Data is only as good as what you can do with it. In a cybersecurity program our audits and vendor risk assessments are only as good as their ability to empower us to make decisions. Too often, risk and compliance solutions visualize data for the sake of visualization without asking, “What does this mean?” The race to create cybersecurity dashboards that efficiently convey the organization's security posture and empower better decision-making is on.
The CISO must look to a cyber risk management solution and a risk-based approach to compliance. Under a cyber risk management approach, all data collected across business units are aggregated and rolled up under a single platform without the hindrance of modules. With this approach, CISOs can effectively monitor key cybersecurity indicators and KPIs and communicate risk information to board members. A proactive view saves managers time and increases the ability to understand the organization's security posture on one security risk dashboard.
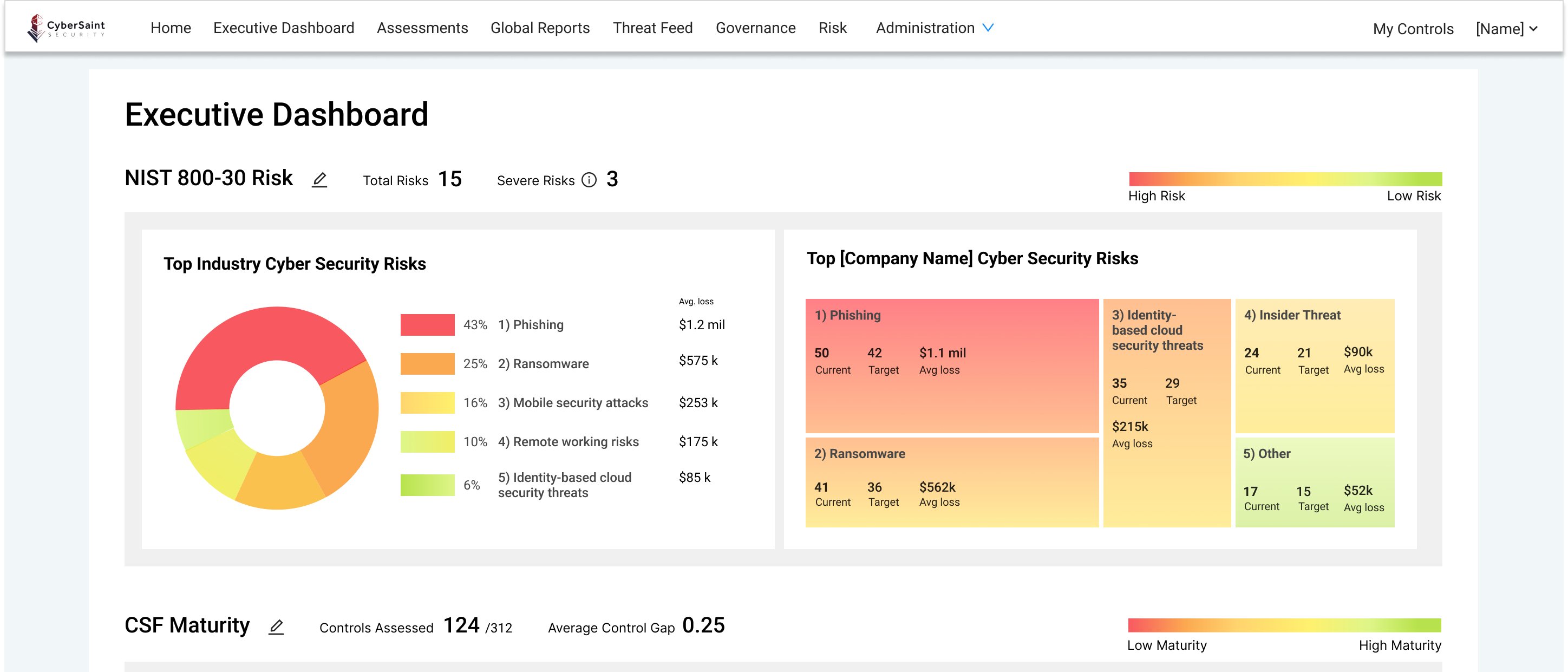
The Value Of An Information Security Executive Dashboard
More often than not, CISOs and their top lieutenants spend incredible amounts of time analyzing the decision-making and performance of their cybersecurity program and need a fast way to measure progress from a high level and reach a common understanding - enter the Executive Dashboard. Sitting a layer of abstraction above the assessment level, a CISO dashboard allows senior security operation program leaders to analyze risk levels in real-time and the posture without getting lost in the details and granular data.
Top Cyber Security Metrics
Elegant user experiences, such as the traffic light protocol, use color coding to convey information quickly. For information security executives, this is critical - it allows users to see where the program is weakest and varying levels of risk based on assessment, and immediately directs them to where they need to invest more resources.
Different Lenses, Different Values
After implementing an integrated cyber risk management solution, almost all program data is in one place, meaning cybersecurity dashboards illustrate the same data only through different visualizations. In the case of a security risk dashboard, breaking the cyber risk data down into the top industry risks, cyber risk by business impact, and risk by threat type gives immediate visibility into the most significant risks to the organization from a high level. These can be broken down further into cybersecurity risk assessment reports that can guide risk mitigation activities.
Risk Assessment Dashboard Example
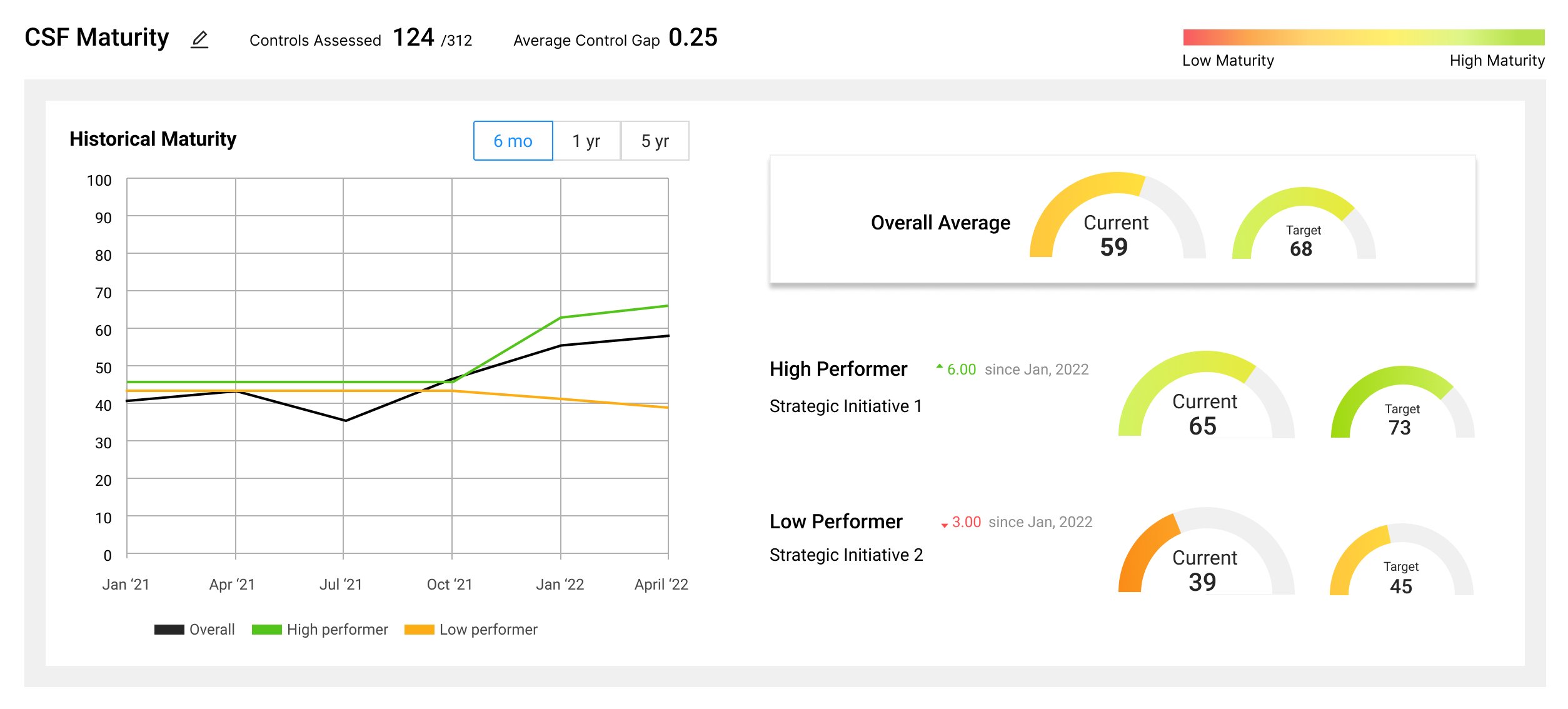
While an executive dashboard is valuable in that it gives a high-level overview of a program, another layer of granularity sits between that high level and the controls: the assessment rollup. For an assessment-level dashboard to be of value, it must be able to illustrate where your organization sits in the context of that assessment when benchmarked against where you should be.
Measure Your Cybersecurity KPIs
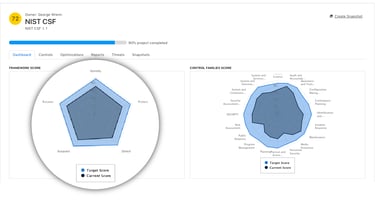
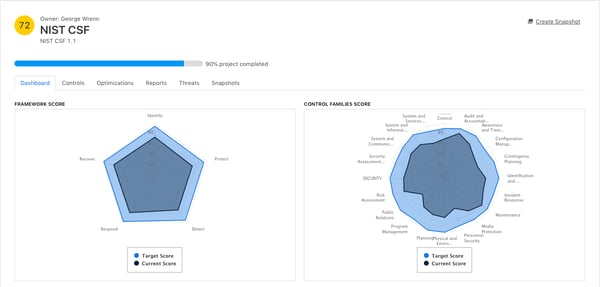
For a mature cybersecurity program, it is paramount to benchmark against security frameworks to ensure that the organization is secure as it grows - the NIST Cybersecurity Framework is the recommended gold standard as it grants the flexibility to grow and scale with your organization and as the landscape shifts. An added bonus is being able to benchmark any assessment against a gold standard like the NIST CSF, and in the case of the CyberStrong platform, it does. Like a NIST dashboard, the five functions appear on every assessment dashboard regardless of the framework you’re working with.
Gap Analysis Visualization 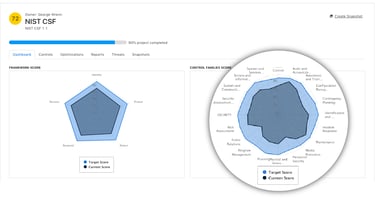
The core reason to conduct audits and assess vendor risks is to understand the gaps in your organization. The faster you and your security team can grasp potential security issues, gaps, and cyber threats in your program, the faster you can work to remediate them. The superior cybersecurity dashboards illustrate that information is provided as expeditiously as possible.
Templates of Cybersecurity Risk Dashboards
An assessment-level cybersecurity dashboard must also reflect risk information related to that assessment and that framework. A cybersecurity risk dashboard that adds a risk breakdown by control family gives more profound insight. Coupled with gap analysis and gold-standard benchmarking, it empowers leaders to make faster data-informed decisions supported by security risk data.
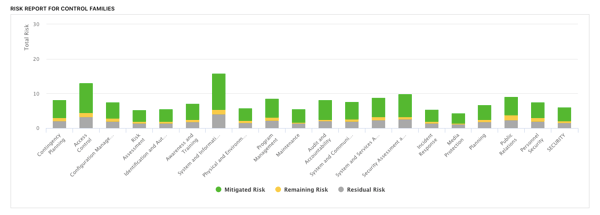
Assessing The Cybersecurity Dashboard Examples
There is a flawed argument in the risk and compliance space today that a complex program needs a complex solution. To those who argue for a complex legacy GRC solution, we’d ask: What are you paying for, then? In a time when automation is rampant, expecting a tool not to make things simpler and more accessible is ludicrous. If anything, a complex cybersecurity program needs technologies that improve decision-making by uniting and integrating the pieces into a greater whole. Especially for organizations with a newly matured cybersecurity program, jumping from spreadsheets to a cyber risk management platform helps build the cybersecurity program of the future.
For a cyber risk management plan to thrive and for the assessment processes to be effective, the tools you use must turn the data collected into actionable insights. The faster the information is conveyed - the risk profile and potential impact specifically - the faster you can remediate data breaches and stay secure.
See also: What is a Cybersecurity Dashboard?





.png)
.png)
.png)
%201.png)
.png)