The US National Institute of Standards and Technology released the 2.0 version of its Cybersecurity Framework, focusing more on governance and supply chain issues and offering resources to speed the framework’s implementation.
After two years of work, the US National Institute of Standards and Technology (NIST) has issued the 2.0 version of its widely referenced Cybersecurity Framework (CSF), expanding upon the draft 2.0 version it issued in September. The CSF 2.0, cited in President Biden’s National Cybersecurity Strategy and several emerging government cybersecurity policy statements, has shifted its focus from protecting critical infrastructure, such as hospitals and power plants, to all organizations in any sector. The previous title of the framework, “Framework for Improving Critical Infrastructure Cybersecurity,” has been abandoned in favor of the “NIST Cybersecurity Framework (CSF) 2.0” in recognition of this shift.
More than with either of the two previous versions of the CSF, the original version released in 2015 and the 1.1 version released in 2018, the 2.0 version is less of a static resource and more of a basket of resources guiding the implementation of the framework. “The CSF has been a vital tool for many organizations, helping them anticipate and deal with cybersecurity threats,” said Under Secretary of Commerce for Standards and Technology and NIST Director Laurie E. Locascio. “CSF 2.0, which builds on previous versions, is not just about one document. It is about a suite of resources that can be customized and used individually or in combination over time as an organization’s cybersecurity needs change and its capabilities evolve.”
The New Govern function is the Most Significant Change
The most significant structural change to the CSF is the addition of a sixth function, Govern, around which the previous five functions of Identify, Protect, Detect, Respond, and Recover revolve. The Govern function aims to help organizations incorporate cybersecurity risk management into broader enterprise risk management programs by presenting “outcomes,” or desired states, to inform what an organization may do to achieve and prioritize the outcomes of the other five functions.
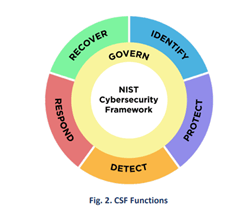 The goal of creating a new Govern category is to elevate all the cybersecurity risk management activities to the C-suite and board levels of organizations. “I think the big focus in 2.0 is promoting governance to a function,” said Padraic O’Reilly, founder and chief innovation officer of CyberSaint, tells CSO. “I think there’s an understanding now, and it’s pretty common across cybersecurity, that if governance is not actively involved, you’re just spinning your wheels.”
The goal of creating a new Govern category is to elevate all the cybersecurity risk management activities to the C-suite and board levels of organizations. “I think the big focus in 2.0 is promoting governance to a function,” said Padraic O’Reilly, founder and chief innovation officer of CyberSaint, tells CSO. “I think there’s an understanding now, and it’s pretty common across cybersecurity, that if governance is not actively involved, you’re just spinning your wheels.”
The Supply Chain Plays a More Prominent Role
CSF 2.0 also incorporates and expands upon the supply chain risk management outcomes contained in CSF 1.1 and groups most of these under the Govern function. According to the 2.0 framework, given “the complex and interconnected relationships in this ecosystem, supply chain risk management (SCRM) is critical for organizations. Cybersecurity SCRM (C-SCRM) is a systematic process for managing exposure to cybersecurity risk throughout supply chains and developing appropriate response strategies, policies, processes, and procedures. The subcategories within the CSF C-SCRM Category [GV.SC] provide a connection between outcomes that focus purely on cybersecurity and those that focus on C-SCRM.”
Including supply chain risk management under the Govern function is only one step in the right direction toward addressing one of the thornier issues in cybersecurity. “Supply chain is a mess,” O’Reilly says. “It’s a mess, and it’s a mess because it’s complex. I think they’re pulling some of the supply chain under governance because more needs to be done to manage it from the top. Because right now, you have some practices that are halfway decent but are only capturing about maybe half of the issue.”
Updated References, Quick Start Guides, and Improved Integration with Other Resources
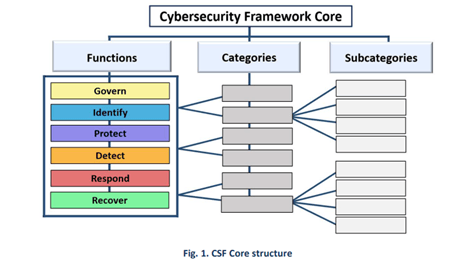
The new version also features updated informative references, or existing standards, guidelines, and frameworks, that help flesh out the technical details and steps that CSF contains to provide further insight into how organizations can implement the 106 subcategories clustered under 23 categories, which are in turn organized under the major functions.
To improve on potential adoption difficulties posed by the CSF, NIST incorporated into the 2.0 version a series of quick-start guides on several topics, including how to create CSF profiles and tiers and, notably, how to begin managing supply chain security risks and create community profiles to allow communities that share a common interest to describe consensus points of view.
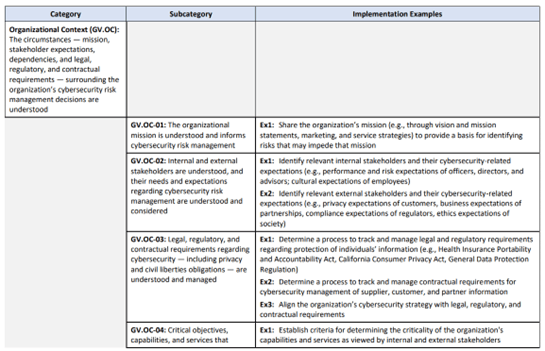
To provide even more practical guidance on how to implement the framework, CSF 2.0 also offers implementation examples. These implementation examples (below) represent NIST’s effort to phrase the passively written outcomes into more active actionable steps organizations can take to adopt the framework.
Since the framework’s inception, NIST has taken care not to prescribe any particular steps organizations should take, given that every organization has unique technical and resource configurations. Instead, NIST has referred to outcomes, which some argue offer little practical guidance on what specific actions organizations should take.
Included in CSF 2.0 is improved integration with other widely used NIST resources that deal with enterprise risk management, ERM, and ICT risk management programs. Among these resources are:
- SP 800-221, Enterprise Impact of Information and Communications Technology Risk: Governing and Managing ICT Risk Programs Within an Enterprise Risk Portfolio
- SP 800-221A, Information and Communications Technology (ICT) Risk Outcomes: Integrating ICT Risk Management Programs with the Enterprise Risk Portfolio
- SP 800-37, Risk Management Framework for Information Systems and Organizations
- SP 800-30, and Guide for Conducting Risk Assessments from the NIST Risk Management Framework (RMF)
NIST said it will continue to build and host additional resources to help organizations implement the CSF. All resources are made publicly available on the NIST CSF website. NIST says suggestions for additional resources to reference on the NIST CSF website can be shared with NIST at cyberframework@nist.gov.










