Protecting controlled unclassified information (CUI) has had the spotlight for a while now, primarily as an extensive focus of the Department of Defense (DoD) for the past several years. In November 2010, the White House issued Executive Order (EO) 13556. This order established an open and uniform program across Civilian and Defense agencies for managing information that requires safeguarding or dissemination controls according to and consistent with law, regulation, and Government-wide policies.
The problem that the Executive Order was trying to solve was that departments and agencies employed ad hoc, agency-specific policies, procedures, and markings to safeguard and control CUI against any information and cyber incidents.
This inefficient and confusing patchwork led to inconsistent, unclear, or unnecessarily restrictive dissemination policies and created impediments to authorized information sharing. Inefficiency in itself is a shame. In this case, more so, since CUI is sensitive information that often impacts privacy and security concerns, contains proprietary business interests, and is critical in law enforcement investigations.
The National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171 requirement was developed to ensure that those working in conjunction with the Department of Defense, like the Defense Industrial Base (DIB), would have methods to meet the requirements for safeguarding covered defense information.
The regulatory document published on behalf of the government by NIST and the Under Secretary for Defense Acquisition states that “protection of Controlled Unclassified Information (CUI) while residing in nonfederal information systems and organizations is of paramount importance to federal agencies and can directly impact the ability of the federal government to carry out its designated missions and business operations successfully.”
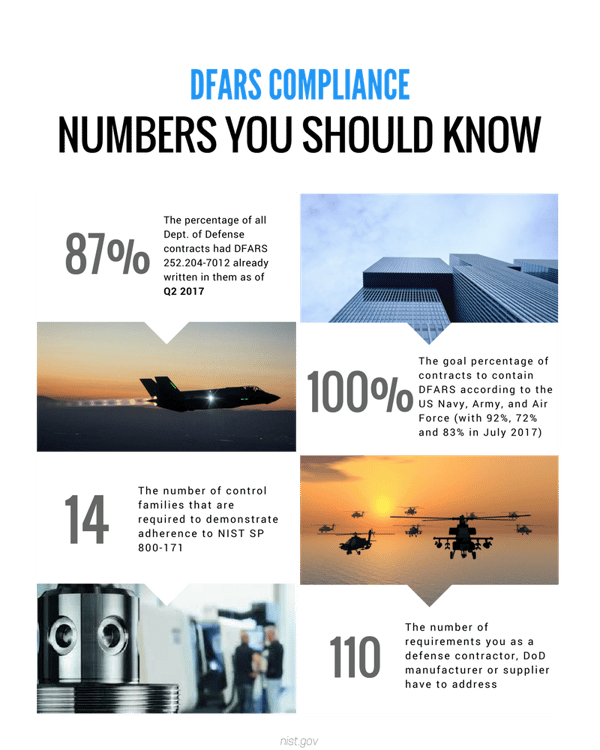
It was published as a Defense Federal Acquisition Regulation Supplement (DFARS), or the cyber clause DFARS 252.204-7012.
In Translation... the Department of Defense made DFARS Compliance required by any company that generates DoD-related revenue to protect its sensitive data within the covered contractor information system from being compromised.
Key Takeaway: If your company generates any DoD-related revenue regardless of size or wants to generate revenue selling to DoD-related businesses in the future, you MUST be compliant with DFARS to win or maintain those contracts.Complying with NIST 800-171 ultimately gives your organization the upper hand over the competition the quicker you get it done. If a supplier is non-compliant with the NIST cybersecurity controls outlined in the cyber DFARS clause 252.204-7012, then the supplier must notify the DoD CIO office within 30 days of contract award of the areas of non-compliance. Filling out and submitting the questionnaire you may have received doesn't count as compliance and will not allow you to prove compliance either.
More background on the DFARS cyber requirements:
NIST SP 800-171: Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations