Given the rollout of regulations such as the SEC Cybersecurity Rule and updates to the NIST Cybersecurity Framework, governance and Board communication are rightly recognized as important in cybersecurity. At the same time, rapid AI adoption, cloud expansion, and increasing third-party interconnectivity have significantly expanded the enterprise attack surface, elevating both operational and regulatory risk.
A CISO is responsible for several cyber risk operations, and transparent communication with stakeholders and the Board is now more critical than ever. CISOs and security leaders must build regular rapport with leadership to align security operations with business objectives, support responsible innovation, and maintain executive buy-in amid accelerated digital transformation.
Part of establishing communication between cyber and business is centralizing and translating cyber risk data into easy-to-understand visualizations in business terms. A CISO board report can be vastly improved with a cybersecurity dashboard that condenses the most critical technical information and delivers data-backed insights to drive decision-making.
While several dashboards are available on the market, we’ll dive into the essential features, explore different types of dashboards, and equip you with the knowledge to make a confident choice. This blog will be your lighthouse, illuminating the path to the best dashboard for CISOs to deliver cybersecurity metrics.
Understanding the Types of Cyber Security Dashboards
To begin our journey, let's understand the different types of cybersecurity dashboards, each catering to a specific audience.
Executive Dashboards:
Executive dashboards serve as the bridge between technical cyber data and strategic decision-making at the highest levels of an organization. They provide a birds-eye view of the cyber landscape, akin to a panoramic view of the ocean from the captain's deck. Just as a captain needs to assess overall sea conditions, executives need to instantly understand the organization's cyber risk posture and critical metrics. These executive cybersecurity dashboards offer simplified, high-level insights into the organization's security posture, highlighting critical areas of concern and trends. Imagine standing on the deck of a ship and seeing the entire ocean laid out before you, allowing leaders to grasp the organization's security landscape at a glance. With this comprehensive view, executives can make informed decisions and allocate resources effectively to mitigate risks and protect the organization from cyber threats.
What Should an Executive Dashboard Include?
At the board level, dashboards should focus on business-impacting metrics — not technical noise. This often includes incident trends over time, third-party risk exposure, vulnerability remediation performance, control coverage against frameworks, and overall risk trajectory. The goal is to answer one core question: Are we getting more secure or less secure — and what does that mean for the business?
Security Operations Dashboards:
Much like a detailed nautical chart with real-time weather updates and enemy ship sightings, these dashboards offer a comprehensive view of the organization's security posture. They consolidate data from various sources, including network logs, intrusion detection systems, and threat intelligence feeds, to provide actionable insights into potential threats and vulnerabilities. Security teams can track incidents as they unfold, investigate alerts, and coordinate response efforts efficiently. These dashboards enable security teams to navigate through the vast sea of data, identify emerging threats, and respond swiftly to mitigate risks.
What Do Security Operations Dashboards Track?
Strong operational dashboards distinguish between lagging indicators (such as incidents and breaches) and leading indicators (such as patch cadence, control effectiveness, and third-party risk posture). While lagging indicators show what has already happened, leading indicators help security teams prevent future incidents — giving leadership confidence that risks are being proactively managed.
Compliance Dashboards:
Compliance dashboards are the compass for ensuring that organizations adhere to various cybersecurity frameworks and standards. They provide a structured framework for tracking compliance requirements, like a checklist for ensuring a ship meets all safety regulations before setting sail. These dashboards consolidate data on regulatory requirements, policies, and standards, providing clear visibility into compliance status. Organizations can track their progress toward meeting compliance goals, identify gaps or deficiencies, and prioritize remediation efforts accordingly. Alongside general compliance dashboards are compliance KPI dashboards that display Key Performance Indicators (KPIs) related to compliance and security.
Other standard dashboards leveraged by security and risk teams include: data governance dashboards and cyber risk assessment dashboards.
Exploring Essential Features of the Best Dashboards
Now that we know the types of dashboards, let's explore the essential features that make them the best.
Data Visualization: Clear charts, graphs, and visualizations are essential to effective cybersecurity dashboards. These visual representations of data serve as a compass, guiding users through the vast sea of information, much like a treasure map with clear markings and landmarks. Just as a treasure map helps adventurers navigate unknown territory, visualizations should help users navigate complex datasets and understand critical insights at a glance.
Visualizations should be intuitive and easy to interpret, allowing users to quickly identify trends, patterns, and anomalies. For example, interactive graphs can display trends in cyber threats over time, while color-coded heat maps can highlight areas of high risk. By transforming complex data into easily digestible insights, data visualizations empower users to make informed decisions and take proactive measures to protect their organization from cyber threats.
Customization: The best cybersecurity dashboards are highly customizable, allowing users to tailor them to their needs and priorities. Users should have the flexibility to adjust dashboard layouts, add or remove widgets, and configure settings according to their preferences. For example, users may prioritize specific metrics or data sources based on their organization's risk profile or compliance requirements. Customization options should be intuitive and user-friendly, empowering users to create a dashboard that meets their specifications.
Customization enhances usability and relevance by allowing users to tailor the dashboard to their specific needs, ensuring that users can efficiently monitor and manage their organization's security posture.
Actionable Insights: Data is only valuable if it leads to actionable insights and informed decision-making. The best cybersecurity dashboards go beyond simply presenting data—they provide clear guidance on mitigating risks and improving security posture. Dashboards should offer actionable recommendations based on data analysis, empowering users to proactively address security threats and vulnerabilities. If the dashboard identifies a critical security flaw, it should provide step-by-step instructions to remediate the issue and reduce risk exposure.
Additionally, dashboards may offer predictive analytics capabilities, alerting users to potential future threats and recommending preventive measures. By providing actionable insights, cybersecurity dashboards enable CISOs and security leaders to convey the course of action to leaders and effectively respond to security breaches or incidents.
Additional Considerations for Cyber Security Data Visualization
Before committing to a cybersecurity dashboard, several additional factors must be considered to ensure smooth sailing and effective cyber risk management planning.
Integration: Choose a dashboard that seamlessly integrates with your existing security tools and platforms. Integration ensures a cohesive experience across your organization's cybersecurity ecosystem. This integration enables comprehensive visibility and centralized management of security operations, streamlining workflows and improving efficiency. When evaluating dashboard options, prioritize solutions that offer robust integration capabilities and support for a wide range of security technologies and protocols.
Scalability: Your cybersecurity needs will inevitably change as your organization grows and evolves. Therefore, selecting a dashboard that can adapt and scale alongside your organization is crucial. A scalable dashboard can accommodate increased data volumes, growing user bases, and expanding infrastructure without sacrificing performance or functionality. Look for flexible architecture, cloud scalability, and modular design that allow the dashboard to grow and evolve with your organization. By investing in a scalable dashboard, you can future-proof your cybersecurity infrastructure and avoid the need for costly replacements or upgrades down the line.
Vendor Reputation: The vendor behind the dashboard plays a significant role in its reliability, support, and security. Before deciding, research the vendor's track record, reputation for customer support, and security practices. Consider the vendor's approach to security, including their adherence to industry standards, data protection practices, and vulnerability management. A reputable vendor will prioritize security and invest in measures to safeguard your organization's data and assets. By selecting a vendor with a solid reputation, you can mitigate risks and ensure a positive experience with your chosen cybersecurity dashboard.
Additional Considerations for Cyber Security Data Visualization
Automation is increasingly critical to dashboard effectiveness. Manual data aggregation and quarterly reporting cycles cannot keep pace with today’s threat landscape. Dashboards powered by automated integrations and continuous control monitoring provide real-time visibility into posture changes, reducing reporting friction while increasing accuracy and executive confidence.
Examples of the Top Cyber Security Dashboards
Now, let's explore the CyberStrong suite of dashboards, each tailored to meet specific needs.
CyberStrong Executive Dashboard: Providing real-time insights into an organization's cybersecurity posture, this dashboard is perfect for CISOs and executive leaders. It offers visualizations using a traffic light protocol, allowing instant identification of areas needing attention.
The Executive Dashboard distills the most critical cyber risk insights into a single dashboard and is routinely updated so CISOs can confidently report on the latest insights. Additionally, CISOs can use the Executive Dashboard to benchmark the organization against its industry and track maturity over time.
For many boards, context is everything. Benchmarking against industry peers helps executives understand whether their organization’s posture is leading, lagging, or aligned with market standards. Comparative insights transform dashboards from internal reporting tools into strategic decision-making assets.
Learn more about CyberStrong’s executive capabilities with the Executive Hub.
CyberStrong Governance Dashboard: Ideal for presenting to the board, this dashboard centralizes critical data and provides meaningful visualizations of security posture. It enables seamless communication between security teams and non-technical leaders.
CyberStrong Assessment Dashboard: Visualizing assessment data against gold-standard frameworks like the NIST CSF, this dashboard helps security leaders identify strengths and weaknesses in security posture. It offers actionable insights for remediation and benchmarking against industry standards.
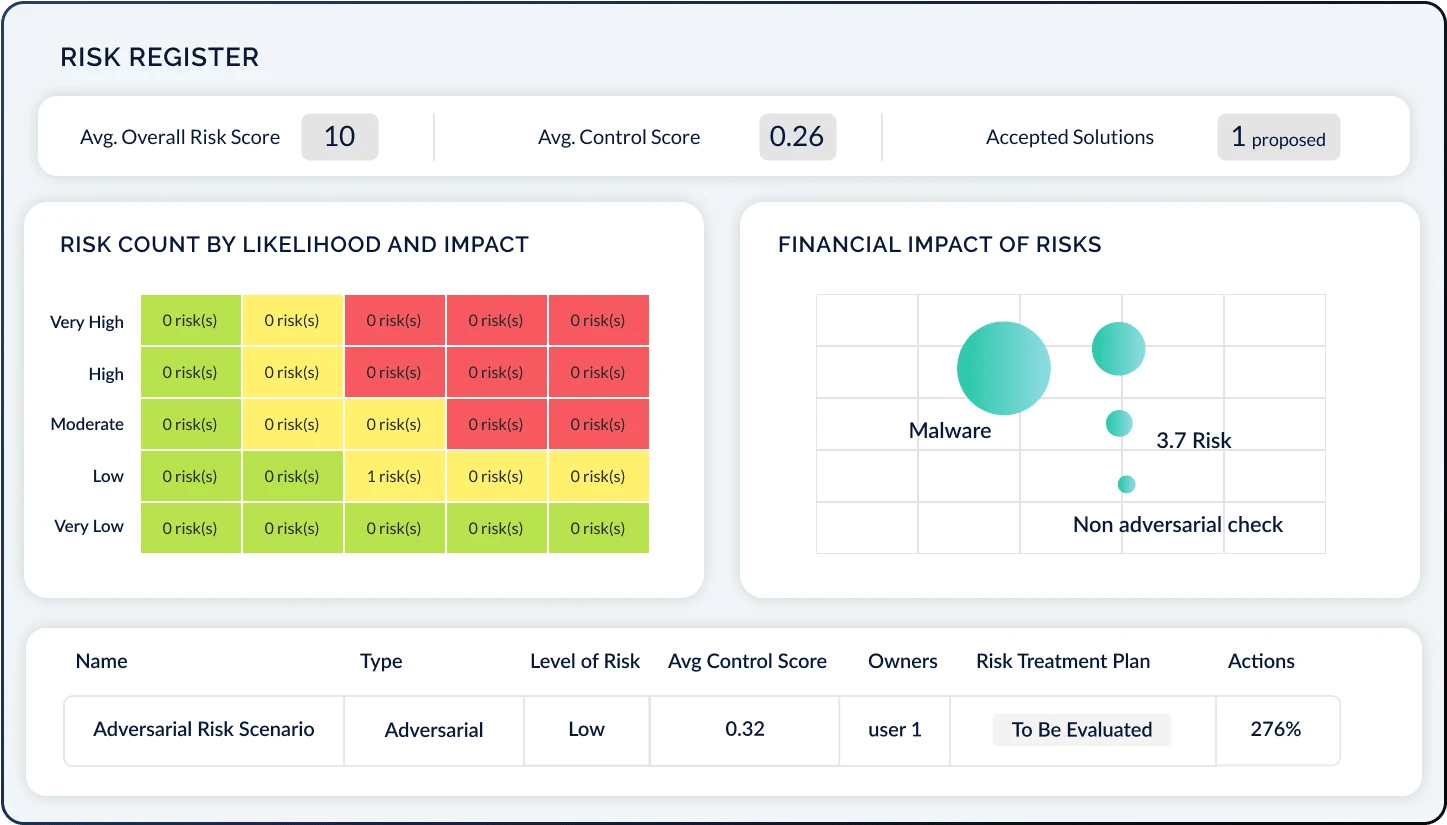
CyberStrong Risk Register: Unlike other risk registers, the CyberStrong Risk Register updates in real-time to accurately reflect compliance and risk data. As control groups are updated and control scores change, risks in the risk register change dynamically. Cyber and IT risk teams can act fast on credible, accurate risk intelligence delivered to the minute. View risk by likelihood and impact, as well as the overall impact on your organization, using cyber risk quantification. CyberStrong allows you to view mitigated, residual, and inherent risks in dynamic ways that spur decision-making and focus.
At the end of our journey, you can identify the best cybersecurity dashboard for your specific needs and priorities, evaluate different dashboards based on their features and functionalities, and decide to guide your organization toward a more secure future. Set sail towards cyber resilience, and contact us today to learn more about our customizable visualization tools and dashboards.
FAQ: How to Choose the Right Cybersecurity Dashboard
Q: Why are cybersecurity dashboards important for CISOs and executive leadership?
Dashboards simplify complex technical data into clear, visual insights that support strategic decisions. They help CISOs communicate cyber risk posture, compliance status, and threat intelligence in terms that business leaders understand.
Q: What’s the difference between executive, operational, and compliance dashboards?
-
Executive dashboards offer high-level overviews for Boards and leadership.
-
Security operations dashboards provide detailed, real-time data for incident response and threat management.
-
Compliance dashboards track adherence to regulatory frameworks and highlight control gaps and KPIs.
Q: What features should I look for in a cybersecurity dashboard?
The most effective dashboards include:
-
Clear data visualizations (e.g., charts, heat maps)
-
Customization to match your priorities
-
Actionable insights that guide decision-making
-
Seamless integration with existing tools
-
Scalability to support growth
-
Vendor trustworthiness for long-term reliability
Q: How does CyberStrong support CISO dashboard needs?
CyberStrong offers dashboards purpose-built for executive reporting, governance alignment, control assessments, and dynamic risk tracking. Each is designed to translate real-time data into meaningful visuals and insights that drive cybersecurity maturity and business alignment.
Q: Can dashboards help with board communication?
Absolutely. Dashboards like CyberStrong’s Governance and Executive Dashboards make it easier to present risk and compliance information to non-technical stakeholders in a visual, digestible format, strengthening trust and transparency at the board level.





.png)
.png)
.png)
%201.png)
.png)