The National Institute of Standards and Technology developed the Framework for Improving Critical Infrastructure Cybersecurity, known as the NIST Cybersecurity Framework (CSF), in response to a presidential executive order to support the critical functions of our society in monitoring and remediating cybersecurity risks. Industrial control systems, such as those involved in product production and distribution automation, have been encouraged to adopt a security framework to protect against cyberattacks, reduce cyber vulnerabilities, and enhance cybersecurity maturity. The use of the Framework has since expanded, being adopted by businesses of all sizes across various industries.
As voluntary guidance, the NIST CSF is intended to be customized to fit the organization and, as a result, does not include controls built into it as other standards do. Instead, the CSF helps security practitioners open a dialogue with stakeholders about the need for cybersecurity preparedness and investment in securing the business. Using the five functions of the Framework Core—Identify, Detect, Respond, and Recover—technical and non-technical stakeholders understand their strengths and weaknesses in their organization’s risk management and cybersecurity, and where to invest time and effort. Implementing the Cybersecurity Framework begins with a benchmarking assessment, which, for most organizations, merits the use of an automated risk assessment tool.
Now that you’ve decided to work with the CSF, selecting the right cybersecurity assessment tool to implement it is critical.
Capabilities of a NIST Cybersecurity Framework Assessment Tool
Any CSF assessment tool must be built on the Framework itself, using the three main elements as guidance:
- NIST CSF Framework Profiles: Understand how the solution enables your team to implement Framework Profiles.
- NIST CSF Implementation Tiers: How it helps you articulate your Implementation Tier.
- NIST CSF Categories: The solution clearly illustrates your strengths and weaknesses in the context of the Five Functions.
How to Build a NIST CSF Profile
A Cybersecurity Framework Assessment tool should employ the NIST CSF Categories and Subcategories, allowing you and your organization to prioritize the most important based on cyber risk assessments and business drivers. From the Categories and Subcategories assessed, you will need to be able to build out a Current State and Target State profile.
In the case of CyberStrong, the platform will automatically generate a current and target state profile as your team completes an assessment. These visualizations are valuable for your team to understand where they need to invest their time. It is also beneficial to talk to your executive leadership to contextualize where financial investment needs to be made.
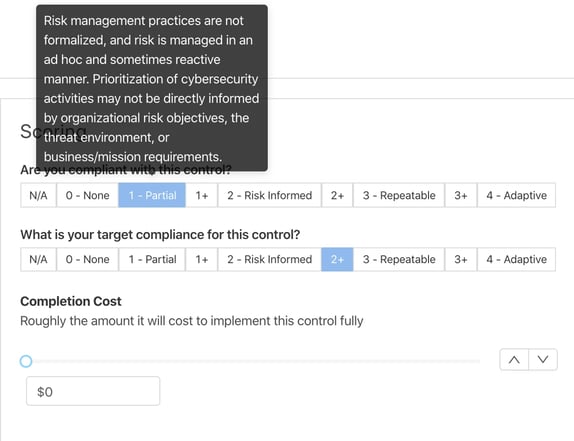
Using the CSF Implementation Tiers for Assessments
NIST stresses in the Framework documentation that the Implementation Tiers are not a maturity model. Instead, the tiers serve as a means to approach cyber risk management and bridge the gap between technical and business stakeholders. For assessment tools, the Implementation Tiers can take multiple forms.
CyberStrong utilizes implementation tiers in control scoring and rolls that data up to the reporting level, where it is presented to directors, the CEO, and the Board. This transparency enables contributors and stakeholders to view the Tiers at all levels of granularity, from control to assessment of the asset and the entire organization.
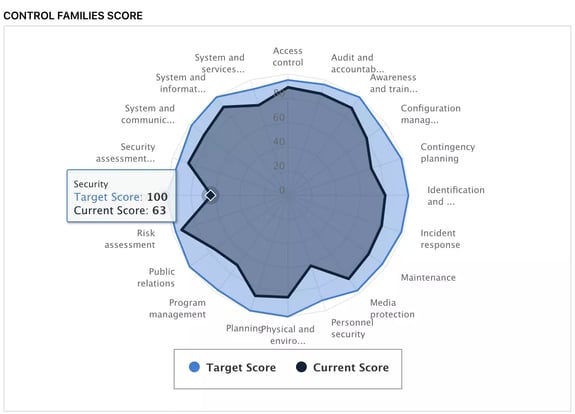
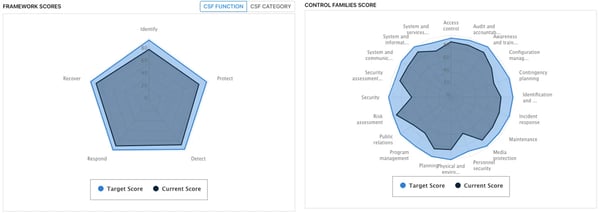
The Five Functions of the NIST CSF
The Five Functions of the NIST CSF are the most well-known elements of the CSF. Another lens through which to assess cybersecurity and risk management is the Five Functions - Identify, Protect, Detect, Respond, and Recover - which enable stakeholders to contextualize their organization’s strengths and weaknesses within these five high-level buckets.
The CyberStrong platform automatically generates gap-analysis graphs using the Five Functions and can be seen in every assessment, regardless of the framework (even assessments not using the NIST CSF). Having the Five Functions at arm's reach, no matter the assessment, serves as a common thread to tie all assessments and assets together.
What to Consider in a NIST Cybersecurity Framework Assessment Tool
When evaluating a NIST Cybersecurity Framework assessment tool, prioritize solutions that go beyond checkbox exercises and instead strengthen the foundation of your entire cyber risk program. The right tool should align directly with the pillars of the NIST CSF—Identify, Protect, Detect, Respond, and Recover—while enabling continuous assessment, clear communication, and measurable progress across these functions.
CyberStrong is purpose-built on these NIST CSF principles, automating how organizations assess, measure, and mature their cybersecurity posture. The platform dynamically generates CSF profiles, implementation tier insights, and gap analyses in real time, providing unified visibility across technical controls and business risk. With AI-powered cross-framework mapping, Continuous Control Monitoring, and board-ready reporting, CyberStrong transforms the NIST CSF from static documentation into an actionable, data-driven strategy.
Whether you’re benchmarking your current state, prioritizing investments, or communicating progress to leadership, CyberStrong simplifies every step of the NIST CSF journey, making it the recommended assessment tool for organizations building a connected, continuous, and quantified cyber risk management program.
Schedule a demo to see how CyberStrong operationalizes the NIST CSF and accelerates your path to measurable cyber resilience.





.png)
.png)
.png)
%201.png)
.png)





