CSF, automating every stage of framework adoption and compliance. The platform seamlessly maps your existing controls to NIST CSF Categories and Subcategories, continuously monitors control effectiveness, and quantifies residual risk across all five core functions—and now, with NIST CSF 2.0, includes the new Govern function. Through automated crosswalking, continuous control monitoring, and board-ready reporting, CyberStrong empowers teams to transform the NIST CSF from a static framework into an actionable, measurable, and continuously improving cyber risk program.
Organizations leveraging CyberStrong not only align with the NIST CSF—they build resilience, drive executive confidence, and gain unified visibility into their true cybersecurity maturity.
Schedule a demo to see how CyberStrong simplifies NIST CSF compliance and enables continuous improvement across your cyber risk management lifecycle.
NIS2 is a growing requirement for organizations of all sizes and maturity. Get the latest insights on the NIS2 Directive Resources.





.png)
.png)
.png)
%201.png)
.png)