What is a Cybersecurity Assessment?
Cybersecurity risk assessments are increasingly replacing checkbox compliance as the foundation for an effective cybersecurity program. As more executive teams and Boards take greater interest and concern around the enterprise’s security posture, effectively managing internal and external risks and reporting out has become a core tenet of a CISO’s job description.
The average cost of cybercrime is expected to reach $23.84 trillion by 2027, highlighting the importance of cybersecurity risk assessments.
Cybersecurity risk assessment templates are essential for organizations to systematically identify vulnerabilities and security risks, supporting a proactive approach to cyber defense.
Cybersecurity risk assessments are the foundation of a cyber risk management strategy and efficient risk responses. Understanding where the organization stands regarding potential threats and vulnerabilities specific to the enterprise’s information systems and critical assets is essential. These templates help organizations create structured processes and documentation for risk management, enabling systematic evaluation of security risks and compliance needs to ensure alignment with regulatory and industry standards. Vulnerability assessments, both as a baselining method and as a means to track risk mitigation, guide both the security strategy and, as we’re starting to see, the strategy for the enterprise as a whole by evaluating the effectiveness of security measures and controls.
Deciding on a framework to guide the data protection and risk management process to conduct this critical function can seem daunting. Organizations can choose from various industry-standard cyber risk assessment templates depending on their compliance needs and specific cybersecurity objectives. However, we’ll dive into the top cyber security risk assessment models your organization can leverage to ensure that this process aligns with your business operations and helps you proactively assess cyber threats.
Understanding Cybersecurity Risks
Cybersecurity risks are an ever-present challenge for organizations, regardless of size or industry. These risks can lead to the compromise of sensitive data, disrupt essential business operations, and inflict lasting reputational damage. Effectively managing cybersecurity risks begins with a clear understanding of the specific threats and vulnerabilities facing your organization. Cybersecurity risk assessment templates are essential tools that enable organizations to systematically identify, analyze, and manage these risks. By leveraging these templates, businesses can conduct comprehensive risk assessments, prioritize vulnerabilities based on their potential impact, and allocate resources to address the most critical vulnerabilities first. Regular risk assessments are vital for maintaining business continuity, meeting compliance requirements, and staying ahead of emerging threats.
Ultimately, using risk assessment templates empowers organizations to proactively protect their data, streamline risk management processes, and ensure that their cybersecurity strategies are both effective and adaptable to the evolving threat landscape.
Cyber Security Risk Assessment Templates
What most people think of when they hear “template” is almost incongruous with the notion of risk. What caused the shift from compliance-based to risk-focused cybersecurity project management was the need for a more tailored approach to treating risks, identified risks, and potential impacts specific to the organization the governing body may not have considered that that created the compliance requirement. NIST frameworks are widely recognized as guiding standards for developing risk assessment templates, supporting compliance, and integrating best practices into vendor risk management processes. Additionally, clearly defining responsibilities within the risk management process is essential to ensure accountability and streamline risk mitigation efforts.
However, there is good news. Many gold-standard frameworks that organizations already have in place or are working to adopt include guidance to assess the impact, likelihood, and severity of risk to the organization as it relates to cyber and IT.
CIS Risk Assessment Method (RAM)
The Center for Internet Security (CIS) is a leading cybersecurity research organization responsible for creating the popular CIS Top 20 Security Controls. HALOCK Security Labs initially developed the CIS Risk Assessment Method, after which HALOCK approached CIS to make the framework more widely available. Version 1.0 of the CIS RAM was published in 2018. The CIS RAM leverages other industry standards from the National Institute of Standards and Technology (NIST) and the International Organization for Standardization (ISO), which have their own risk assessment program template that we will touch on in this article.
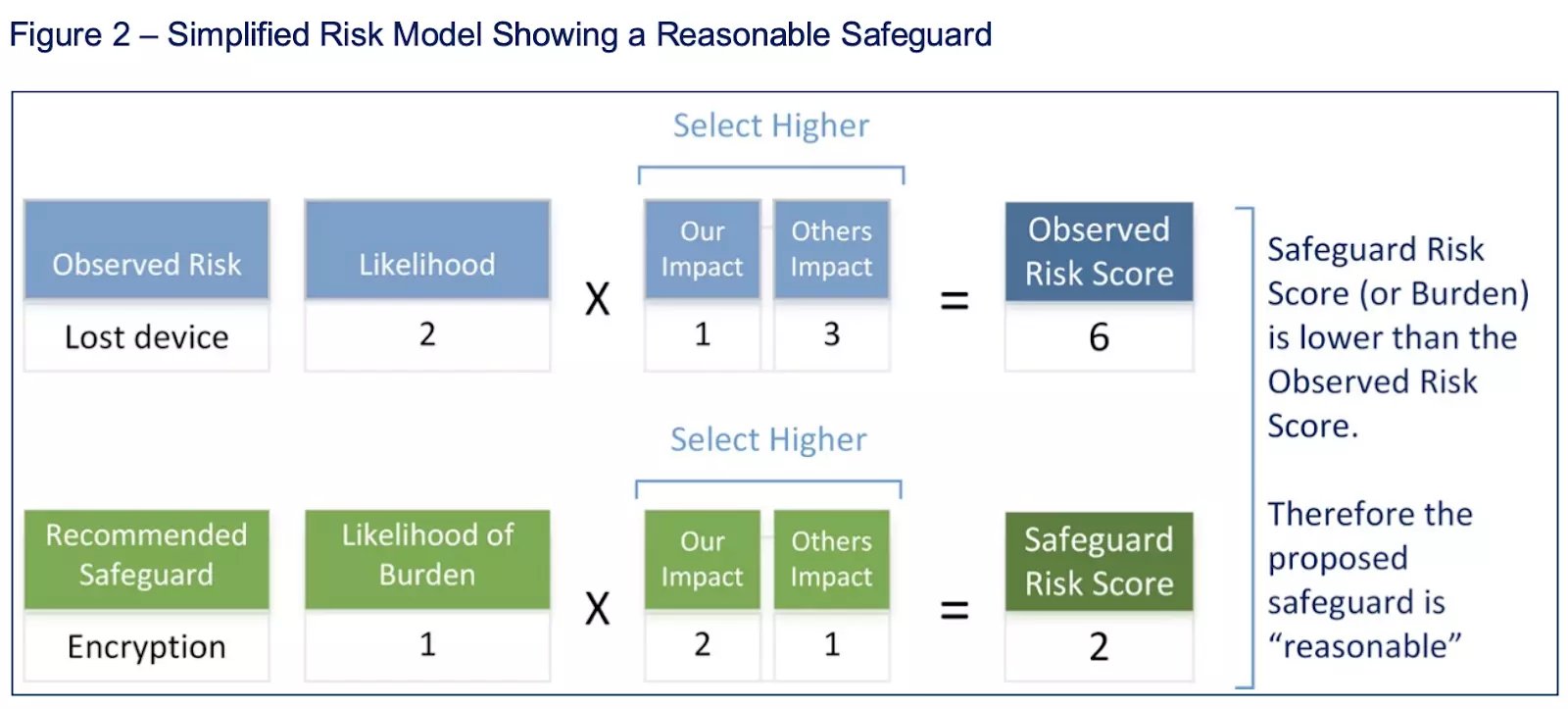
Based on the Duty of Care Risk Analysis (DOCRA), which many regulatory bodies rely on to ensure that organizations deliver reasonable cyber risk management plan templates to protect their customers and vendors, the CIS RAM aligns with the CIS Controls. CIS Risk Assessment Method (CIS RAM) is a widely adopted template that helps gauge the effectiveness of cybersecurity programs. The CIS RAM also helps organizations prioritize security investments by aligning safeguards and controls with business objectives and risk tolerance.
The CIS RAM uses a tiered method to reduce risk based on the organization’s goals and maturity. Again, the CIS RAM tiers align with implementation tiers in other frameworks (e.g., the NIST CSF Implementation Tiers). If your organization leverages the CIS Controls, the CIS RAM can be a good fit. However, should your organization rely on frameworks and standards from NIST or ISO, aligning your security threat assessment reporting to their respective project plans might make more sense. Regular audits are essential to ensure the ongoing effectiveness of implemented controls and risk management strategies.
NIST Cybersecurity Framework/Risk Management Framework Risk Assessment
The National Institute of Standards and Technology (NIST) outlined its guidelines for risk assessment processes in Special Publication 800-30. The guidance has been widely applied across industries and company sizes, primarily because the popular NIST Cybersecurity Framework (CSF) recommends SP 800-30 as the risk assessment methodology.
The significant supporting body of work is the value of using NIST SP 800-30 as a cyber risk assessment template. NIST has developed a robust ecosystem of guidance and supporting documentation to guide organizations as regulated as the United States federal government. Still, the guidance has been applied across organizations of all industries and sizes.
Like the CIS RAM, NIST SP 800-30 uses a hierarchical model, but in this case, to indicate the extent to which the risk assessment results inform the organization. Each tier, from one through three, expands to include more organizational stakeholders.
Developed to support the NIST Risk Management Framework and NIST Cybersecurity Framework, SP 800-30 is a management template best suited for organizations that meet standards built from the NIST CSF or other NIST publications (e.g., defense and aerospace organizations, federal organizations, and contractors).
ISO 27000 Risk Assessment Methodology
The International Organization for Standardization (ISO)'s 27000 series documentation for risk management, specifically ISO 27005, supports organizations using ISO's cybersecurity frameworks to build a risk-based cybersecurity program.
As with NIST SP 800-30, using ISO guidance is most beneficial for organizations pursuing or maintaining ISO 27001 certification.
Conducting a Risk Assessment
Conducting a risk assessment is a foundational step in managing cybersecurity risks and safeguarding your organization’s assets. The process begins with identifying potential threats and vulnerabilities that could impact your systems, data, and business operations. Next, organizations evaluate the likelihood of these threats materializing and assess the potential impact on their operations. This evaluation enables the development of appropriate mitigation strategies tailored to the organization’s unique risk profile.
NIST offers comprehensive guidelines and frameworks, such as the NIST CSF, to guide organizations through each stage of the assessment process. These frameworks provide a structured approach to identifying, protecting, detecting, responding to, and recovering from cyber threats. Utilizing risk assessment templates in conjunction with NIST guidelines streamlines the assessment process, making it easier to identify and prioritize vulnerabilities and implement effective mitigation strategies. By following a structured risk assessment process, organizations can ensure that their cybersecurity efforts are both thorough and aligned with industry best practices.
A Cybersecurity Risk Assessment Checklist
-
Conduct an inventory of all hardware, software, data, and other valuable assets to identify critical assets.
-
Define the scope of the assessment by outlining specific systems, departments, or the entire enterprise.
-
Cybersecurity risk assessments should be conducted regularly to account for changes in the IT environment.
-
A risk matrix or heat map can be used to calculate and prioritize risk levels based on likelihood and impact, documented in a risk register.
-
Train employees on cybersecurity best practices. This is a critical component of implementing a risk management plan.
-
Engage with stakeholders during the risk assessment process to ensure alignment with both technical and business objectives.
Choosing the Right Cybersecurity Assessment Approach
Information technology leaders must use the most effective and efficient risk assessment approach to safeguard business continuity. Regulatory frameworks and standards often require an internal audit risk assessment with allusions and recommendations (i.e., PCI DSS). Managing risk so that risk and compliance teams' efforts align is critical. Streamlining the assessment process for both teams ensures a single source of truth for the entire organization and makes risk assessment reporting much easier. A cybersecurity risk register is a centralized record of identified cybersecurity threats that can be managed and tracked for all business units to use within risk treatment plans.
Check out our guide to cyber risk analysis and how it can enhance security and business operations.
Ultimately, alignment and utility are the most critical factors when deciding on a cybersecurity program assessment methodology. As we discussed, ensuring that each risk team member is aligned with your compliance team is essential. In this case, utility means ensuring that your risk and data security teams collect information, so that leaders can effectively use it to make informed decisions and proactively prevent cyberattacks. With more business leaders requiring greater insight into the cybersecurity posture of the enterprise, as well as third-party risk, ensuring that security leaders can be transparent and clear in their reporting is no longer optional.
In the CyberStrong platform, risk and compliance are completely aligned at the control level in real-time, enabling risk and compliance teams to collect data at the same level of granularity in an integrated approach. For more information on the CyberStrong platform or any questions regarding your following cyber risk assessment, please contact us or request a demo.





.png)
.png)
.png)
%201.png)
.png)




